Professional Documents
Culture Documents
At Any Time Wonder The History of Protected Calls or How To Encrypt Voice Calls.20140316.042015
Uploaded by
teller5crossOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
At Any Time Wonder The History of Protected Calls or How To Encrypt Voice Calls.20140316.042015
Uploaded by
teller5crossCopyright:
Available Formats
Ever ponder the history of secure phone calls or how to encrypt voice calls
With SIGSALY, ten channels had been utilized to sample the voice frequency spectrum from 250 Hz to 3 kHz and two channels had been allotted to sample voice pitch and background hiss. In the time of SIGSALY, the transistor experienced not been produced and the digital sampling was carried out by circuits making use of the model 2051 Thyratron vacuum tube. Every SIGSALY terminal employed forty racks of equipment weighing 55 tons and loaded a massive area. This tools provided radio transmitters and receivers and big phonograph turntables. The voice was keyed to two sixteen-inch vinyl phonograph information that contained a Frequency Change Keying (FSK) audio tone. The records have been played on big exact turntables in synch with the voice transmission.[one] From the introduction of voice encryption to these days, encryption tactics have developed dramatically. Electronic engineering has properly replaced outdated analog strategies of voice encryption and by employing intricate algorithms, voice encryption has turn out to be a lot far more protected and productive. A single relatively modern voice encryption strategy is Sub-band coding. With Sub-band Coding, the voice sign is split into numerous frequency bands, utilizing several bandpass filters that include particular frequency ranges of fascination. The output alerts from the bandpass filters are then lowpass translated to decrease the bandwidth, which minimizes the sampling charge. The lowpass indicators are then quantized and encoded making use of unique tactics like, Pulse Code Modulation (PCM). Following the encoding phase, the alerts are multiplexed and despatched out alongside the interaction community. When the signal reaches the receiver, the inverse functions are used to the sign to get it back again to its authentic state.[two] Motorola designed a voice encryption system named Digital Voice Security (DVP) as part of their very first technology of voice encryption strategies. DVP makes use of a self-synchronizing encryption method identified as cipher comments (CFB). The basic DVP algorithm is able of 2.36 x 1021 different "keys" based on a important size of 32 bits."[three] The extremely high quantity of achievable keys related with the early DVP algorithm, can make the algorithm very strong and presents a higher degree of secur Digital A electronic protected voice normally involves two factors, a digitizer to change in between speech and electronic signals and an encryption program to offer confidentiality. What helps make ciphony hard in exercise is a want to send the encrypted sign more than the same voiceband interaction circuits employed to transmit unencrypted voice, e.g. analog telephone strains or cell radios. This has led to the use of Voice Coders (vocoders) to achieve tight bandwidth compression of the speech alerts. NSA's STU-III, KY-fifty seven and SCIP are illustrations of methods that work more than current voice circuits. The STE technique, by contrast, calls for vast
bandwidth ISDN traces for its normal manner of procedure. For encrypting GSM and VoIP, which are electronic anyway, the standard protocol ZRTP could be utilized as an concludeto-finish encryption technologies. Safe voice's robustness tremendously rewards from obtaining the voice information compressed into extremely minimal little bit-charges by special part named speech coding, voice compression or voice coder (also recognized as vocoder). The outdated safe voice compression requirements incorporate (CVSD, CELP, LPC-10e and MELP, where the latest standard is the state of the artwork MELPe algorithm. encrypt voice calls, encrypt voice calls, encrypt voice calls
You might also like
- Q1Document4 pagesQ1Aviratna Kumar100% (5)
- BU275-2021-Spring Course OutlineDocument6 pagesBU275-2021-Spring Course OutlineRichard MaNo ratings yet
- Connected Leader - Module 1Document22 pagesConnected Leader - Module 1api-670274155No ratings yet
- Ajp - 3.14 Joint ProtectionDocument78 pagesAjp - 3.14 Joint Protectionghoster33100% (1)
- THE Increasing Relevance of Multimedia Applications Is Placing A Great Demand On ContentDocument17 pagesTHE Increasing Relevance of Multimedia Applications Is Placing A Great Demand On ContentShyam SundarNo ratings yet
- Digital Audio Broadcasting 8320 V1xMLeiDocument22 pagesDigital Audio Broadcasting 8320 V1xMLeiDandy KelvinNo ratings yet
- VOIPDocument79 pagesVOIPKhalid Khalifa AtyaNo ratings yet
- Digital Audio Broadcasting Full Seminar ReportDocument23 pagesDigital Audio Broadcasting Full Seminar Reportbindug167% (3)
- Digital Audio BroadcastingDocument14 pagesDigital Audio Broadcastingbindug1100% (1)
- What Is MPEGDocument5 pagesWhat Is MPEGARTMehr Eng. GroupNo ratings yet
- CcnavoiceDocument43 pagesCcnavoiceGoutham Baratam50% (2)
- AstroDocument41 pagesAstroAhmed Hamed BadrNo ratings yet
- Ee 3700 Digital Comm SystemsDocument33 pagesEe 3700 Digital Comm SystemsnishnagiNo ratings yet
- 1 5 Analog To Digital Voice EncodingDocument10 pages1 5 Analog To Digital Voice EncodingDương Thế CườngNo ratings yet
- I DenDocument34 pagesI DenGajendra SettyNo ratings yet
- Echo Cancellation in IP NetworksDocument26 pagesEcho Cancellation in IP NetworksRuthvik ReddyNo ratings yet
- Wideband Voice Coding - Opportunities and Implementation ChallengesDocument6 pagesWideband Voice Coding - Opportunities and Implementation ChallengeshoainamcomitNo ratings yet
- Presented by Nithin RajDocument26 pagesPresented by Nithin Rajh_akbarshariffNo ratings yet
- IIIIDocument46 pagesIIIIkhasimNo ratings yet
- Application of Digital Signal Processing in Radio Transmitter, CDMA, GSM, Optical Fiber, DTH CommunicationDocument3 pagesApplication of Digital Signal Processing in Radio Transmitter, CDMA, GSM, Optical Fiber, DTH Communicationramjee26No ratings yet
- 4g TechDocument24 pages4g TechMahesh MoreNo ratings yet
- Digital Over Analog Signal ProcessingDocument2 pagesDigital Over Analog Signal ProcessingHayeon Lee100% (1)
- Mobile Computing Through TelephonyDocument65 pagesMobile Computing Through TelephonyPrakash Patil100% (10)
- LabviewDocument11 pagesLabviewRameezNo ratings yet
- Introduction To Cdma: Code Division Multiple Access (CDMA) Is A Radically New Concept in WirelessDocument24 pagesIntroduction To Cdma: Code Division Multiple Access (CDMA) Is A Radically New Concept in WirelessMohamed Abdel MonemNo ratings yet
- ONT10S02 Voice Over IPDocument106 pagesONT10S02 Voice Over IPAakash GoelNo ratings yet
- Jeas 0120 8068Document10 pagesJeas 0120 8068FengXuan YangNo ratings yet
- Audio Coding: Basics and State of The ArtDocument6 pagesAudio Coding: Basics and State of The ArtAu Belchez ZamudioNo ratings yet
- Audio Coding: Basics and State of The ArtDocument6 pagesAudio Coding: Basics and State of The ArtAu Belchez ZamudioNo ratings yet
- Report On Advance Telcom TechnologyDocument37 pagesReport On Advance Telcom Technologyvincent GamingNo ratings yet
- Speech Coding: Fundamentals and Applications: ARK Asegawa OhnsonDocument20 pagesSpeech Coding: Fundamentals and Applications: ARK Asegawa OhnsonMohamed TalaatNo ratings yet
- 4g TechnologyDocument16 pages4g Technologyapi-422183469No ratings yet
- What Is 3GDocument15 pagesWhat Is 3GShampad AyanNo ratings yet
- OKOS Paper 2013001 - Advanced Digitizer Technologies and Ultrasonic Scanning Acoustic Microscopy (SAM)Document2 pagesOKOS Paper 2013001 - Advanced Digitizer Technologies and Ultrasonic Scanning Acoustic Microscopy (SAM)Aly-LNo ratings yet
- Chap5 VoIPDocument39 pagesChap5 VoIPMoustapha RachidiNo ratings yet
- Voice Encryption Using DESDocument48 pagesVoice Encryption Using DESVipul SharmaNo ratings yet
- 4G Technology: Presented by Nithin RajDocument26 pages4G Technology: Presented by Nithin RajClaudiu MădălinNo ratings yet
- 4G Technology: Presented by YogenderDocument26 pages4G Technology: Presented by YogenderPawanJainNo ratings yet
- 4g TechnologyDocument31 pages4g TechnologyAbhinav Reddy KalvaNo ratings yet
- Fpga Implementation of Direct Sequence Spread SpectrumDocument29 pagesFpga Implementation of Direct Sequence Spread SpectrumThirumal ArunNo ratings yet
- Reliable Communication: Basics of Error Control CodingDocument4 pagesReliable Communication: Basics of Error Control CodingMusiur Raza AbidiNo ratings yet
- 4G Technology: Presented by Nithin RajDocument26 pages4G Technology: Presented by Nithin RajLucasNo ratings yet
- Voice Over Internet ProtocolDocument5 pagesVoice Over Internet ProtocolNaveen KrishnanNo ratings yet
- Third Generation (3G) Mobile Technology: CSCI 6404Document68 pagesThird Generation (3G) Mobile Technology: CSCI 6404Rishabh RichhariyaNo ratings yet
- Spread SpectrumDocument32 pagesSpread SpectrumLiyana NasarudinNo ratings yet
- Digital Audio Networking in The FieldDocument4 pagesDigital Audio Networking in The FieldEdoardo PacchiottiNo ratings yet
- Data CommunicationDocument114 pagesData CommunicationShikha SharmaNo ratings yet
- Signals Carried Over The NetworkDocument15 pagesSignals Carried Over The NetworkAgma Tinoe MauludyNo ratings yet
- Introduction About Telecom: TelecommunicationDocument29 pagesIntroduction About Telecom: TelecommunicationChandra Prakash BhartiNo ratings yet
- Telephone Network and DSL Technology: U.K.P. Mihiranga (MBA in MOT, B.Sc. Eng. (Hons), PMP-PMI (USA), AMIESL)Document37 pagesTelephone Network and DSL Technology: U.K.P. Mihiranga (MBA in MOT, B.Sc. Eng. (Hons), PMP-PMI (USA), AMIESL)Pathum MihirangaNo ratings yet
- Telephone Exchange IntroductionDocument102 pagesTelephone Exchange IntroductionPankaj kumarNo ratings yet
- Mobile & Wireless Lecture # 1 by Engr. Sajjad KarimDocument21 pagesMobile & Wireless Lecture # 1 by Engr. Sajjad KarimShah Zeb YousafzaiNo ratings yet
- Prepared by Kartikeya Tiwari. 0817EC081030Document20 pagesPrepared by Kartikeya Tiwari. 0817EC081030Sonu TiwariNo ratings yet
- ATA IP Phone: Compression - DecompressionDocument8 pagesATA IP Phone: Compression - Decompressionabhia16No ratings yet
- Principles of Electronic Communication Systems: Second EditionDocument60 pagesPrinciples of Electronic Communication Systems: Second EditionThiruGovindNo ratings yet
- Waveform CodingDocument7 pagesWaveform Codingapi-19663123No ratings yet
- 1-Digital Comm.Document15 pages1-Digital Comm.عقيل سعدNo ratings yet
- Digital AM and FM BroadcastingDocument47 pagesDigital AM and FM BroadcastingHans Christian Macasa100% (1)
- Cdma DsssDocument6 pagesCdma DsssSh Re SuNo ratings yet
- Analog To Digital ConversionDocument37 pagesAnalog To Digital ConversionSharanya VaidyanathNo ratings yet
- Colour Banding: Exploring the Depths of Computer Vision: Unraveling the Mystery of Colour BandingFrom EverandColour Banding: Exploring the Depths of Computer Vision: Unraveling the Mystery of Colour BandingNo ratings yet
- Prakt 8 - Openssl Demo Encrypting Decrypting Files Using Both Symmetric and Asymmetric Encryption PDFDocument6 pagesPrakt 8 - Openssl Demo Encrypting Decrypting Files Using Both Symmetric and Asymmetric Encryption PDFAbiyau NeoNo ratings yet
- Berhanemeskel Reda PDF Anti Communism Far Left PoliticsDocument1 pageBerhanemeskel Reda PDF Anti Communism Far Left PoliticsAlula AbrahaNo ratings yet
- 50 Number Series (Gradeup)Document12 pages50 Number Series (Gradeup)VamsiKrishnaNo ratings yet
- EPSTPLOGDocument6 pagesEPSTPLOGAbbes BelhaniNo ratings yet
- Course Syllabus - QMT181 - June - 2016 - Latest PDFDocument2 pagesCourse Syllabus - QMT181 - June - 2016 - Latest PDFadamNo ratings yet
- Cisco ExamDocument109 pagesCisco ExamBart WetzelsNo ratings yet
- ASN1Document15 pagesASN1hari423No ratings yet
- FXD RecloserControl v2 Color2Document16 pagesFXD RecloserControl v2 Color2erty ertyuNo ratings yet
- Cybersecurity and The Critical Infrastructure Looking Beyond The PerimeterDocument5 pagesCybersecurity and The Critical Infrastructure Looking Beyond The PerimeterEsteban Miranda NavarroNo ratings yet
- OtisDocument3 pagesOtisscarivinNo ratings yet
- Format of Lab ReportDocument3 pagesFormat of Lab ReportNirbhayNo ratings yet
- How Is The Loyalty Batch EngineDocument5 pagesHow Is The Loyalty Batch EnginessbnirmaNo ratings yet
- Samsung Group: By: Ethel Herna C. PabitoDocument13 pagesSamsung Group: By: Ethel Herna C. PabitoEthel PabitoNo ratings yet
- Linux Essential A 2 4Document28 pagesLinux Essential A 2 4Robin LiNo ratings yet
- M750 Service ManualDocument78 pagesM750 Service ManualcciprainNo ratings yet
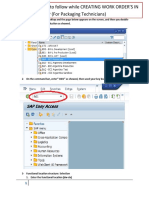
- Creating WO SOP and Teko in SapDocument10 pagesCreating WO SOP and Teko in SapGeorge AgafinaNo ratings yet
- Software Engineering II - CS605 Spring 2009 Assignment 01 SolutionDocument2 pagesSoftware Engineering II - CS605 Spring 2009 Assignment 01 SolutionnnoumanNo ratings yet
- 1) Develop An Application That Uses GUI Components, Fonts and ColorsDocument56 pages1) Develop An Application That Uses GUI Components, Fonts and ColorsKirti AroraNo ratings yet
- 990k HidraulicDocument15 pages990k Hidraulichitler morales gavidiaNo ratings yet
- Lab Report No 10ADCDocument4 pagesLab Report No 10ADCIhsan ul HaqNo ratings yet
- 3G Direct Tunnel ConfigurationDocument23 pages3G Direct Tunnel ConfigurationSNOC3 TeamNo ratings yet
- Sap Hana and TableauDocument6 pagesSap Hana and Tableauusd30547100% (1)
- 802 Information Technology Sqp2019-2020Document5 pages802 Information Technology Sqp2019-2020aespamaoNo ratings yet
- Click Fraud Detection: Adversarial Pattern Recognition Over 5 Years at MicrosoftDocument21 pagesClick Fraud Detection: Adversarial Pattern Recognition Over 5 Years at MicrosoftBhakti RaneNo ratings yet
- How To Learn From GATE Applied Course - TOCDocument1 pageHow To Learn From GATE Applied Course - TOCrythgngNo ratings yet
- Common Services Portal: Digital Gujarat Portal - Citizen User ManualDocument26 pagesCommon Services Portal: Digital Gujarat Portal - Citizen User ManualrahukNo ratings yet