Professional Documents
Culture Documents
Installing Backtrack 5 R1 in Virtual Machine
Uploaded by
vijay_7860 ratings0% found this document useful (0 votes)
40 views44 pageswireless security notes
Original Title
Security
Copyright
© © All Rights Reserved
Available Formats
DOCX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this Documentwireless security notes
Copyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
40 views44 pagesInstalling Backtrack 5 R1 in Virtual Machine
Uploaded by
vijay_786wireless security notes
Copyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
You are on page 1of 44
LAB 1: Installing BackTrack 5 R1 in Virtual Machine
OBJECTIVE: To install BackTrack 5 R1 in Vmware
REQUIREMENTS
Computer
Vmware
BackTrack 5 R1 iso file
STEPS
Be sure that you have Vmware installed on your system.
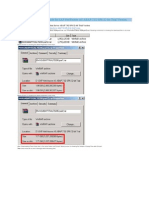
Step 1: Here, we are going to create New Virtual Machine for
installing Backtrack 5 R1. So, we have to click on New Virtual
Machine option in VMware.
Step 2: So, as you see it has opened New Virtual Machine
wizard. It is prompting that what type of configuration do you
want? Select Typical (recommended) then click on Next.
Step 3: Here, it is prompting for selecting ISO Image. So, we are
going to select BackTrack 5 R1 ISO image. After selecting ISO
image just click on Next button to proceed with installation.
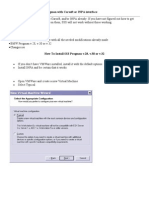
Step 4: Here, it is prompting for Guest operating system. It
means which operating system you are going to install on this
virtual machine. As you might know that BackTrack OS is based
on Linux. So, select Linux as your Guest operating system. In
version it will automatically select Ubuntu.
Step 5: Here, it is prompting for Virtual Machine Name and
Location. So, enter Pentest as our Virtual Machine Name. Here,
we have to choose Location, it means where we want to install
BackTrack 5 R1. Before we select Location, first open D: drive in
My Computer and create one folder there & name this folder
My Virtual Machines. Now open your newly created folder My
Virtual Machines & inside that folder create one more folder &
name this folder BackTrack. Now coming back to our New
Virtual Machine Wizard, In Location browse for our newly
created folder BackTrack in D:\My Virtual Machines\BackTrack.
Select BackTrack folder and then click on Next.
Step 6: Here, it is prompting for Maximum disk size (GB). Enter
20 GB there, and then click on Next.
Step 7: Here, it is prompting for Hardware. In Memory it has
512 MB by default; there is no need to increase Memory for
BackTrack because it works fine in 512 MB. Select Floppy &
click on Remove button to remove it. Select Network Adapter &
change its setting from NAT to Bridged. Finally, click on OK.
Step 8: In this step we have to review all settings & then click
on Finish option. Then it will start Installation of BackTrack 5 R1.
Step 9: Here, just Hit enter key to continue with installation.
Step 10: Here, dont change selection and Just Hit enter key to
continue. So, it will boot in Default Boot Text Mode.
Step 11: Here, type startx on terminal, to start a Graphical User
Interface.
Step 12: Here, just double click on install BackTrack icon.
Step 13: Here, English is by default, so just click on Forward
button to proceed.
Step 14: Here, select your Location to India in world map for
India Time and just click on Forward button to proceed.
Step 15: Here, In Keyboard layout, just click on Forward button
to proceed.
Step 16: Here, where do you want to put BackTrack Live? Select
Erase and use the entire disk option and just click on Forward
button to proceed.
Step 17: Finally click on Install button to proceed.
Step 18: Here, as you see it has started installing BackTrack 5 R1
operating system.
Step 19: Here, as you see its still installing BackTrack 5 R1 OS.
In progress bar its showing 99%. Please be patient here
because it will take at least 10 minutes more to complete.
Surely after 10 minutes it will prompt you to restart the system,
so for that just click on restart button. (Note: When it prompt
then only you have to click on Restart now button)
Step 20: Here, as you see BackTrack 5 R1 is installed properly.
But still we need to install VMware Tools (that includes
Graphics, Sound drivers etc) So, for that we need to Shutdown
our BackTrack OS. So, click on System option & Shut Down.
Step 21: Here, just click on Shut Down.
Step 22: Here, as you see that our BackTrack OS has been Shut
Down. Now, click on Edit Virtual Machine Settings.
Step 23: Here, in Virtual Machine Settings Dialog, Select
CD/DVD (IDE) option. As, you see on the right hand side of
Dialog, its is still using BackTrack ISO image. So, we need to
change this setting.
Step 24: Here, Select Use Physical Drive option & Auto detect
settings. Then click on OK. Then click on Power on This Virtual
Machine.
Step 25: Here, BackTrack is started. Now we are going to move
further to install VMware Tools for our BackTrack OS. So, for
that just right click on your Virtual Machine Name Pentest &
click on Install VMware Tools option.
Step 26: As you see here, VMware Tools ISO image has been
mounted automatically.
Step 27: Now, next step is to create a directory in / and name
this directory vmware.
Step 28: Now Open Terminal and run these commands:
cd /
cd media
cd VMware Tools
ls
tar C /vmware zxvf VMwareTools-8.1.3-203739.tar.gz
After invoking this command it will show you progress
Once progress stops.
Type these command:
cd /vmware
ls
cd vmware-tools-distrib
ls
Now you need to execute vmware-install.pl file, so for that type this command:
./vmware-install.pl
Then it will ask you some questions:
Installing VMware Tools.
In which directory do you want to the install binary files?
[/usr/bin]
Hit enter key
What is the directory that contains the init directories (rc0.d/ to rc6.d/)?
[/etc]
Hit enter key
What is the directory that contains the init scripts?
[/etc/init.d]
Hit enter key
In which directory do you want to install the daemon files?
[/usr/sbin]
Hit enter key
In which directory do you want to install the library files?
[/usr/lib/vmware-tools]
Hit enter key
The path usr/lib/vmware-tools does not exist currently. This program is going to create it, including needed
parent directories. Is this what you want?
[yes]
Hit enter key
In which directory do you want to install documentation files?
[/usr/share/doc/vmware-tools]
Hit enter key
The path /usr/share/doc/vmware-tools does not exist currently. This program is going to create it, including
needed parent directories. Is this what you want?
[yes]
Hit enter key
The installation of VMware Tools 8.1.3 build-203739 for Linux completed successfully. You can decide to remove
this software from your system at any time by invoking the following command: "/usr/bin/vmware-uninstall-
tools.pl".
Before running VMware Tools for the first time, you need to configure it by invoking the following command:
"/usr/bin/vmware-config-tools.pl". Do you want this program to invoke the command for you now? [yes]
Hit enter key
Searching for GCC...
Detected GCC binary at "/usr/bin/gcc".
The path "/usr/bin/gcc" appears to be a valid path to the gcc binary.
Would you like to change it? [no]
Hit enter key
Would you like to change it? [yes]
Type no and Hit enter key
Now it will show you many warning just like below but you do not need to care about
these warning.
Just Press Enter key several times to continue.
WARNING: This program cannot compile any modules for the following reason(s)...
This program could not find a valid path to the kernel headers of the running kernel. Please ensure that the
header files for the running kernel are installed on this system.
[Press Enter key to continue]
Step 29: Finally it will be installed, so, after successful
installation of VMware Tools just right click on VMware Tools
icon on desktop & click on Eject. Now, the last step is to restart
your BackTrack OS Virtual Machine.
Step 30: Now, its time to take Snapshot of BackTrack 5 R1.So,
for that go to VM---Select Snapshot---then select Snapshot
Manager.
Step 31: Click on Take Snapshot.
Step 32: Enter the Name & Description same ---Fresh Copy
Then click on OK.
Step 33: As you see here, snapshot has been taken. Now, click
on Close.
Step 33: Configure the Access Point with open Authentication
and SSID as Wireless Lab
YOU ARE DONE
CONCLUSION:
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
------------------------------To be filled by trainer--------------------------
Remarks:
Poor Fair Good Very Good Excellent
Trainers Signature
LAB 2: Configuring your Wireless Card
OBJECTIVE: To setup the wireless card to work with backtrack
REQUIREMENTS
Computer
Vmware
Backtrack Virtual Machine
Wireless Adapter
STEPS
Step 1: Put your wireless card and start the backtrack machine.
Step 2: Once you log in to the backtrack open the terminal and
type iwconfig to see the wireless interface.
Step 2 : Type ifconfig wlan0 up to bring up the interface and
see the details of your card by typing ifconfig wlan0
Step 3 : Connecting to your AP
First see the list of networks you have
Step 4 : Issue the command iwlist wlan0 scanning
Here you can see all the networks select your network which
you created.
Step 5 : Issue the command iwconfig wlan0 essid Wireless Lab
to associate your wireless card with Wireless Lab.
Step 6: Issue the command iwconfig wlan0 to check whether
it has associated or not.
Step 7 : Set your IP Address from the same subnet
Issue the command ifconfig wlan0 192.168.0.2 255.255.255.0
up
Step 8 : Verify with the command ifconfig wlan0
Step 9 : Now issue the command to ping AP ping 192.168.0.1
YOU ARE DONE
CONCLUSION:
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
------------------------------To be filled by trainer--------------------------
Remarks:
Poor Fair Good Very Good Excellent
Trainers Signature
LAB 3: Creating Monitor Mode Interface
OBJECTIVE: To Configure the wireless card to monitor mode
REQUIREMENTS
Computer
Vmware
Backtrack Virtual Machine
Wireless Adapter
STEPS
Step 1 : Type iwconfig to see your wireless interface
Step 2 : Issue the command ifconfig wlan0 up to bring the card
up.
Step 3 : Verify the card that it is now up by issuing the
command ifconfig wlan0
Step 4 : To put your card into monitor mode we will use the
utility which is inbuilt in backtrack i.e airmon-ng so first issue
the command airmon-ng to verify that it has detected the card,
you should see the wlan0 interface as the output.
Step 5 : Now issue the command airmon-ng start wlan0 to
create a monitor mode interface corresponding to wlan0.this
will be named something in my case lets say mon0.
Step 6 : Now verify that the monitor mode interface is created
by issuing the command airmon-ng
Step 7 : Issue the command ifconfig to see your newly created
monitor mode interface.
YOU ARE DONE
CONCLUSION:
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
------------------------------To be filled by trainer--------------------------
Remarks:
Poor Fair Good Very Good Excellent
Trainers Signature
LAB 4: Sniffing Packets using monitor mode interface
OBJECTIVE: Capture packets using wireshark from mon0
interface.
REQUIREMENTS
Computer
Vmware
Backtrack Virtual Machine
Wireless Adapter
STEPS
Step 1 : Learn the Wlan Frames
In WLANs, communication happens over frames. A frame has
the following header structure:
The Type field defines the type of WLAN frame, which has three
possibilities:
1. Management frames: Management frames are
responsible for maintaining communication between
the access points and wireless clients. The
Management frames can have the following sub-
types:
a. Beacon
b. Probe Request
c. Probe Response
d. Association Request
e. Association Response
f. Disassociation
g. Authentication
h. De-authentication
2. Control frames: Control frames are responsible for
ensuring a proper exchange of data between the
access point and wireless clients. Control frames can
have the following sub-types:
a. Request to Send (RTS)
b. Clear to Send (CTS)
c. Acknowledgement (ACK)
3. Data frames: Data frames carry the actual data sent on the
wireless network. There are no sub-types for data frames.
Step 2 : Switch ON your AP Wireless Lab
Step 3 : start wireshark by typing Wireshark
Step 4 : Click on capture----interface
Step 5 : select packet capture from mon0 interface by clicking
on the start button.
Step 5 : Select one packet and you can able to see the all the
details inside the second window.
Step 6 : click on triangle infront of the IEEE 802.1 Wireless LAN
management frame.
Step 7 : To view all the Management frames in the packets
being captured, enter the filter wlan.fc.type == 0 into the filter
window and click on Apply. You can stop the packet capture if
you want to prevent the packets from scrolling down too fast.
Step 8 : To view Control Frames, modify the filter expression to
read wlan.fc.type == 1
Step 9 : To view the Data Frames, modify the filter expression to
wlan.fc.type == 2
Step 9 : To additionally select a sub-type, use the
wlan.fc.subtype filter. For example, to view all the Beacon
frames among all Management frames use the following filter
(wlan. fc.type == 0) && (wlan.fc.subtype == 8)
Step 10 : Alternatively, you can right-click on any of the header
fields in the middle window and then select Apply as Filter |
Selected to add it as a filter
Step 11 : Find the channel on which the Wireless Lab
access point is running on. To do this, open a terminal and
run airodump-ng bssid 00:21:91:D2:8E:25 mon0 where
00:21:91:D2:8E:25 is the MAC address of our access point.
Let the program run, and shortly you should see your
access point shown on the screen along with the channel
it is running on
Step 12 : Lock our wireless card on the same channel that
is channel, 11. To do this run the command iwconfig mon0
channel 11 and then run iwconfig mon0 to verify the same.
You should see the value Frequency: 2.462 GHz in the
output. This corresponds to Channel 11
Step 13 : Start sniffing on the mon0 interface. After
Wireshark has started sniffing the packets, apply a filter
for the bssid of our access point as shown next using
wlan.bssid == 00:21:91:D2:8E:25 in the filter area. Use the
appropriate MAC address for your access point
Step 14 : In order to see the data packets for our access
point, add the following to the filter (wlan.bssid ==
00:21:91:d2:8e:25) && (wlan.fc.type_subtype == 0x20).
Open your browser and type 192.168.0.1
YOU ARE DONE
CONCLUSION:
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
____________________________________________________
------------------------------To be filled by trainer--------------------------
Remarks:
Poor Fair Good Very Good Excellent
Trainers Signature
You might also like
- Installing BackTrack 5 R1 For Wireless LAN Security TestingDocument28 pagesInstalling BackTrack 5 R1 For Wireless LAN Security TestingKundan PrasadNo ratings yet
- Step by Step Installation of SAP NetWeaver 7.01 SR1 SP3 ABAP Trial VersionDocument59 pagesStep by Step Installation of SAP NetWeaver 7.01 SR1 SP3 ABAP Trial VersionJuan Carlos VargasNo ratings yet
- NctunsDocument12 pagesNctunsSankar Padmanabhan0% (1)
- Steps To Setup Virtual Machine and Installing Windows 11 Pro in VMDocument22 pagesSteps To Setup Virtual Machine and Installing Windows 11 Pro in VMpriyangkaNo ratings yet
- How to Install an OSDocument16 pagesHow to Install an OSKumar KarthickNo ratings yet
- Fedora VBox InstallationDocument22 pagesFedora VBox InstallationAlex J ChurchNo ratings yet
- Documentati On: 1: Installing Virtual BoxDocument26 pagesDocumentati On: 1: Installing Virtual Boxmanishsingh137No ratings yet
- Step by Step Installation Guide For SAP NetWeaver AS ABAP 7.02 SP6 32-Bit Trial VersionDocument31 pagesStep by Step Installation Guide For SAP NetWeaver AS ABAP 7.02 SP6 32-Bit Trial VersionsravanNo ratings yet
- VirtualXP ManualDocument31 pagesVirtualXP Manualandrewb2005No ratings yet
- Step by Step Installation Guide for SAP NetWeaver AS ABAP 7.02 SP6 32-bitDocument18 pagesStep by Step Installation Guide for SAP NetWeaver AS ABAP 7.02 SP6 32-bitSatish KumarNo ratings yet
- Installing Virtual BoxDocument46 pagesInstalling Virtual BoxRajesh Kumar ReddyNo ratings yet
- How To Install KaliDocument35 pagesHow To Install Kalimisko0512100% (1)
- VirtualBox Windows 7 EngDocument24 pagesVirtualBox Windows 7 EngbvnageshaNo ratings yet
- Today Am Going To Teach You How To Install Windows XP in Vmware WorkstationDocument23 pagesToday Am Going To Teach You How To Install Windows XP in Vmware WorkstationNeekesh PandeyNo ratings yet
- IVCC Lab AssignmentDocument19 pagesIVCC Lab AssignmentDiablo YNo ratings yet
- Configure IaaS Architecture in Eucalyptus For Installing Multiple Operating Systems in Same Host MachineDocument5 pagesConfigure IaaS Architecture in Eucalyptus For Installing Multiple Operating Systems in Same Host MachineVasanth AnanthNo ratings yet
- To Install Any Guest Operating System Like Linux Using VmwareDocument4 pagesTo Install Any Guest Operating System Like Linux Using VmwareVairavan MNo ratings yet
- Setup For ofDocument22 pagesSetup For ofSHARIFFNo ratings yet
- EXPERIMENT File OSDocument41 pagesEXPERIMENT File OSPriŃcê sÖniNo ratings yet
- How To Install SSSProgmanwith Virtual DiskDocument24 pagesHow To Install SSSProgmanwith Virtual DiskgorotoNo ratings yet
- CS8711 - Cloud Computing RecordDocument89 pagesCS8711 - Cloud Computing RecordMathioli SenthilNo ratings yet
- Cloud Computing Lab Manual-NewDocument150 pagesCloud Computing Lab Manual-NewAlka SinghNo ratings yet
- Eagle Server Install VM How-To Tutorial-Rev1Document9 pagesEagle Server Install VM How-To Tutorial-Rev1Eduardo DecleNo ratings yet
- Vulnerability Assessment LabDocument27 pagesVulnerability Assessment Labtewiya AKOSSINo ratings yet
- 1.5 - Centos 7 Installation Ver3 - VMwareDocument28 pages1.5 - Centos 7 Installation Ver3 - VMwarezaimdigimaxNo ratings yet
- How To Configure OpenFiler v2.3 iSCSI Storage For Use With VMware ESXDocument42 pagesHow To Configure OpenFiler v2.3 iSCSI Storage For Use With VMware ESXSp PatialNo ratings yet
- Windows Server 2016: Installation and Configuration: Command ReferencesDocument8 pagesWindows Server 2016: Installation and Configuration: Command ReferenceslucasNo ratings yet
- Install Oracle Linux On Virtual BoxDocument32 pagesInstall Oracle Linux On Virtual BoxArshad HussainNo ratings yet
- Install Windows 8 Dev Preview in VMware WorkstationDocument25 pagesInstall Windows 8 Dev Preview in VMware Workstationanand.xissNo ratings yet
- OS Practical FileDocument47 pagesOS Practical FileDevil IVORNo ratings yet
- Python Installation GuideDocument101 pagesPython Installation GuideClaudiu StefanNo ratings yet
- Virtual Reference Design: Pathwave Ads Workspace For Transphorm Tdttp4000W066CDocument35 pagesVirtual Reference Design: Pathwave Ads Workspace For Transphorm Tdttp4000W066CVăn CôngNo ratings yet
- Installation of Windows Server 2012Document10 pagesInstallation of Windows Server 2012NavanathNo ratings yet
- Experiment 1 Creating Guest OS On VMwareDocument17 pagesExperiment 1 Creating Guest OS On VMwareHarsh AryanNo ratings yet
- Installation of Different Operating System PC: ObjectivesDocument26 pagesInstallation of Different Operating System PC: Objectivestasmeya malikNo ratings yet
- Centos Server Configuration A-Z PDFDocument70 pagesCentos Server Configuration A-Z PDFMarina Derrude100% (1)
- VM Ware and Linux Installation LabDocument14 pagesVM Ware and Linux Installation LabJulia PayetteNo ratings yet
- OS Practical File (1900651)Document59 pagesOS Practical File (1900651)Gurjot Singh 651No ratings yet
- How Install Cccam Server WindowsDocument89 pagesHow Install Cccam Server Windowsmanntulang82% (11)
- UTM Installation and UTM Tasks ReportDocument20 pagesUTM Installation and UTM Tasks Reportdibash sigdelNo ratings yet
- Data Protection Manager 2010 Step by StepDocument12 pagesData Protection Manager 2010 Step by Stepthanhbcvt_1989No ratings yet
- Introduction to Setting Up a Client/Server NetworkDocument60 pagesIntroduction to Setting Up a Client/Server NetworkBernadeth Dusal GuiasilonNo ratings yet
- LPIC-1 and CompTIA LinuxDocument13 pagesLPIC-1 and CompTIA Linuxstephen efangeNo ratings yet
- Course - 2014 05 11 C Programming PDFDocument110 pagesCourse - 2014 05 11 C Programming PDFdrpdzNo ratings yet
- Ubuntu VM Installation Guide v1 Y6o n27bk3cDocument30 pagesUbuntu VM Installation Guide v1 Y6o n27bk3cSuraj KumarNo ratings yet
- How To Install Windows Server 2003 Enterprise Edition As Vmware Virtual Machine For Installing Sap ECC 6.0Document11 pagesHow To Install Windows Server 2003 Enterprise Edition As Vmware Virtual Machine For Installing Sap ECC 6.0Joseph DeckerNo ratings yet
- Q:-01: - Create The Hard Disk Partitrion in Linux AnsDocument93 pagesQ:-01: - Create The Hard Disk Partitrion in Linux AnsRitu MalviyaNo ratings yet
- Installing CUCM 10 in VMware WorkstationDocument21 pagesInstalling CUCM 10 in VMware Workstationmohand omaraNo ratings yet
- Ubuntu VM Installation Guide 4ta Zz4uvj2Document30 pagesUbuntu VM Installation Guide 4ta Zz4uvj2KOUSIK KNo ratings yet
- Install and Configure SUSE Linux and SAP NetWeaverDocument49 pagesInstall and Configure SUSE Linux and SAP NetWeaverrajesh98765No ratings yet
- How To Install VMware Workstation and Create A Virtual Machine On Your PCDocument19 pagesHow To Install VMware Workstation and Create A Virtual Machine On Your PCKhizar HayatNo ratings yet
- How to install a CCcam server on Windows in 38 charactersDocument93 pagesHow to install a CCcam server on Windows in 38 charactersGuillermo Salas M.100% (1)
- Install Hyper-V and Deploy Windows Server 2008 VMDocument27 pagesInstall Hyper-V and Deploy Windows Server 2008 VMMuhammad Majid KhanNo ratings yet
- Obiee 11g InstallationDocument159 pagesObiee 11g Installationmlgovardhan100% (1)
- The Big Softice Howto: A Step by Step GuideDocument24 pagesThe Big Softice Howto: A Step by Step GuideMichael WilliamsNo ratings yet
- Windows Operating System: Windows Operating System (OS) Installation, Basic Windows OS Operations, Disk Defragment, Disk Partitioning, Windows OS Upgrade, System Restore, and Disk FormattingFrom EverandWindows Operating System: Windows Operating System (OS) Installation, Basic Windows OS Operations, Disk Defragment, Disk Partitioning, Windows OS Upgrade, System Restore, and Disk FormattingNo ratings yet
- How to Install WordPress on Your Windows Computer Using WampFrom EverandHow to Install WordPress on Your Windows Computer Using WampNo ratings yet
- ICSE PapersDocument5 pagesICSE Papersvijay_786No ratings yet
- ICSE Board Class X Biology Board Paper 2008 (One Hour and A Half)Document9 pagesICSE Board Class X Biology Board Paper 2008 (One Hour and A Half)vijay_786No ratings yet
- OTU-8000 Optical Test Unit: Rack-Mounted Fiber Test For Backbone, Metro, and Access NetworksDocument2 pagesOTU-8000 Optical Test Unit: Rack-Mounted Fiber Test For Backbone, Metro, and Access Networksvijay_786No ratings yet
- IEEE SDN Workshop Sponsorship FlyerDocument2 pagesIEEE SDN Workshop Sponsorship Flyervijay_786No ratings yet
- E1 TroubleshootingDocument20 pagesE1 TroubleshootingDavid Chandy PesantezNo ratings yet
- Esdm IrdtDocument259 pagesEsdm Irdtvijay_786No ratings yet
- 2007 QuestionsDocument9 pages2007 Questionsvijay_786No ratings yet
- Cable Drum Handling ManualDocument40 pagesCable Drum Handling Manualjeb13No ratings yet
- WiMAX AgilentDocument28 pagesWiMAX AgilentDheeraj100% (1)
- Fiber Safety RulesDocument1 pageFiber Safety Rulesvijay_786No ratings yet
- Guidebook For Optical Time Domain ReflectometerDocument12 pagesGuidebook For Optical Time Domain ReflectometerkumarsachinguptaNo ratings yet
- MAC WLAN Notes PDFDocument20 pagesMAC WLAN Notes PDFHoney KaushikNo ratings yet
- Ethernet PONDocument11 pagesEthernet PONchaidar_lakareNo ratings yet
- Optical Fiber Cable Works (OFC) : ELC Solutions Corp Private LimitedDocument12 pagesOptical Fiber Cable Works (OFC) : ELC Solutions Corp Private LimitedLaolu Podolski IpadeolaNo ratings yet
- OFC Applications GuidelinesDocument27 pagesOFC Applications Guidelinesvijay_786No ratings yet
- FTTH Drop and Indoor CablesDocument8 pagesFTTH Drop and Indoor Cablesvijay_786No ratings yet
- Orientation Seminar For Education StaffDocument11 pagesOrientation Seminar For Education Staffvijay_786100% (1)
- 18-MSTP Configuration - 206300 - 1285 - 0Document59 pages18-MSTP Configuration - 206300 - 1285 - 0vijay_786No ratings yet
- Antennas (New)Document34 pagesAntennas (New)vijay_786No ratings yet
- WiMAX AgilentDocument28 pagesWiMAX AgilentDheeraj100% (1)
- ZXSDR BS8800Document9 pagesZXSDR BS8800vijay_786No ratings yet
- SDHDocument80 pagesSDHMavura Michael MgayaNo ratings yet
- Tax Saving Options Fy2012-2013Document5 pagesTax Saving Options Fy2012-2013vijay_786No ratings yet
- FTTH Optical InfrastructureDocument30 pagesFTTH Optical Infrastructurevijay_786100% (1)
- EthernetDocument19 pagesEthernetAmit SharmaNo ratings yet
- EVDO Rel A Basic-20081212Document23 pagesEVDO Rel A Basic-20081212badri1969revanthNo ratings yet
- CDMA For Trainee's From HUWAEIDocument89 pagesCDMA For Trainee's From HUWAEIvijay_786No ratings yet
- CDMA 2000 1X RTT: An Overview of Key Features and PerformanceDocument19 pagesCDMA 2000 1X RTT: An Overview of Key Features and Performancevijay_786No ratings yet
- Cisco RPR TutorialDocument0 pagesCisco RPR Tutorialvijay_786No ratings yet
- Articulate Storyline To Scorm 1 2 and SabaDocument14 pagesArticulate Storyline To Scorm 1 2 and SabaSantosh DasNo ratings yet
- Guide WizconDocument125 pagesGuide WizconlettolimaNo ratings yet
- Creating A Command in AutoCAD With C#Document26 pagesCreating A Command in AutoCAD With C#ask_ienNo ratings yet
- S4H - 947 User Experience Strategy TemplateDocument13 pagesS4H - 947 User Experience Strategy TemplateEdir JuniorNo ratings yet
- Azure Data SolutionsDocument7 pagesAzure Data SolutionsSrinivas GorantlaNo ratings yet
- Google Maps Distance CalculatorDocument1 pageGoogle Maps Distance CalculatorPRABHUTIRUPURNo ratings yet
- Alert Method in JavaScriptDocument4 pagesAlert Method in JavaScriptPriyanka KaliyaperumalNo ratings yet
- Transaction ManagerDocument62 pagesTransaction ManagerAnonymous 5cMeyYyxhNo ratings yet
- Ms Office Lab ManualDocument53 pagesMs Office Lab Manuallakshmi.s100% (3)
- Difference Between BW, BW On HANA and Native HANADocument2 pagesDifference Between BW, BW On HANA and Native HANASourabhNo ratings yet
- Line Sets in Oracle Order ManagementDocument9 pagesLine Sets in Oracle Order ManagementS S PatelNo ratings yet
- 5138Document4 pages5138Anvar Sadath A.KNo ratings yet
- Openstack Install Guide Apt TrunkDocument149 pagesOpenstack Install Guide Apt TrunkAkhil GuptaNo ratings yet
- Azure Data Engineer Learning Path (OCT 2019)Document1 pageAzure Data Engineer Learning Path (OCT 2019)boobeshNo ratings yet
- We Carry The Saving CrossDocument12 pagesWe Carry The Saving CrossGood Fellas Custom GuitarsNo ratings yet
- Excel Chapter - 9Document14 pagesExcel Chapter - 9Shahwaiz Bin Imran BajwaNo ratings yet
- SAS® Enterprise Guide For SAS® Visual Analytics LASR ServerDocument11 pagesSAS® Enterprise Guide For SAS® Visual Analytics LASR ServerDaniloVieiraNo ratings yet
- BPC10 1 BADIsDocument6 pagesBPC10 1 BADIsmanishkr1980No ratings yet
- This Document Contains An Installation and User Guide For Orchestra 4.7.1Document40 pagesThis Document Contains An Installation and User Guide For Orchestra 4.7.1fjsaa19No ratings yet
- Oracle SCM Expert with 17+ Years of ERP ExperienceDocument7 pagesOracle SCM Expert with 17+ Years of ERP ExperienceKarunya KannanNo ratings yet
- Optimize RBQL queries and recordsDocument37 pagesOptimize RBQL queries and recordsLuis MuchakiNo ratings yet
- What Is A Technology Platform?Document4 pagesWhat Is A Technology Platform?Khen BeruegaNo ratings yet
- 5.vulnerability AnalysisDocument18 pages5.vulnerability Analysisbhumika.verma00100% (1)
- Computer ScienceDocument34 pagesComputer ScienceMaisha KéimNo ratings yet
- Uputstvo T25ADocument191 pagesUputstvo T25ADavor PodoreškiNo ratings yet
- ReadmeDocument2 pagesReadmeGreg UmbersNo ratings yet
- Vmware Mac Os X Guest Package: 1.1 BackgroundDocument11 pagesVmware Mac Os X Guest Package: 1.1 BackgroundnadmahmdNo ratings yet
- 100 Days of PowerBuilder-2Document12 pages100 Days of PowerBuilder-2JavaidsNo ratings yet
- Oracle HCM R12.2 New/Changed FeaturesDocument29 pagesOracle HCM R12.2 New/Changed FeaturesAbhishek Singh Tomar100% (2)
- Axapta Hardware Guide 250usersDocument14 pagesAxapta Hardware Guide 250usersRomeo AlamNo ratings yet