Professional Documents
Culture Documents
Paper 1
Uploaded by
Eric DavisOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Paper 1
Uploaded by
Eric DavisCopyright:
Available Formats
Network Security For Wireless Sensor Network Using Game Theory Approach
V.Vinoba K.N.Government Arts College for Women Thanjavur P.Hema R.M.K. Collgege of Engineering and Technology Puduvoyal-601206 Abstract: In this paper we investigate the impacts of applying game theory on the network throughout and accuracy of malicious node detection to WSN. Currently, the needs of WSN have become inevitable in daily life. With continuous growth of WSN in daily life, business and defence application the security of transfering data from sensors to their destination has become an important research area. In this apaper we discuss currently available intrusion detection technique attack models using game theoryand to detect malicious node using game theory approach for nodes in forward data path. Introduction Game theory provides a mathematical method for analysing and modelling WSN security problems for it considers scenarios where multiple players with contradictory objectives compete with each other. We divide game theory application for WSN security into three categories (i) preventing Denial of service attacks (ii) intrusion detection (iii) coexistence with malicious nodes. In DoS attacks, the attackers objective is to make target destinations inaccessible by legitimate users . A sensor network without sufficient protection from DoS attacks may not be deployable in many areas. Nodes of a sensor network can not be trusted for the correct execution of critical network functions. Nodes misbehavior may range from simple selfishness or lack of collaborationdue to the need for power saving, to active attacks aiming at DoS and subversion of traffic. There are two types ofDoS attacks: Passive attacks: selfish nodes use the network but do not cooperate, saving battery life for their own communications; they do not intend to directly damage other nodes. Active attacks: malicious nodes damage other nodes by causing network outage by partitioning, while saving battery life is not a priority.
The prevention of passive denialof service attack at routing layer in wireless sensor networks as a repeated game between an intrusion detectorand nodes of a sensor network, where some of these nodesact maliciously. We propose a framework to enforce cooperation among nodes and punishment for non-cooperativebehavior. We assume that the rational users optimizetheir profits over time. Intrusion detector residing at the base station keeps track of other nodes collaboration bymonitoring them. If performances are lower than sometrigger thresholds, it means that some nodes act maliciously by deviation. Intrusion detector rates other nodes,which is known as subjective reputation and the positive rating accumulates for each node as it gets rewarded. In WSN, IDSs can be placed on all of nodes to make a network safer. But the always-on Strategy is not an efficient choice because of wasting the source of system. Instrusion detection can be done by using non co-operative game theoretic frame work which can help each cluster head node decide the probability of starting of IDSs service. In the intrusion detection problem, IDS needs toprotect each cluster in the network. Since we are considering one cluster at a time, detection of a malicious node on the path of data flow is very important. We assume that the network is operating under ideal radioconditions. Consequently, packet loss appears due to malicious activity. GAME THEORY BASED APPROACH A.Basics of Game Theory In game theory, the basic assumption is that the decision makers pursue some well defined objectives and take into account their knowledge or experience of the other decision makers behavior. In this research, we analyze the existing system as game and study the properties of game. We define the game G as =(N,A, {ui}), where Nis the finite set of players, action game theory. Rational players are assumed to maximize their payoff, which is a selfish motivation. In game theory, the solution of a game is the outcome. In WSN, the IDS plays as one player and intruder plays as opponent. In the WSN problem, the large WSN is divided into clusters and IDS defends a cluster at any given time, while the attacker disturbs the normal operations. B. Game Model
Figure 1
Figure 1 is a typical sensor network where data transferis from the sensor nodes (N) to the cluster head with action Ai and outcome ui . In this game model, we consider IDSat cluster head and monitor the data transfer from sensor nodes to cluster head. The attacker may attack any node in the cluster (including cluster head) and the IDS at the cluster head to defend the nodes. The IDS at the cluster head tries to maintain the normal functionality of the network by reventing the attacks while the attacker tries to disturb the network. This functionality will continue at all cluster heads as well as at the base station. Definition 1: An outcome of a game is Pareto optimal if there is no other outcome that makes every player at least as well off and at least one player strictly better off. Theorem 1: A zero sum game is not a Pareto optimal. Proof: If a change from one allocation to another can make at least one individual better off without making any other individual worse off, then it is called a Pareto improvement. An allocation is Pareto efficient or Pareto optimal when no further Pareto improvements can be made. This is often Pareto optimal. Definition 2: If the zero sum game is Pareto optimal then it is called a conflict game. In a conflict game, none of the players benefit. The game leads nowhere. Therefore, it is suggested to design an IDs to play a conflict game, so that the intruder never wins and no node compromises distraction or diversion. Definition 3: In a zero sum game the cost of attack on a node is equal to the cost to defend a node. This leads, the profit of an attack to the intruder equals the loss to the sensor network (loss may a cluster). Theorem 2: A zero sum game has no pure Nash Equilibrium. Proof: In pure strategy NE, when each players output maximizes its profits given the output of other player. Definition 4. The IDS defends many times for all intruder attacks. For a zero sum game, the cost of the intruders success and failure attacks equals the cost of success and failures of defending the nodes. To get a successful attack, an intruder must attack a number of times unsuccessfully. The waiting time for unsuccessful attacks is added to successful attacks of the intruder cost. The profit of the attacker depends upon the number of nodes compromised, but the total cost or energy used by the intruder to compromise the cluster nodes is the sum of the successful and failure attempts. Theorem 3: In zero sum game, the energy used to defend a cluster is finite. C. Detection of malicious node In the intrusion detection problem, IDS needs to protect each cluster in the network. Since we are considering one cluster at a time, detection of a malicious node on the path of data flow is
very important. m of which are malicious. Let there be q (=1) nonmalicious nodes between every two malicious nodes. Let be the number of selected acknowledgement points (A and E) in the packet path and be the percent of nodes which are randomly selected as check points. Let us consider the path SABCDEF BS in Figure 2, where D is a malicious node. Let A and E be the selected acknowledge points ( =2). The following are the possibilities: Any node in the path is malicious (compromised with an intruder) One or more of the nodes (for example B ) are malicious (before or between the acknowledge points) Node A or node E is malicious (assume that selected acknowledgement points are not malicious)
Figure 2 With the help of above theorems and definitions we can find the number of malicious node In the forwarding path. Here IDSs and intruders are non co-operative players. The intruder maximizes its benefits by destroying the functionality of the system and the protector tries to protect the facility. In this research, our problem is to detect malicious node in the forward path. CONCLUSIONS The random check points are selected to detect the malicious node in the communications path using zero sum game. The zero sum game presented in the current model shows the total energy required is constant.
You might also like
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (588)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Probability and Queueing Theory SyllabusDocument2 pagesProbability and Queueing Theory SyllabusEric DavisNo ratings yet
- Fish (Plural: Fish or Fishes) AreDocument4 pagesFish (Plural: Fish or Fishes) AreEric DavisNo ratings yet
- Probability and Queueing Theory SyllabusDocument2 pagesProbability and Queueing Theory SyllabusEric DavisNo ratings yet
- Predicates 3Document6 pagesPredicates 3Eric DavisNo ratings yet
- R.M.K College of Engineering and Technology: Test AnalysisDocument22 pagesR.M.K College of Engineering and Technology: Test AnalysisEric DavisNo ratings yet
- Test 2-NMDocument2 pagesTest 2-NMEric DavisNo ratings yet
- Galois Theory ImportantDocument66 pagesGalois Theory ImportantEric DavisNo ratings yet
- Chapter 5 Introduction To Factorial DesignsDocument28 pagesChapter 5 Introduction To Factorial DesignsEric DavisNo ratings yet
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5795)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (345)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (400)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (74)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1091)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (121)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Kcse 2019 Prediction-All PDFDocument220 pagesKcse 2019 Prediction-All PDFBadmind JnrNo ratings yet
- Modeling and Simulation of A Spray Column For NOx AbsorptionDocument15 pagesModeling and Simulation of A Spray Column For NOx AbsorptionAnel MamaniNo ratings yet
- Design of Pressure Vessels Under ASME Section VIIIDocument122 pagesDesign of Pressure Vessels Under ASME Section VIIIAnonymous d23gWCRQNo ratings yet
- NEURAL NETWORKS - Prediction of Admission in Pediatric Emergency DepartmentDocument8 pagesNEURAL NETWORKS - Prediction of Admission in Pediatric Emergency DepartmentGabriel Hora SáNo ratings yet
- CH 17Document68 pagesCH 17Ignacio MagañaNo ratings yet
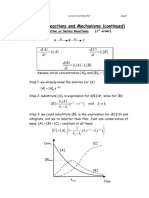
- Consecutive, Series, and Reversible ReactionsDocument6 pagesConsecutive, Series, and Reversible ReactionsRojo JohnNo ratings yet
- Web Traffic Time Series Forecasting: Kaggle Competition Review Bill Tubbs July 26, 2018Document39 pagesWeb Traffic Time Series Forecasting: Kaggle Competition Review Bill Tubbs July 26, 2018do minh tienNo ratings yet
- Geophysical Signal AnalysisDocument481 pagesGeophysical Signal AnalysisDimas Pradana100% (1)
- CE50P-2: Numerical Solution To Engineering ProblemsDocument21 pagesCE50P-2: Numerical Solution To Engineering ProblemshgfhfghfghgNo ratings yet
- Clean Code: A Handbook of Agile Software CraftsmanshipDocument8 pagesClean Code: A Handbook of Agile Software CraftsmanshipJack MaloneyNo ratings yet
- Data Science Is New-Age Astrology: Astrology and Machine LearningDocument6 pagesData Science Is New-Age Astrology: Astrology and Machine LearningRtdfAbNo ratings yet
- TestDocument126 pagesTestGar LewisNo ratings yet
- Updation After ENVI5.0Document36 pagesUpdation After ENVI5.0Vijay KumarNo ratings yet
- SpeedDocument21 pagesSpeeddrexelNo ratings yet
- North Sydney Boys 2015 Year 10 Maths Yearly & SolutionsDocument14 pagesNorth Sydney Boys 2015 Year 10 Maths Yearly & SolutionsAditiPriyankaNo ratings yet
- Curve and SurfacesDocument28 pagesCurve and SurfacesAnonymous u87aqFoNo ratings yet
- BTS3900 V100R009C00SPC150 (ENodeB) Performance Counter ListDocument321 pagesBTS3900 V100R009C00SPC150 (ENodeB) Performance Counter Listvikas_bhardwaj301No ratings yet
- Lesson 9: Coulomb's Law: Charles Augustin de CoulombDocument7 pagesLesson 9: Coulomb's Law: Charles Augustin de Coulombanaklembah@ScribdNo ratings yet
- Tugas English For Math 01Document4 pagesTugas English For Math 01Danny KusumaNo ratings yet
- 96812e6cf4fb89fb149a7ea47216c988Document6 pages96812e6cf4fb89fb149a7ea47216c988Erick NuescaNo ratings yet
- 2018FA MAT152 Test2AKEY 1Document6 pages2018FA MAT152 Test2AKEY 18987a&mNo ratings yet
- Commutators in Quantum Mechanics PDFDocument2 pagesCommutators in Quantum Mechanics PDFIsraelNo ratings yet
- Ged 102 Exercise 3 Module 1 1Q 2021-2022Document3 pagesGed 102 Exercise 3 Module 1 1Q 2021-2022DES MOSNo ratings yet
- AMCAT Automata QuestionsDocument35 pagesAMCAT Automata QuestionsSarvasaisrinathNo ratings yet
- Revision WorksheetDocument17 pagesRevision WorksheetJumana ElkhateebNo ratings yet
- 2nd Quaarter ExamDocument2 pages2nd Quaarter ExamJoana Marie DeontoyNo ratings yet
- Laterally Unrestrained BeamsDocument12 pagesLaterally Unrestrained BeamsVikram0% (1)
- Write A Program To Obtain The Topological Ordering of Vertices in A Given DigraphDocument11 pagesWrite A Program To Obtain The Topological Ordering of Vertices in A Given DigraphGuru GuruNo ratings yet
- False Data Injection Attacks On LFC Systems An AI-Based Detection and Countermeasure StrategyDocument9 pagesFalse Data Injection Attacks On LFC Systems An AI-Based Detection and Countermeasure StrategyAmar IndraNo ratings yet
- Dressing TabulateDocument9 pagesDressing Tabulatenishu_aminNo ratings yet