Professional Documents
Culture Documents
MTA SSG IT PRO Without Crop
Uploaded by
snadminOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
MTA SSG IT PRO Without Crop
Uploaded by
snadminCopyright:
Available Formats
Student Study Guide
IT Pro Edition
MI C ROS OF T T E C HNOL OGY AS S OC I AT E
Preparing for MTA Certication
EXAM 98-365 Windows Server Administration Fundamentals
EXAM 98-366 Networking Fundamentals
EXAM 98-367 Security Fundamentals
EXAM 98-349 Windows Operating System Fundamentals
M
T
A
S
t
u
d
e
n
t
S
t
u
d
y
G
u
i
d
e
I
T
P
R
O
E
D
I
T
I
O
N
MTA EXAMS
MICROSOFT TECHNOLOGY ASSOCIATE (MTA)
STUDENT STUDY GUIDE FOR IT PROS
Preparing for MTA Certication
MICROSOFT TECCHNOLOGY SSOCIATE ((MMT
STUDENT STUDY GUIDE F
Preparing ffoor MTA Certtiicaation
A
n
AASSOCIATE
FOR IT PROS
CCeerrttiiccaa
ECHNOLOGY ASSOCIATE (MTA
UDY GUIDE FOR IT PROS
for MTA Certication
A)
98-365 Windows Server Administration
Fundamentals
98-366 Networking Fundamentals
98-367 Security Fundamentals
98-349 Windows Operating System
Fundamentals
Michael Teske (Windows Operating System). Michael has been
teaching in the Network Specialist Program for 10 years at Northeast
Wisconsin Technical College and has been involved as an engineer for
15 years. He has a passion for both teaching and technology and loves
helping people nd happiness in a career. Mike believes that learning
technology should be fun, but he also recognizes that the networking
eld continually changes and can challenge even the brightest students.
Mike also works as an independent consultant for several small
businesses in northeast Wisconsin and enjoys bringing that real-world
experience in to the classroom on a daily basis. Mike has become known
as the Microsoft Guy on campus. His goal is to continue to teach
network technology with the same enthusiasm and passion for many
years to come and to help his students nd the same joy and passion
that he has found in an amazing industry.
Jeffrey Sonnleitner (Windows Operating System). Jeff is a lead Instructor
in the Information Technologies department at Moraine Park Technical
College (MPTC) in Fond du Lac, Wisconsin. Jeff teaches the Network
Specialist degree program and the Advanced Technical Certicate in
Information Security. Jeff is also certied to teach classes in international
business. He is beginning his 10th year at MPTC, and enjoys teaching
courses in networking, Microsoft servers, and information security. Jeffs
goal is to help students succeed and enjoy their college experience in a
future-focused learning environment. He was instrumental in developing
MPTCs student exchange with technical colleges in Darmstadt, Germany,
and he has led the colleges student exchange programs for over six
years. As an advisor to MPTCs student IT Club, he initiated annual tours
to Silicon Valley. Prior to joining the faculty at MPTC, Jeff spent 14 years
as an independent consultant, specializing in medical and dental ofce
computer systems and software.
Tim McMichael (.NET Development). Tim has been a high school
computer science teacher for the past 11 years. He currently teaches
Advanced Placement computer science, .NET programming, and
computer game programming at Raymond S. Kellis High School in
Glendale, Arizona. Prior to teaching, Tim worked for several years as
a database application developer. Tim is the author of the Software and
Windows Development Exam Review Kits in the Developer Exam Review
Kit series.
Tom Indelicato (.NET Development). Tom teaches computer science at
Bishop Guertin High School in Nashua, New Hampshire for 11 years,
including courses on Microsoft Ofce applications, Microsoft Visual Basic
programming, AP computer science, and, most recently, autonomous
robotics programming. Outside the classroom, he runs the schools FIRST
Robotics team. Prior to teaching, Tom was a software engineer for
17 years.
Patricia Phillips (Authoring Manager). Patricia taught computer science
for 20 years in Janesville, Wisconsin. She served on the Microsoft
National K-12 Faculty Advisory Board and edited the Microsoft
MainFunction website for technology teachers for two years. For the
past ve years, she has worked with Microsoft in a variety of roles
related to K-12 curriculum development and pilot programs, such as the
MTA Exam Review Kits and Student Study Guides, Expression Studio web
design, and XNA game development. In her role as an author and editor,
Patricia has written several articles and a student workbook on topics
including computer science, web design, and computational thinking.
She is currently the editor of the Computer Science Teachers Association
newsletter, the Voice.
Authors
This content is only for use by or provision to students for their personal use.
Some examples depicted herein are provided for illustration only and are ctitious. No real association or connection is intended or should
be inferred.
Microsoft and other trademarks listed at http://www.microsoft.com/about/legal/en/us/IntellectualProperty/Trademarks/EN-US
.aspx are trademarks of the Microsoft group of companies. All other marks are property of their respective owners.
2010 Microsoft Corporation. All Rights Reserved. This content is provided as-is and Microsoft makes no warranties, express or implied.
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ixi
Career Planning . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . x
Exploring Job Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xiii
Value of Certication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xiv
98-365 WINDOWS SERVER ADMINISTRATION FUNDAMENTALS
CHAPTER 1 Understanding Server Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
1.1/1/2 Understand device drivers; Understand services . . . . . . . . . . . . . . 5
1.3 Understand server installation options . . . . . . . . . . . . . . . . . . . . . . . . . . 7
CHAPTER 2 Understanding Server Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
2.1 Identify application servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
2.2 Understand Web services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
2.3 Understand remote access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
2.4 Understand le and print services . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
2.5 Understand server virtualization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
98-365 WINDOWS SERVER ADMINISTRATION FUNDAMENTALS
CHAPTER 1
CHAPTER 2
Contents
CHAPTER 3 Understanding Active Directory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
3.1 Understand accounts and groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
3.2 Understand organizational units (OUs) and containers . . . . . . . . . . 25
3.3 Understand Active Directory infrastructure . . . . . . . . . . . . . . . . . . . . 27
3.4 Understand group policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
CHAPTER 4 Understanding Storage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
4.1/4.2 Identify storage technologies; Understand RAID . . . . . . . . . . . . . 33
4.3 Understand disk types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
CHAPTER 5 Understanding Server Performance Management . . . . . . . . . . . . . . 37
5.1 Identify major server hardware components. . . . . . . . . . . . . . . . . . . . 39
5.2 Understand performance monitoring . . . . . . . . . . . . . . . . . . . . . . . . . 41
5.3 Understand logs and alerts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
CHAPTER 6 Understanding Server Maintenance . . . . . . . . . . . . . . . . . . . . . . . . . . 45
6.1 Identify steps in the startup process . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
6.2 Understand business continuity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
6.3 Understand updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
6.4 Understand troubleshooting methodology . . . . . . . . . . . . . . . . . . . . . 53
98-366 NETWORKING FUNDAMENTALS
CHAPTER 1 Understanding Networking Infrastructures . . . . . . . . . . . . . . . . . . . . 57
1.1 Understand the concepts of the internet, intranet, and extranet . . . 59
CHAPTER 3
CHAPTER 4
CHAPTER 5
CHAPTER 6
CHAPTER 1
98-366 NETWORKING FUNDAMENTALS
iv Contents
1.2A Understand local area networks (LANs) . . . . . . . . . . . . . . . . . . . . . . 61
1.2B Understand local area networks (LANs) . . . . . . . . . . . . . . . . . . . . . . . 63
1.3A Understand wide area networks (WANs) . . . . . . . . . . . . . . . . . . . . . . 65
1.3B Understand wide area networks (WANs) . . . . . . . . . . . . . . . . . . . . . . 67
1.4 Understand wireless networking . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
1.5 Understand network topologies and access methods . . . . . . . . . . . . . 71
CHAPTER 2 Understanding Network Hardware . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
2.1A Understand switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
2.1B Understand switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
2.2 Understand routers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
2.3A Understand media types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
2.3B Understand media types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
CHAPTER 3 Understanding Protocols and Services . . . . . . . . . . . . . . . . . . . . . . . . 85
3.1A Understand the OSI model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
3.1B Understand the OSI model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
3.2 Understand IPv4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
3.3A Understand IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
3.3B Understand IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
3.4 Understand names resolution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 97
3.5 Understand networking services . . . . . . . . . . . . . . . . . . . . . . . . . . 99
3.6 Understand TCP/IP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
CHAPTER 3
Contents v
98-367 SECURITY FUNDAMENTALS
CHAPTER 1 Understanding Security Layers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
1.1 Understand core security principles . . . . . . . . . . . . . . . . . . . . . . . . . 107
1.2 Understand physical security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
1.3 Understand Internet security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
1.4 Understand wireless security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
CHAPTER 2 Understanding Operating System Security . . . . . . . . . . . . . . . . . . . 115
2.1A Understand user authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
2.1B Understand user authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
2.2 Understand permissions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 121
2.3 Understand password policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
2.4 Understand audit policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
2.5A Understand encryption . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
2.5B Understand encryption . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
2.6 Understand malware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
CHAPTER 3 Understanding Network Security . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
3.1 Understand dedicated rewalls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
3.2 Understand Network Access Protection (NAP) . . . . . . . . . . . . . . . . 137
3.3A Understand Network Isolation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
3.3B Understand Network Isolation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
3.4 Understand protocol security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
CHAPTER 2
CHAPTER 1
CHAPTER 3
vi Contents
CHAPTER 4 Understanding Security Software . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
4.1 Understand client protection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
4.2 Understand email protection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
4.3 Understand server protection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
98-349 WINDOWS OPERATING SYSTEM FUNDAMENTALS
CHAPTER 1 Understanding Operating System Congurations . . . . . . . . . . . . . . 155
1.1/1.2 Congure Control Panel options; Congure desktop settings 157
1.3 Understand native applications and tools . . . . . . . . . . . . . . . . . . . . . 159
1.4/1.5 Understand mobility; Understand remote management and
assistance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
CHAPTER 2 Installing and Upgrading Client Systems . . . . . . . . . . . . . . . . . . . . . 163
2.1/2.2 Identify Windows operating system editions; Identify
upgrade paths . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
2.3 Understand installation types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
2.4 Understand virtualized clients . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
CHAPTER 3 Managing Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
3.1 Understand application installations . . . . . . . . . . . . . . . . . . . . . . . . . . 173
3.2 Understand user account control (UAC) . . . . . . . . . . . . . . . . . . . . . . . 175
3.3 Remove malicious software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
3.4 Understand services. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
3.5 Understand application virtualization . . . . . . . . . . . . . . . . . . . . . . . . . 181
CHAPTER 4
98-349 WINDOWS OPERATING SYSTEM FUNDAMENTALS
CHAPTER 1
CHAPTER 2
CHAPTER 3
Contents vii
viii Contents
CHAPTER 4 Managing Files and Folders . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
4.1 Understand le systems . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
4.2 Understand le and print sharing . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
4.3 Understand encryption . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
4.4 Understand libraries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
CHAPTER 5 Managing Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
5.1/5.2 Connect devices; Understand storage . . . . . . . . . . . . . . . . . . . . . 195
5.3 Understand printing devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197
5.4 Understand system devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
CHAPTER 6 Understanding Operating System Maintenance . . . . . . . . . . . . . . . 201
6.1 Understand backup and recovery methods . . . . . . . . . . . . . . . . . . . 203
6.2/6.3 Understand maintenance tools; Understand updates . . . . . . . . 205
CHAPTER 4
CHAPTER 5
CHAPTER 6
Introducti on ix
M
TA validates building-block technology concepts
and helps students explore, discover and
pursue successful careers in Information Technology
(IT) in an exciting and rewarding way! As the rst step
in the Microsoft Technology Certication Series, this
new, entry-level certication provides students with
condence, credibility, and differentiation.
Explore IT career options without committing
a lot of time and resources MTA exams validate
the core technology knowledge that is in demand
today by businesses around the world. Whether you
want to explore becoming a network administrator,
software engineer, web developer, or database
analyst, MTA gets you started on the right path.
Prepare to compete A little investment in IT can
go a long way in todays job market. Becoming MTA
certied helps you build a solid foundation to prepare
for intermediate technology studies and for Microsoft
Certied Technology Specialist (MCTS) certications.
It can also help you compete on college admissions
and jumpstart your IT career planning!
Empower yourself As the rst step toward
becoming an MCTS, MTA shows your commitment to
technology while connecting you with a community
of more than ve million Microsoft Certied
Professionals. Learn from them and show them what
you know by becoming MTA certied!
This MTA Student Study Guide serves as a study tool
to help students prepare for their MTA certication
exam. Students are challenged with real-life situations
for each of the major topics covered in the exam.
Although successful completion of the study guide
exercises does not guarantee that you will pass your
MTA exam, it is an excellent way to gauge your
readiness to take the exam and build condence
that you know your stuff on exam day.
I wish you all the best as you prepare for a successful
career in technology!
Victoria Pohto
Victoria Pohto
MTA Product Marketing Manager
Introduction
x Career Planning
Career Planning
M
ost IT solutions or infrastructure built on
Microsoft technologies require prociency
with one or all of the following products, often
referred to as The Microsoft Stack.
Microsoft Windows
Server
as the data center
or development platform
Microsoft SQL Server
as the data and business
intelligence (BI) platform
Microsoft Visual Studio
as the suite of application
life-cycle management tools
MTA is the starting point of Microsoft technology
certications, providing aspiring technologists with
the fundamental knowledge essential to succeed
with continued studies and a successful career with
technology.
Preparing for and becoming MTA certied helps you
explore a variety of career paths in technology with-
out investing a lot of time and money in a specialized
career path. When you nd a path that is right for
you, Microsoft learning products and certication can
help you prepare and guide your longer-term career
planning.
If you already know that you want to start building
a career in technology, MTA preparation and certi-
cation is the recommended entry point. Becoming
MTA certied shows that you have a rm working
knowledge of the fundamental IT concepts critical
for success with intermediate learning and
certications such as Microsoft Certied Technology
Specialist (MCTS). Moreover, Microsoft certications
demonstrate an individuals commitment of self-
investment and condence to take his or her
knowledge and skills to the next level with an
industry-recognized credential.
MTA is not a career certication, meaning that
employers recognize you as job ready, but it is the
rst step toward that career goal and can help
differentiate you for an internship or to college
admissions committees. As you prepare for your rst
job focusing on technology, be sure that you
are equipped with an MCTS credentialthe
intermediate level certication that validates
Microsoft product and technology skills.
The MTA Certication path on the next page shows you
the MTA exams that are recommended prior to taking
on some of Microsofts intermediate technology
certication, MCTS.
Career Planning xi
xii Expl oring Job Rol es
Exploring Job Roles
C
hoosing a career path is a big decision and its
not always easy, but youre not alone! Microsoft
created a career site to help students understand the
options and possibilities of pursuing a career in IT.
The site also connects you with learning resources,
student techie communities, and much more to help
you prepare for a career in technology.
To chart your career with Microsoft technology,
visit www.microsoft.com/learning/career/en/us/
career-org-charts.aspx.
Database Administrator
As a database administrator, you are in charge
of important databases that span multiple
platforms and environments. You are a strong
team player who thrives in a fast-paced
environment. You build complex, highly scalable
databases that meet business needs and security
requirements. You are an expert in optimizing,
maintaining, and troubleshooting databases, but also
in designing archival, data distribution, and high-
availability solutions.
Server Administrator
As a server administrator, you are in charge
of implementing and managing some
of the most important technology in your
organizationthe servers. You use extensive
monitoring and proling tools to manage the
network and tune systems so they perform at optimal
levels. You are an expert in Active Directory
, and you
have an in-depth understanding of network
protocols, and le and directory security.
Computer Support Technician
Consider starting your IT career by becoming
a consumer support technician. You dont
need any formal work experience, but a
company might require that you know how to
install, administer, and troubleshoot operating
systems in a home network environment that has
desktop computers, laptops, and printers. As a
consumer support technician, youll also handle
network, virus, malicious software, and hardware
support issues. Youll typically nd this position in
small to medium-sized organizations.
Expl oring Job Rol es xiii
Exploring Job Roles
Web Developer
As a web developer, you are an expert in
using the dynamic programming tools and
languages that fuel the web. You might work
independently or be part of a team that builds
and integrates interactive web sites, applications, and
services for both internal and public sites. Your role is
to make it work, which means developing web
applications and testing them on various browsers,
enhancing and modifying them as necessary to
ensure the best experience for the user. As a web
developer, you might also architect websites, design
data-driven applications, and nd efcient client-
server solutions. You must have an in-depth under-
standing of the software development life cycle and
be able to communicate project status, issues, and
resolutions.
Windows Developer
As a Windows client developer, knowing how
to optimize Windows code and track bugs is a
given. But you also know how to use Microsoft
Visual Studio
and the Microsoft .NET frame-
work to design, develop, test, and deploy Windows-
based applications that run on both corporate servers
and desktop computers. Your key talents include
understanding multiple Windows application models
and n-tier applications, and knowing how to work
with object-oriented programming, algorithms, data
structures, and multithreading. Windows developers
have an in-depth understanding of software engi-
neering principles, software life cycles, and security
principles.
Additional Online Resources for New Developers:
http://msdn.microsoft.com/beginner
http://msdn.microsoft.com/rampup
Imagine Cup
The Imagine Cup is the
worlds premier student
technology competition
where students from
around the world can learn new skills, make new
friends, and change the world. Competitions
include Software Design, Embedded Development,
Game Design, Digital Media and Windows Phone 7.
The brightest young minds harness the power of
technology to take on the worlds toughest problems.
www.imaginecup.com
xiv Val ue of Cer ti f i cati on
Value of Certication
T
echnology plays a role in virtually everything
we do. In the 20-plus years since Microsoft has
been certifying people on its products and technolo-
gies, millions of people have gained the knowledge,
expertise, and credentials to enhance their careers,
optimize business solutions, and create innovation
within just about every business and social sector
imaginable. Todays Information Technology (IT)
hiring managers are more often using professional
credentials, such as Microsoft certication, to identify
properly skilled IT candidates. Certication becomes
a way to easily differentiate qualied candidates in a
sea of resumes.
The job outlook for IT professionals, as reported in
a study prepared by the U.S. Department of Labors
Bureau of Labor Statistics (BLS), is positive! The BLS
indicates an increase that will be faster than the
average for all occupations through 2014 for
Computer Support Specialists, Systems Engineers,
Database Administrators, and Computer Software
Engineers. One signicant message resulting from
this study is that information and communications
technology (ICT) skills are the entry ticket to the
job market, regardless of the country, industry, or
job function. Information Technology is clearly an
area worth investing time, resources, and education
in and technology certication is a key part of the
education process, validating product and technology
expertise as a result of their learning experiences.
Microsoft IT Certications provide objective validation
of the ability to perform critical IT functions success-
fully for worldwide IT professionals, developers, and
information workers. Microsoft certications repre-
sent a rich and varied spectrum of knowledge, job
roles, and responsibilities. Further, earning a specic
certication provides objective validation of the
candidates ability to perform critical IT functions
successfully. Embraced by industry professionals
worldwide, Microsoft certication remains one of the
most effective ways to help reach long-term career
goals.
MTA 98-365
WINDOWS SERVER
ADMINISTRATION
FUNDAMENTALS
1
Understanding
Server Installation
IN THI S CHAPTER
1.1/1.2 Understand device drivers; Understand services
1.3 Understand server installation options
Understand devi ce dri vers; Understand ser vi ces 5
Understand device drivers; Understand services
SCENARIO: Maurice Taylor is the network administrator for Fabrikam, Inc. A workstation that he plans to image
and roll out to production is having issues with the video display. The display worked initially when he rst set up
the system. After applying several system and driver updates, the video has degraded to standard VGA 640x800
and performance has really stunk. He knows this wont be acceptable.
Maurice also is having an issue with the rewall service on his Windows
Server
2008 R2 Web server. The service
fails to start when the system starts; however, Maurice can start it manually after he logs in. Maurice does not
want to manually start that service every time maintenance on the web server is required, and he realizes that
hell be in big trouble if he doesnt secure the web server by forgetting to turn on the rewall service.
1. What could be a possible reason for Maurices video problems?
a. Maurice installed the wrong video driver
b. Maurice installed an incompatible or corrupted video driver
c. the video adapter is not properly seated on the system board
2. Where should Maurice check to verify if he has a proper driver installed?
a. Event Viewer
b. Disk Management
c. Device Manager
3. What can Maurice do with the web service to ensure that it will start after
the other system services finish their startup?
a. configure a delayed startup for the web service through the services.msc
b. write a batch program to start the service as a scheduled task
c. configure the service to restart after first failure
OBJECTIVE UNDERSTANDI NG SERVER I NSTALLATI ON 1. 1/1. 2
Performance suffers
if a service is failing
to start.
6 CHAPTER 1: Understanding Ser ver Installati on
Answers
1. Maurices video problem occurred because:
b. Maurice installed an incompatible or corrupted video driver
2. Driver problems can be found in the:
c. Device Manager
3. The interim solution to the web service is:
a. configure a delayed startup for the web service through the services.msc. Maurice can open
services.msc and configure the service for a delayed start for the startup type. This will allow
the remaining services to finish starting. Maurice should investigate what possible services
would be causing these issues.
Essential details
A device driver is a software component that permits an operating system to communicate with a device.
A service is a long-running executable that performs specific functions and that is designed not to require
user intervention.
FAST TRACK HELP
http://www.microsoft.com/whdc/driver/install/drvsign/default.mspx
http://technet.microsoft.com/en-us/library/dd919230(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc732482.aspx
FAST TRACK HELP
_______ /3
Understand ser ver installati on opti ons 7
OBJECTIVE UNDERSTANDI NG SERVER I NSTALLATI ON 1. 3
Understand server installation options
SCENARIO: On Thursday, Pat was tasked with setting up 10 servers and 20 workstations per specication.
Pat is aware that if he sets up each one individually, he will be at work through the weekend, and he doesnt
want to do that because he has plans to go to a concert with some friends. Pat knows the company uses
Windows Deployment Services whenever a new workstation or server is rolled out. Pat would like to automate
these installations with as little human interaction as possible.
1. What can Pat do to make sure he can make it to the concert this weekend?
a. start his installations manually and hope they finish in time
b. create one completed installation, setup and configuration of a server and a workstation and use those
two copies to image the remaining systems using Windows Deployment Services and ImageX
c. sell his tickets to his buddyits not going to happen
2. What is ImageX?
a. a picture editing utility
b. a personal image enhancement service
c. a system imaging software that takes a snapshot of an existing, configured server
or workstation and creates an imaged or cloned version of that system
and saves it to a file
3. What can Pat use to solve the last part of his problem, which requires as little
human interaction as possible?
a. have a robot do the installations
b. use Windows System Image Manager to create an answer file that will automatically
provide the answers to the setup questions throughout installation as well as
configure and install any necessary software during the installation
c. create a DVD that will contain all of the necessary software that will be installed
on the servers and workstations
Answer les have a
variety of features that
can be used through
Windows Deployment
Services to create a
custom installation DVD.
8 CHAPTER 1: Understanding Ser ver Installati on
Answers
1. Pat can complete the installs if he:
b. creates one completed installation, setup and configuration of a server and a workstation and
use those two copies to image the remaining systems using Windows Deployment Services and
ImageX. Creating the two images or clones will allow Pat to duplicate those installations by pushing
those files (images) onto the hard drives of the remaining systems.
2. ImageX is:
c. a system imaging software that takes a snapshot of an existing, configured server or
workstation and creates an imaged or cloned version of that system and saves it to a file.
ImageX can be copied to a bootable CD/DVD/USB and used to create image files of an existing system
for duplicating or backup purposes.
3. Pat can eliminate interactions during the installs if he:
b. uses Windows System Image Manager to create an answer file that will automatically provide
the answers to the setup questions throughout installation as well as configure and install any
necessary software during the installation.
Essential details
An unattended installation is a process of automating operating system installations by providing the
setup/install file with a configuration file or answer file to perform and answer normal
install tasks and questions.
An answer file is an XML-based file that contains setting definitions and values to use
during Windows Setup. In an answer file, you specify various setup options, including
how to partition disks, the location of the Windows image to install, and the product
key to apply.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc785644(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc771670(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc749317(WS.10).aspx
FAST TRACK HELP
o use
ding ding
uctt uct
_______ /3
2
Understanding
Server Roles
IN THI S CHAPTER
2.1 Identify application servers
2.2 Understand Web services
2.3 Understand remote access
2.4 Understand le and print services
2.5 Understand server virtualization
Identify application servers
SCENARIO: Cari is a systems administrator for Contoso, Ltd. She needs to develop a systems design so her
company can use an email messaging system that allows for message and calendar collaboration. Contoso, Ltd.
uses Microsoft
Ofce 2010 as their mainline ofce production suite. Her company also wants a collaboration
server for their intranet. The collaboration server should support dynamic updating from the employees
of Contoso, Ltd. Company ofcers would like to have the intranet monitored and protected with a threat
management solution.
1. What would be Caris best solution for their messaging system?
a. use a third party email provider and a custom developed calendaring program
b. include Microsoft Exchange Server 2010
c. not recommend any solution because of the potential loss of production with an email messaging
system
2. What can meet the needs of the Contoso. Ltd. Intranet collaboration server?
a. implement SharePoint
Portal Server 2010 which uses Microsoft SQL as an option to support dynamic
updating
b. solicit bids from various web development firms to meet their intranet needs
c. create a Microsoft Word document and send a link to it throughout the company
and call it their messaging board
3. What would be the best fit to meet the companys needs so that they can manage
their employees internet access through Active Directory?
a. have all employees sign an internet usage contract and document the sites they
visit and promise not to install any malicious software onto their systems
b. recommend Microsofts Threat Management Gateway, which provides integration with
Microsoft Forefront
antivirus and can grant or deny various types of internet behavior
either by user name or group
c. only allow internet access from one computer that employees can sign up to use in 30-minute
increments
I denti f y appl i cati on ser vers 11
OBJECTIVE UNDERSTANDI NG SERVER ROLES 2. 1
h
or
0 i
Providing
integrated solutions
that will also integrate
with existing applications
provides fewer potential
compatibility issues.
12 CHAPTER 2: Understanding Server Rol es
Answers
1. The best solution for their messaging system is to:
b. include Microsoft Exchange Server 2010. Microsoft Exchange will integrate with the Contoso, Ltd.
Existing core production suite with reduced learning curves for their employees.
2. The collaboration server needs can be met by:
a. implementing SharePoint Portal Server 2010 which uses Microsoft SQL as an option to support
dynamic updating
3. The best fit to meet the companys needs so they can manage their employees internet access through
Active Directory is:
b. Microsofts Threat Management Gateway, which provides integration with Microsoft Forefront
antivirus and can grant or deny various types of internet behavior either by user name or group
Essential details
Active Directory
is the central location for configuration information, authentication requests,
and information about all of the objects that are stored within your forest.
SharePoint provides a turnkey solution that will integrate with the existing core production suite as well as a
communications server. Data will be stored with the inherent SQL application incorporated.
FAST TRACK HELP
http://www.microsoft.com/exchange/2010/en/us/default.aspx
http://sharepoint.microsoft.com/en-us/Pages/default.aspx
http://www.microsoft.com/forefront/threat-management-gateway/en
/us/overview.aspx
http://office.microsoft.com/en-us/sharepoint-server-help
/CH010030543.aspx
FAST TRACK HELP
_______ /3
Understand Web ser vi ces 13
Understand Web services
SCENARIO: Alicia is a server administrator for Tailspin Toys. Security personnel have contacted her to provide
them with security information regarding her web exposed servers. They want to know which servers will have
access from beyond the perimeter security appliance so that they can accommodate the incoming and outgoing
trafc. Alicia responds that two of her three servers require perimeter access: First, the intranet server, which is
running SharePoint, will need SSL access for the remote toy salespeople. Her second server is the companys web
server, where online customers can buy their toys from the comfort of their own homes. Customer transactions
must be secured in some fashion. Their web developers also request FTP access to the web server so that they
can upload and download updated content.
1. The security people have asked for the ports Alicia wants available for the intranet server running
Microsoft SharePoint. What will her response be?
a. 445
b. 443
c. 80
2. Alicia wants all transactions to the storefront on their web server to be encrypted. What security
protocol encrypts web traffic?
a. Secure Socket Layer, SSL
b. Point to Point Tunneling Protocol, PPTP
c. Central Intelligence Agency, CIA
3. What does is FTP and what port(s) does it communicate on?
a. FTP is File Transport Protocol, a fast, application-level protocol widely
used for copying files to and from remote computer systems on a network
using TCP/IP, such as the internet. It communicates on ports 20 and 21
b. FTP is File Tuning Package, which tunes the file packages and communicates
on port 3399.
c. FTP is a proprietary file protocol that only allows the transmission of encrypted files to and from remote
systems and uses port 20.
OBJECTIVE UNDERSTANDI NG SERVER ROLES 2. 2
d f d f
You can assume you
are using SSL if your
web address starts with
https://, which is typical
when performing any
online transactions or
authentications.
14 CHAPTER 2: Understanding Server Rol es
AnAnswers
1. The port Alicia needs open for SharePoint is:
b. 443
2. The security protocol that encrypts web traffic is:
a. Secure Socket Layer, SSL
3. FTP is:
a. File Transport Protocol. It is a fast, application-level protocol widely used for copying files
to and from remote computer systems on a network using TCP/IP, such as the internet.
It communicates on ports 20 and 21.
Essential details
A port is an application-specific communications endpoint used by Transport Layer protocols of the
Internet Protocol Suite. A specific port is identified by its number, commonly known as the port number,
the IP address with which it is associated, and the protocol used for communication.
SSL supports authentication of client, server, or both, as well as encryptions during a communications session.
FAST TRACK HELP
http://www.iis.net
http://sharepoint.microsoft.com/en-us/Pages/default.aspx
FAST TRACK HELP
_______ /3
Understand remote access 15
OBJECTIVE UNDERSTANDI NG SERVER ROLES 2. 3
Understand remote access
SCENARIO: Craig works for Fourth Coffee as their network administrator. Fourth Coffee provides coffee and
coffee-making products throughout the United States. Fourth Coffee wants their salespeople, who manage their
own regions of the country, to be able to have access to their enterprise resource management application so
that they can update their sales numbers regardless of where they are located. This access needs to be secured.
Craig also needs to provide remote support for their sales force. Fourth Coffees server infrastructure is predomi-
nantly Microsoft Server
2008 R2 and their salespeople use Microsoft Windows
7 Professional on their laptops.
1. What is the most cost-effective and efficient method to provide remote support for their sales force?
a. enable Remote Assistance for all of the salespeople, which will enable Craig to remote into their systems
while they are logged on and simultaneously troubleshoot or monitor their activities. Remote Assistance
is already a feature of Windows 7 at no additional cost.
b. make sure all salespeople have their own mobile phones so that Craig can provide phone
support for the salespeople
c. purchase a third-party remote support software license for each laptop. This would require Craig to
retrieve all remote laptops for installation and training purposes.
2. What can Craig do to provide secure access to Fourth Coffees enterprise software?
a. have their sales people email all sales data three times a day to the corporate
headquarters where the data can be input
b. enable and configure Remote Desktop Services for Microsoft Windows Server 2008
R2 through Virtual Private Network (VPN) tunnel and push the enterprise software
as a Remote Application
c. install a third-party remote server on top of Windows Server 2008 R2
with additional licensing
3. By default, what communication port does Remote Desktop Protocol
communicate on?
a. 443
b. 445
c. 3389
R2
Remote Desktop
Services is an inherent
application in Microsoft
Windows Server 2008 R2 and the
Remote Desktop Client is an
inherent service on Microsoft
Windows 7 Professional.
16 CHAPTER 2: Understanding Server Rol es
Answers
1. The most cost-effective and efficient method is to:
a. enable Remote Assistance for all of the salespeople, which will enable Craig to remote into their
systems while they are logged on and simultaneously troubleshoot or monitor their activities
2. To provide secure access Craig can:
b. enable and configure Remote Desktop Services for Microsoft Windows Server 2008 R2 through
Virtual Private Network (VPN) tunnel and push the enterprise software as a Remote Application
3. By default, Remote Desktop Protocol communicates on port:
c. 3389
Essential details
Remote Desktop is used for administration. Remote desktop is available on
Windows 7 and Server 2008 R2 by enabling it through Advanced System
Settings. It allows a user to remote into a system when enabled and take
control.
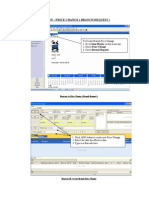
Right-click Computer->Properties
Select Remote Settings on the left
Click the radio button to Allow Connections Only From Computers
Running Remote Desktop With Network Level Authentication as shown here:
Remote Assistance is a technology in Windows that enables Windows users to help
each other over the internet.
FAST TRACK HELP
http://www.microsoft.com/systemcenter/appv/default.mspx
http://technet.microsoft.com/en-us/windowsserver/ee236407.aspx
FAST TRACK HELP
elp elp
_______ /3
Understand f il e and print ser vi ces 17
OBJECTIVE UNDERSTANDI NG SERVER ROLES 2. 4
Understand le and print services
SCENARIO: Kern Sutton is the regional systems administrator for Wingtip Toys. The company has asked Kern to
upgrade their existing le server to Microsoft Windows Server 2008 R2. They also want Kern to congure the new
server to support print sharing as well. Kern eagerly accepts the challenge as he is excited to work with the new
operating system. Kern must secure both the shares and folders using the appropriate rights and permissions.
Kern discovers that this isnt an old-time Windows Server!
1. What Role(s) are required for Kern to accomplish his task?
a. Microsoft File and Printer sharing
b. File Services Role and Print and Document Services Role
c. File Services for MacIntosh
2. Is there an alternate method to install the File Services Role?
a. No, the role must be installed through the Add Roles Wizard
b. Yes, when Kern initially shares a folder, the Role will be added automatically
c. Yes, through a separate download from Microsoft
3. What tasks can be accomplished through the Print Management console?
a. deploy printers and print servers, manage printers, update drivers, and manage
print queues
b. manage print queues only
c. remove a printer from a users desktop
The Print
Management console
is a single landing zone
for all print management
needs.
18 CHAPTER 2: Understanding Server Rol es
Answers
1. Required Roles include:
b. File Services Role and Print and Document Services Role. Microsoft File and Printer service has now
been split into separate roles.
2. There is an alternate method:
b. yes, when Kern initially shares a folder, the Role will be added automatically. Adding the Role
through the Add Role Wizard is a preferred method of installation
3. The tasks that can be accomplished include:
a. deploy printers and print servers, manage printers, update drivers, and manage print queues
Essential details
A print server is a workstation that is dedicated to managing printers on a network. The print server can be
any station on the network.
NTFS rights apply to a folder or file regardless of how it is being accessed. Share permissions apply to the
resource when it is being accessed over the network.
The effective right of a resource being accessed over the network is based on the most restrictive permission
or right that is applied.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc770906(WS.10).aspx
http://technet.microsoft.com/en-us/library/dd759058.aspx
FAST TRACK HELP
_______ /3
Understand ser ver vir tuali zati on 19
OBJECTIVE UNDERSTANDI NG SERVER ROLES 2. 5
Understand server virtualization
SCENARIO: Molly Dempseys company, Northwind Traders, has more than 50 servers that are due to be upgraded.
Molly must determine the most cost-effective method of upgrading these servers. She has several options that
she must consider to make her decision. Northwind Traders has several older applications that are part of the
problem because they are only supported on the existing legacy operating systems. Molly also has a desire to
simplify her backup and disaster recovery procedures. Molly is considering virtualization to address these various
needs.
1. What appears to be Mollys best solution for the legacy applications?
a. only upgrade the hardware the applications are running on and install the legacy operating system
b. virtualize the legacy systems by performing a physical to virtual migration and run these systems on a
host Microsoft Hyper-V solution
c. keep the legacy systems running on their legacy operating systems on the legacy hardware, which
would ensure her legacy at this current, soon-to-be legacy employer
2. How can virtualization help simplify Mollys disaster recovery needs?
a. allows for application portability and flexibility across hardware platforms
b. cant help simplify her situationit will only complicate her procedures
c. can help simplify her proceduresthere isnt a need for disaster recovery when
utilizing virtualization technologies because they perform virtual backups
3. What are the additional benefits that Northwind Traders will realize when they
implement virtual technologies?
a. no additional benefits will be realized by using server virtualization
b. they will not benefit from server virtualization but rather lose out as the costs
of virtualization are dramatically underestimated
c. they will be able to consolidate their servers and reduce the number of physical
computers they will have to support
Most entry-level
server virtualization
platforms are free to the
end user. Costs are added
if the user requires
additional management
features.
20 CHAPTER 2: Understanding Server Rol es
Answers
1. Mollys best solution is to:
b. virtualize the legacy systems by performing a physical to virtual migration and run these sys-
tems on a host Microsoft Hyper-V solution
2. Virtualization can help simplify her disaster recovery needs by:
a. allowing for application portability and flexibility across hardware platforms. The system
archives the virtual system or file. The virtual system is not dependent on the hardware platform
it is running on.
3. The additional benefits that Northwind Traders will realize when they implement virtual technologies
include:
c. they will be able to consolidate their servers and reduce the number of physical computers they
will have to support. They will also reduce their carbon footprint because of reduced energy needs,
making their company a greener company. They can also reduce the number of people needed
to support their large number of servers.
Essential details
Server virtualization is the ability to run a full operating system on a platform so that the operating system
performs as though it were a real system.
Physical to virtual (P2V) is a process in which an existing physical computer is
converted into a virtual machine. Virtual to physical (V2P) is a process in which an
existing virtual machine is converted or deployed to one or more physical computers.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc753637(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc816638(WS.10).aspx
FAST TRACK HELP
an
ters. t
_______ /3
3
Understanding Active
Directory
IN THI S CHAPTER
3.1 Understand accounts and groups
3.2 Understand organizational units (OUs) and containers
3.3 Understand Active Directory infrastructure
3.4 Understand group policy
Understand accounts and groups 23
OBJECTIVE UNDERSTANDI NG ACTI VE DI RECTORY 3. 1
Understand accounts and groups
SCENARIO: Sara Davis is the helpdesk manager for Wide World Importers (WWI). WWI has asked Sara to provide
procedures and training for her helpdesk staff that will allow them to be more procient at normal day-to-day
administrative tasks, including creating domain and local user accounts, managing group memberships, and
understanding whats under the hood as it relates to managing user accounts. This includes technical details
such as the location of the user database for both local and domain systems, acceptable naming conventions, and
what characters are not allowed.
1. What is the name and location of the file that contains the local user and group objects?
a. userDB: c:\userdb.mdb
b. Security Accounts Manager Database: %systemroot%\system32\config
c. ntds.dit: c:\windows\ntds
2. Which of the following is an unacceptable user account name?
a. Abercrombie?kim
b. Mu.Han
c. MPatten
3. What is the rule related to nesting domain and local groups?
a. domain groups can contain local groups, but local groups cannot contain domain
groups
b. domain groups and local groups cannot be nested
c. local groups can contain domain groups, but domain groups cannot contain
local groups
The local users and
groups security
boundary is limited
to the system they are
created on.
24 CHAPTER 3: Understanding Acti ve Directory
Answers
1. The name and location of the file that contains the local user and group objects is:
b. Security Accounts Manager Database: %systemroot%\system32\config. The Active Directory
Domain Services database is named ntds.dit. The file is located by default in %systemroot%\ntds.
2. An unacceptable user account name is:
a. Abercrombie?kim
/ \ [ ] : ; | = , + * ? < > @ are not accepted characters for user accounts.
3. The rule related to nesting domain and local groups is:
c. local groups can contain domain groups, but domain groups cannot contain local groups
Essential details
The Security Accounts Manager (SAM) is a database present on servers running Windows Server 2008 R2
that stores user accounts and security descriptors for users on the local computer.
The following steps create a local user account and add it to the Power Users group through the command
line:
Start->All Programs->Command Prompt
Type: net user WHarp myP@ssword /fullname:Walter Harp /comment:A member of the
Power Users Group /logonpasswordchg:yes /add
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc756748(WS.10).aspx
http://support.microsoft.com/kb/909264
FAST TRACK HELP
_______ /3
Understand organi zati onal uni ts (OUs) and containers 25
Delegation of
control grants specic
admini-strative tasks
such as resetting passwords
to individual users or groups
without making them
domain administrators.
OBJECTIVE UNDERSTANDI NG ACTI VE DI RECTORY 3. 2
Understand organizational units (OUs) and containers
SCENARIO: Victoria Flores is the Directory Services administrator for Humongous Insurance. Humongous
Insurance is a large insurance company with ofces throughout the country. The IT needs and wishes of various
branches vary greatly and it is a challenge to manage it all.
The company wants to design its Active Directory structure to better suit these various needs and allow for easier
management of the various computers and departments. They have asked Victoria to create an organizational
unit design that will t their goals. One of their main goals is to create a model with which they can maintain
consistency and usability. They also want to be able to manage each department without granting particular
users complete administrative privileges.
1. What can Victoria do to solve the administration issue?
a. give the domain administrator password to the employee assigned to manage each departmental
organizational unit
b. simply perform all the administrative tasks herself
c. delegate control to the employee assigned to manage each departmental organizational unit and grant
specific administrative rights for that container
2. How can an organizational unit be created?
a. Active Directory Users and Computers, PowerShell, command line,
Active Directory Administrative Center
b. User Manager for Domains
c. organizational units can only be created through Active Directory
Users and Computers
3. Which command creates an OU called Marketing in the domain
HUMONGOUS.LOCAL?
a. dsadd ou ou=Mar ket i ng, dc=humongous, dc=l ocal
b. makeou=mar ket i ng. humongous. l ocal
c. ou=mar ket i ng, dc=humongous, dc=l ocal
26 CHAPTER 3: Understanding Acti ve Directory
Answers
1. Victoria can solve the administration issue if she:
c. delegates control to the employee assigned to manage each departmental organizational unit
and grants specific administrative rights for that container
2. An organizational unit can be created through:
a. Active Directory Users and Computers, PowerShell, command line, Active Directory Administra-
tive Center
3. An OU is created with the command:
a. dsadd ou ou=Marketing,dc=humongous,dc=local
Essential details
Organizational units are Active Directory containers into which you can place users, groups, computers, and
other organizational units.
Organizational units can be structured to meet various needs. They can be structured based on geographic
location, business structure (departments), organizational need, specific role or function, operating system
version, or platform and any combination mentioned.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc758565(WS.10)
http://technet.microsoft.com/en-us/library/cc732524.aspx
FAST TRACK HELP
_______ /3
Understand Acti ve Director y infrastructure 27
OBJECTIVE UNDERSTANDI NG ACTI VE DI RECTORY 3. 3
Understand Active Directory infrastructure
SCENARIO: Andrew Ma is the systems administrator for Coho Winery. Recent changes in the business and
in advertising strategies have increased the popularity of Coho wines beyond expectations. Because of the
meteoric rise of Cohos sales, the company has decided to migrate from a workgroup network to a centrally
managed domain model using Microsoft Windows Server 2008 R2 Active Directory Domain Services.
This IT change will allow Andrew to utilize several benets of a domain, including organizing network objects,
applying group policies to manage desktop computers, and managing security. Andrew has decided to have
multiple domain controllers for redundancy, as well as to split operations roles. The new organization system will
support future company growth.
1. What is a benefit of having a domain model network as opposed to a workgroup?
a. there isnt any benefitit is cost-prohibitive. It is easier to manage user accounts on 20 different
computers than a centrally managed option
b. it allows for a centrally managed system where employees authenticate to the domain rather than to
each individual workstation
c. the only benefit is that it is easier to secure than a workgroup model
2. What should Andrew do to determine which domain controller maintains
the operations role of RID master?
a. contact the previous system administrator
b. open Active Directory Users and Computers, right-click his domain, and select
Operation Masters
c. create a batch file that will query each domain controller to determine
who is responsible for the RID master
3. What domain controller maintains all five operations roles by default?
a. the first domain controller in the forest
b. operations roles are automatically transferred to subsequent domain controllers
as they are added to the forest
c. the domain controller is selected by the administrator when the system is being promoted
Migrating from a
workgroup model to a
domain model allows for ease
of administration. It creates a
centrally managed database that
can be replicated across domain
controllers which adds fault
tolerance.
28 CHAPTER 3: Understanding Acti ve Directory
_______ /3
Answers
1. The primary benefit of a domain model network is:
b. having a centrally managed system where employees authenticate to the domain rather than to
each individual workstation. This allows for better security policies and network management.
2. Andrew can determine which domain controller maintains the operations role of RID master if he
b. opens Active Directory Users and Computers, right-clicks his domain, and selects Operation
Masters
3. The domain controller that maintains all five operations roles by default is:
a. the first domain controller in the forest. The operations roles have to be transferred manually when
the additional domain controllers are promoted in the forest. NTDSUTIL is a command-line utility that
can accomplish this task.
Essential details
A domain is a unit of replication.
A domain controller is a server that is running a version of the Windows Server operating system and has
Active Directory Domain Services installed.
In a domain model, the user authenticates once to the domain, which maintains all information
about other objects in the domain. Compare this to a workgroup model in which the
administrator has to duplicate user accounts on any workstation that is sharing resources.
This means that a single user would have to have a user account created for on each
computer she accesses.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc780856(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc755450(WS.10).aspx
FAST TRACK HELP
Understand group poli cy 29
OBJECTIVE UNDERSTANDI NG ACTI VE DI RECTORY 3. 4
Group Policy
settings apply to
users regardless
of the workstation
they authenticate to.
Understand group policy
SCENARIO: Benjamin Harris works for Wingtip Toys as
their desktop administrator. Bens primary function is
desktop management and support of the companys
desktop environment. His main goal is to have a quiet
day at his desk so he can research new ideas for Wingtip
Toys. He has several tools at his disposal to accomplish
this but his most important tool is his use of group
policies on their domain.
Some issues have arisen in various departments:
Employees want to have customized desktops and
features on their systems and still maintain consis-
tency with Wingtip Toys
Administrators at Wingtip Toys want some primary
settings to remain consistent on all systems in the
company but want to allow each department to
have individual settings that will help them per-
form their jobs more efficiently
1. Wingtip Toys only want password policies
applied to their Testing Division. Ben wants to
create a Group Policy Object for the Testing orga-
nizational unit that sets these password policies.
Will this accomplish what Wingtip Toys wants?
a. yes, the password policy set at the organiza-
tional unit level will only apply to the users
and computers in that OU
b. yes, the password policy will apply to the
users in the Testing division no matter what
computer they log onto
c. no, password policies can only be applied at
the domain level
2. Ben wants to see if the policies he set are in
effect. He does not want to reboot or wait
for the system to refresh automatically in
90 minutes. What command can he issue to
force the application of group policies?
a. gpupdat e / NOW
b. gpedi t . msc / updat e
c. gpupdat e / f or ce
3. Ben has a policy that sets his homepage in
Internet Explorer to open to http://wingtip-
toys.com. The testing department has their
homepage in IE set to open to http://testing.
wingtiptoys.com. What will the homepage
display when Ben logs into
a testing department
workstation?
a. http://wingtiptoys.com
.User Policy settings
follow the user
b. http://testing.wingtiptoys
.com. He is authenticating
to a testing department
station
c. Internet Explorer default
MSN homepage. He is not
a Testing user and its not
his workstation
30 CHAPTER 3: Understanding Acti ve Directory
_______ /3
Answers
1. Wingtip Toys want password policies applied only to their Testing division:
c. No, password policies can only be set and applied at the domain level. Password policies can only
be set and applied at the domain level. The user has already authenticated by the time organizational
unit policies are applied.
2. The command to force the application of group policies is:
c. gpupdate /force
3. When Ben logs into a testing department workstation his homepage will display:
a. http://wingtiptoys.com. User Policy settings follow the user
Essential details
A Group Policy is an infrastructure that enables administrators to implement specific configurations for users
and computers.
Winlogon is a component of the Windows operating system that provides interactive logon support.
Winlogon is the service in which the Group Policy engine runs.
Group Policy Preference enables administrators to manage drive mappings, registry settings, local users
and groups, services, files, and folders.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc779838(WS.10).aspx
http://support.microsoft.com/kb/94372
http://www.microsoft.com/downloads/details
.aspx?FamilyID=18c90c80-8b0a-4906-a4f5-ff24cc2030fb&displaylang=en
FAST TRACK HELP
4
Understanding
Storage
IN THI S CHAPTER
4.1/4.2 Identify storage technologies; Understand RAID
4.3 Understand disk types
Understand Windows application deployment methods
SCENARIO: Stepan spends much of his free time in the outdoors, camping, hiking, and canoeing. Whenever
school is not is session, he tries to take at least one trip. He has developed two applications to help him enjoy
his hobbies. The rst application helps him log his activities, downloads data from his GPS unit, and automatically
posts updates to his favorite social media websites. The second is a relatively simple application for planning trips;
it helps him organize his maps, plan the supplies hell need, and keep track of weather reports in the days before
he leaves. Both programs are Windows Forms applications.
He has always run the applications from his own computer, but now that his friends have seen how well they
work, he would like to distribute copies for others to enjoy.
1. The planning application is newer and Stepan is still making frequent changes. Which deployment
option checks for updates before installing the application?
a. ClickOnce
b. Windows Installer
c. Both deployment options automatically check for updates.
2. The log application interfaces with a GPS and must install a device driver upon
deployment. Which option is best suited for this application?
a. ClickOnce
b. Windows Installer
c. Neither deployment option can install a device driver.
3. Which option will allow Stepan to distribute his applications via USB drives?
a. ClickOnce
b. Windows Installer
c. Both deployment options can be distributed via USB drive.
Answers
1. If Stepan wants the installer to check for updates, the deployment method he should use is:
A. ClickOnce
I denti f y storage technol ogi es; Understand RAI D 33
OBJECTIVE UNDERSTANDI NG STORAGE 4. 1/4. 2
The amount of drive
space used for
redundancy is 1/n (total
drive space) where n is the
total number of drives in
the array.
Identify storage technologies; Understand RAID
SCENARIO: Howard Gonzalez is the systems administrator for Humongous Insurance. The company is responsible
for protecting the property of hundreds of thousands of clients across 14 states. Because of the time-critical nature
of the data stored by Humongous Insurance, Howard is researching his best alternative to ensure that the customer
service representatives have access to their clients information whenever they need it. Server downtime is not an
option for Humongous Insurance, where customer satisfaction is top priority. Howard is considering various form of
Redundant Array of Independent Disks (RAID), possibly congured in a Network Attached Storage (NAS).
1. What is the minimum number of hard drives required if Howard wants to configure
a RAID 5 solution?
a. 5
b. 2
c. 3
2. What is a benefit of NAS over Storage Area Network (SAN)?
a. There isnt any advantage; they are equal
b. NAS provides file serving without the need for a server
c. NAS benefits from being attached to a server on the network to provide
file abstraction
3. Howard is configuring a server with RAID 5. He is using four 750-GB hard drives
in his RAID array. How much available free space will Howard have after
RAID is configured?
a. 750 GB
b. 2,250 GB
c. 2,250 TB
34 CHAPTER 4: Understanding Storage
Answers
1. The minimum number for hard drives required to configure a RAID 5 solution is:
c. 3
2. A benefit of NAS over Storage Area Network (SAN) is that:
b. NAS provides file serving without the need for a server
3. After RAID is configured Howard will have:
b. 2,250 GB of free space (3000-(3000)=2,250)
Essential details
Network-attached storage (NAS) is file-level computer data storage connected to a computer network
providing data access to heterogeneous clients.
NAS does not require a server to provide services. SAN requires a server to provide file abstraction services.
NAS reduces the number of servers on a network.
A Redundant Array of Independent Disks (RAID) is a data storage method in which data is distributed
across a group of computer disk drives that function as a single storage unit.
Available free space after RAID 5 is configured =Total drive space-1/n (total drive space) 3000-(3000)=2,250
FAST TRACK HELP
http://msdn.microsoft.com/en-us/library/ms184252(SQL.90).aspx
FAST TRACK HELP
_______ /3
Understand disk t ypes 35
OBJECTIVE UNDERSTANDI NG STORAGE 4. 3
Self-healing NTFS
does not protect
against hardware
malfunctions.
Understand disk types
SCENARIO: Luka Abrus works for City Power and Light as a systems administrator. Luka wants to increase the data
availability for three servers without having to rebuild them from scratch and without incorporating a great deal
of cost by purchasing array controllers. Luka also would like to be able to use data on one system and transport
it to another system and have it appear as another hard drive.
1. What can Luka do to increase his server data availability without additional costs of an array
controller or rebuilding each server?
a. make sure the servers are always on
b. add another physical drive to each server, convert the drives from basic disks to a dynamic disk,
and establish a mirror (RAID 1) between the two drives
c. make sure that his backups are running every night to ensure that he can restore data in the event
of a failure
2. What can Luka do to be able to transport data from one system to another and have
it appear as a separate drive?
a. create a virtual hard disk (VHD) to store the data
b. carry an external drive and attach it from one system to another
c. compress the data and email the data to himself
3. What advantages will Luka experience when using self-healing NTFS
in Microsoft Windows Server 2008 R2?
a. continuous data availability
b. no concerns about physical drive failure
c. no need to install antivirus software
36 CHAPTER 4: Understanding Storage
Answers
1. To increase his server data availability without additional costs of an array controller or rebuilding each
server, Luka can:
b. add another physical drive to each server, convert the drives from basic disks to a dynamic disk
and establish a mirror(RAID 1) between the two drives
2. To be able to transport data from one system to another and have it appear as a separate drive, Luka can:
a. create a virtual hard disk (VHD) to store the data. The vhd can be stored to a network share and then
be utilized from one system to another and mounted as a virtual drive. A VHD can be mounted to any
Windows system and appear as a separate physical drive
3. When using self-healing NTFS in Microsoft Windows Server 2008 R2, Luka will experience the advantage of:
a. continuous data availability. Self-healing NTFS attempts to correct corruptions of the file system with-
out requiring the use of chkdsk.exe
Essential details
A dynamic disk is a physical disk that can use the master boot record (MBR) or GUID partition table (GPT)
partitioning scheme and has the ability to create fault tolerant volumes (mirrored and RAID-5 volumes).
A mount point is an association between a volume and a directory on another volume.
Microsoft virtual hard disk (VHD) file format specifies a virtual machine hard disk
that can reside on a native host file system encapsulated within a single file.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc938934.aspx
http://windows.microsoft.com/en-US/windows-vista/
What-are-basic-and-dynamic-disks
http://technet.microsoft.com/en-us/library/cc758035(WS.10).aspx
FAST TRACK HELP
_______ /3
5
Understanding
Server Performance
Management
IN THI S CHAPTER
5.1 Identify major server hardware components
5.2 Understand performance monitoring
5.3 Understand logs and alerts
2. If he wants to install a device driver he should use:
B. Windows Installer
3. Stepans applications can be distributed via USB drives because:
C. both deployment options can be distributed via USB drive.
Essential details
The .NET Framework provides two primary technologies for deploying applications: ClickOnce and Windows
Installer.
Both technologies:
provide a user interface to guide users through the installation process.
allow for the creation of Start Menu and desktop shortcuts.
can be distributed by a website or by removable media.
can register file types.
The advantages and features of ClickOnce include:
There is minimal user interaction during the installation process.
The technology automatically checks for updates.
Updates do not require complete reinstallation of application.
Features of Windows Installer include the use of a wizard that assists the user with
installation and the flexibility to handle a variety of installation situations.
In general, ClickOnce is simpler and is ideal for applications that are updated frequently.
Windows Installer provides more control over the installation process and
is flexible enough to handle unusual or complicated setup requirements.
FAST TRACK HELP
http://msdn.microsoft.com/en-us/library/y18k4htb.aspx
http://msdn.microsoft.com/en-us/library/e2444w33.aspx
FAST TRACK HELP
I denti f y maj or ser ver hardware components 39
OBJECTIVE UNDERSTANDI NG SERVER PERFORMANCE MANAGEMENT 5. 1
Identify major server hardware components
SCENARIO: Proseware Inc. has recently purchased land to expand their business center. A great deal of thought
and research must go into planning for the technology needs of a business the size of Proseware.
Cari has been the server administrator at Proseware for several years and has a deep understanding of the
technology needs related to the server components. Proseware has asked Cari to submit a plan for the
redesigned datacenter that will ensure data redundancy and server availability. The overall business plan
is dependent upon a dependable data system.
1. What technology can Cari implement that will allow for the replacement of server components
while the servers are still running?
a. the technology does not exist
b. component live swappable
c. hot swappable/pluggable
2. What can Cari implement that will protect the servers from a power outage and allow the systems
to be shut down gracefully in the event of a power loss?
a. uninterruptable power supply (UPS)
b. a script that will shut down the server when the datacenter loses power
c. several surge suppressors for the servers
3. Why is it important for Cari to have climate control within the datacenter?
a. to be comfortable when she is working in the datacenter
b. to prevent servers from overheating
c. it is irrelevant servers are configured with their own cooling systems
ASHRAE recommends
a temperature range
of 61 to 75 degrees
Fahrenheit and a humidity
range of 40 to 55 percent.
40 CHAPTER 5: Understanding Server Performance Management
Answers
1. To allow for the replacement of server components while the servers are still running, Cari can implement:
c. hot swappable/pluggable. Various hot swappable components include hard disks and fans.
2. To protect the servers from a power outage and allow the systems to be shut down gracefully in the event
of a power loss, Cari can implement:
a. uninterruptable power supply (UPS). A UPS only protects against power outages and is used
to gracefully shut the systems down in the event of an extended power loss
3. It is important for Cari to have climate control within the datacenter:
b. to prevent servers from overheating
Essential details
Hot pluggable technology includes replacing system components without shutting down the system.
Memory is a hardware device where information can be stored and retrieved.
A Network Interface Card (NIC) is a hardware device that handles an interface to a computer network and
allows a network-capable device to access that network.
FAST TRACK HELP
http://en.wikipedia.org/wiki/Hot_swapping
http://upload.wikimedia.org/wikipedia/en/2/29/Chassis-Plans-Rack.jpg
FAST TRACK HELP
_______ /3
Understand performance moni toring 41
OBJECTIVE UNDERSTANDI NG SERVER PERFORMANCE MANAGEMENT 5. 2
Understand performance monitoring
SCENARIO: Cliff Majors works for Southridge Video as a systems administrator. Southridge Video began as a
start-up business in southern Georgia just a few years ago and its popularity has skyrocketed; Southridge has
a unique ability to anticipate customer needs and provide services before customers are even aware that they
would nd the services valuable.
A while ago the company introduced a service for customers to rent videos over the internet and stream the
movies to their computers or internet-capable devices. In spite of their best planning and anticipation of prob-
lems, calls have come in from the customers complaining that the quality of the video is poor or that the videos
just arent available.
1. Cliff attempted to close a program on one of the video servers; however the application did not
respond. What application can he open to end that process?
a. File Manager
b. Task Manager
c. Command Prompt
2. Cliff wants to compare the performance reports he created when he initially
deployed the video servers. What application does he need to launch
to create a comparison report?
a. Network Monitor
b. netstat
c. Performance Monitor
3. Cliff is analyzing Performance Monitor and adds a counter that tracks page
file/usage and hits. Cliff notices that the page file is being accessed continuously.
What can Cliff do to solve this issue?
a. add more RAM
b. adjust the size of the page file
c. move the page file to another physical drive on the system
Continuous page
le hits are a result
of a system not having
enough RAM.
42 CHAPTER 5: Understanding Server Performance Management
Answers
1. To end a process that cannot be closed in the usual manner, Cliff can open the:
b. Task Manager
2. To create a comparison report, he must launch the:
c. Performance Monitor. It is important to create a baseline performance report using Performance
Monitor when deploying a system. This allows the administrator to have a report to compare against.
The reports can be overlapped within Performance Monitor to have a visual comparison.
3. To solve the problem of continuous page file hits, Cliff should:
a. add more RAM
Essential details
A page file is a hidden file on the hard disk that operating systems use to hold parts of programs and data
files that do not fit in memory.
A process is a program or part of a program.
Performance is the measure of how quickly a computer completes application and system tasks.
FAST TRACK HELP
http://support.microsoft.com/kb/323527
http://technet.microsoft.com/en-us/library/cc771692(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc755081(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc749249.aspx
FAST TRACK HELP
_______ /3
Understand l ogs and al er ts 43
OBJECTIVE UNDERSTANDI NG SERVER PERFORMANCE MANAGEMENT 5. 3
Understand logs and alerts
SCENARIO: Walter Felhofer manages the network at Graphic Design Institute. He has been monitoring the
network for several months to better understand the trafc variations. The network performance seems to vary
greatly and Walter suspects a variety of causes ranging from the time-of-day use to events that coincide with
special promotions and cyclical events. Walter keeps this historical data as it relates to the systems performance.
He reviews this data on a regular basis as well as reviewing the data in comparison mode because he knows that
it contains details that will be valuable for justifying future technology acquisitions and creating business plans.
1. What benefit can Walter gain by maintaining a historical record of the systems performance?
a. use of the data to justify future upgrades as well as to identify performance trends throughout the year
b. provide performance documentation if a supervisor asks for it
c. there is no benefit to keeping a historical record of your systems performance because technology
changes so frequently
2. Walters job keeps him very busy. He is unable to watch performance logs and data all day long.
What can Walter do so he can perform his other day-to-day tasks and not miss
any major performance issues?
a. hire an intern to watch performance monitor and page him whenever
something goes wrong
b. create a Performance Alert that will send a network message, write an event log,
or run a program when certain criteria are met
c. remote into the systems periodically to check performance logs, regardless
of whether he is busy
3. What is the default location for system performance logs?
a. %systemroot%\logs
b. #system#\perflogs
c. %systemdrive%\PerfLogs
Performance
monitoring is crucial
for real-time system
performance but is also
important for scaling
future systems and
upgrades.
44 CHAPTER 5: Understanding Server Performance Management
Answers
1. By maintaining a historical record of the systems performance, Walter can:
a. use the data to justify future upgrades as well as to identify trends throughout the year.
2. To ensure that he doesnt miss any major performance issues, Walter can:
b. create a Performance Alert that will send a network message, write an event log, or run
a program when certain criteria are met.
3. The default location for system performance logs is:
c. %systemdrive%\PerfLogs
Essential details
Objects are specific resources in the Performance Monitor that can be measured.
Performance counters are measurements of system state or activity.
Use of the overlay mode is only available in the Performance Monitor when it is running in stand-alone mode
with comparison enabled:
Click Start->click in the Start Search box, type perfmon/sys/comp and press Enter.
The Performance Monitor will open in stand-alone mode with comparison enabled.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc738564(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc722414.aspx#BKMK_alert
FAST TRACK HELP
_______ /3
6
Understanding
Server Maintenance
IN THI S CHAPTER
6.1 Identify steps in the startup process
6.2 Understand business continuity
6.3 Understand updates
6.4 Understand troubleshooting methodology
I denti f y steps in the star tup process 47
OBJECTIVE UNDERSTANDI NG SERVER MAI NTENANCE 6. 1
Identify steps in the startup process
SCENARIO: Fourth Coffee has expanded its business to 20 new stores in neighboring states. The expansion meant
that the company had to expand its IT department and hire several new technicians. It is critical that all of the
new hires have knowledge and skills in maintaining the companys technology infrastructurethe success of the
company depends upon effective technology at every level of the business.
The CIO has asked the systems administrator, April Meyer, to provide training to her staff on Server 2008 R2.
She wants everyone to have a fundamental understanding of the boot process as well as some troubleshooting
techniques.
1. What command-line utility can April demonstrate to modify the boot configuration database?
a. bcdedit.exe
b. boot.ini
c. ntloader.exe
2. What does the Power-On Self Test (POST) do?
a. tests to see whether the power is on
b. performs initial hardware checks, verifies devices, and retrieves system
configurations from CMOS
c. calls programs such as autoexec.bat, config.sys, and win.ini
3. April want to demonstrate starting a computer in safe mode. What are the steps
to start a computer in safe mode?
a. access the system BIOS and configure it to start in safe mode
b. boot the installation media and select the safe mode option
c. remove all media and then press and hold the F8 key before the
Windows Logo appears
Safe mode starts
Windows with a
limited set of les
and drivers.
48 CHAPTER 6: Understandi ng Ser ver Mai ntenance
Answers
1. The utility that April can demonstrate to modify the boot configuration database is:
a. bcdedit.exe
2. The Power-on Self Test (POST):
b. performs initial hardware checks, verifies devices, and retrieves system configurations from
CMOS
3. To start a computer in safe mode:
c. remove all media and then press and hold the F8 key before the Windows Logo appears
Essential details
Power-On Self Test (POST) is a set of routines stored in a computers read-only memory (ROM) that tests
various system components such as RAM, the disk drives, and the keyboard to see whether they are properly
connected and operating.
The Master Boot Record (MBR) is the first sector of the first hard disk; it is a physically small but critical
element in the startup process on an x86-based computer.
To start a computer in safe mode remove all floppy disks, CDs, and DVDs from the computer and then
restart the computer.
If your computer has a single operating system installed, press and hold the
F8 key as your computer restarts.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc976730.aspx
http://technet.microsoft.com/en-us/library/bb457123.aspx
http://technet.microsoft.com/en-us/library/cc721886(WS.10).aspx
http://windows.microsoft.com/en-US/windows-vista/
Start-your-computer-in-safe-mode
FAST TRACK HELP
_______ /3
Understand business continui t y 49
Understand business continuity
SCENARIO: Rachel Valdes is developing a strategic information technology plan for her company, Northwinds
Traders. The main focus of this plan is to maintain business continuity by ensuring that critical business
functions will be available for customers and business partners. Her plan must ensure that the needs and
important activities of Northwinds customers, suppliers, regulators, and employees can be met in event
of an unforeseen technology problem or a natural or human-induced disaster. She needs to plan for
data redundancy as well as disaster recovery.
1. Northwinds Traders core infrastructure runs on Microsoft Windows Server 2008 R2. What inherent
application can they use to implement the data redundancy portion of their strategic plan?
a. Windows Server Backup
b. Active Directory Restore Mode
c. NTBackup.exe
2. What benefit does folder redirection offer?
a. allows administrators to direct folders to perform data backups and migrations
b. allows users and administrators to redirect the path of a folder to a new
location that can provide backup on a network share
c. converts a folder from one file system to another
3. Part of Rachels plan is to develop a disaster recovery plan. What is a disaster
recovery plan?
a. the process, policies, and procedures related to preparing for recovery
or continuation of critical technology after a natural or human-induced
disaster
b. a plan that dictates how to recover data and financial loss after a theft
c. a procedure meant solely for recovering lost data
A disaster recovery
plan is related to
any technology infra-
structure and should
be updated on a
regular basis.
OBJECTIVE UNDERSTANDI NG SERVER MAI NTENANCE 6. 2
50 CHAPTER 6: Understandi ng Ser ver Mai ntenance
Answers
1. To implement the data redundancy portion of Northwinds strategic plan they can use:
a. Windows Server Backup
2. The benefit offered by folder redirection is to:
b. allow users and administrators to redirect the path of a folder to a new location that can
provide backup on a network share. Folder redirection is a method that helps prevent users from
keeping important information on their local hard drives by redirecting it to another location
where it can be backed up for data redundancy.
3. A disaster recovery plan includes:
a. the process, policies, and procedures related to preparing for recovery or continuation
of critical technology after a natural or human-induced disaster
Essential details
Data redundancy is a property of some disk arrays that provides fault tolerance so that all or part of
the data stored in the array can be recovered in the case of disk failure.
Disaster recovery is the process, policies, and procedures related to preparing for recovery or continuation
of technology infrastructure critical to an organization after a natural or human-induced disaster.
Business continuity is the activity performed by an organization to ensure that critical
business functions will be available to customers, suppliers, regulators, and other
entities that must have access to those functions.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc778976%28WS.10%29.aspx
http://technet.microsoft.com/en-us/library/cc770266(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc753201.aspx
http://technet.microsoft.com/en-us/library/cc785306(WS.10).aspx
FAST TRACK HELP _______ /3
Understand updates 51
Understand updates
SCENARIO: Mark Patten is a network engineer with Tailspin Toys. Tailspin Toys has asked Mark to nd a way to
ensure that all of the systems on their network are updated on a regular basis. They also want Mike to discuss
updates with their software development team because developers sometimes run into issues with updates
conicting with their custom software while they are in development process. Tailspin Toys desktop systems range
from Windows XP to Windows 7, both 32-bit and 64-bit. They also have a mix of server operating systems running
Windows Server 2003 R2 through Windows Server 2008 R2. This variety of computers and systems within a single
organization is not unusual, but requires strong network administration skill on Marks part!
1. What can Mark do to streamline update management for Tailspin Toys?
a. configure Windows Software Update Services (WSUS) to download and deploy updates based
on his needs
b. arrive early every Wednesday before Tailspin Toys opens and perform Windows Updates
c. allow the users to run the updates whenever they see fit
2. What can Mark do to solve the issues he will run into with the software development team?
a. disable updates for the software development team
b. configure a separate WSUS group and put all of the software development
computers and servers in that group
c. isolate the software development team on a separate segment and allow
them to manage their own updates
3. What tool can Mark use to determine the security state in accordance with
Microsoft security recommendations?
a. Qchain.exe
b. Network Monitor
c. Microsoft Baseline Security Analyzer (MBSA)
Use MBSA to detect
common security
miscongurations and
missing security updates
on computer systems.
OBJECTIVE UNDERSTANDI NG SERVER MAI NTENANCE 6. 3
52 CHAPTER 6: Understandi ng Ser ver Mai ntenance
Answers
1. To streamline update management for Tailspin Toys, Mark can:
a. configure Windows Software Update Services (WSUS) to download and deploy updates based
on his needs
2. To solve the issues with the software development team, Mark can:
b. configure WSUS to have a separate group and put all of the software development computers
and servers in that group. He can schedule updates to be selectively applied to their system.
3. To determine the security state in accordance with Microsoft security recommendations, Mark can use:
c. Microsoft Baseline Security Analyzer (MBSA)
Essential details
A hotfix is a single package composed of one or more files used to address a problem in a product.
Update management is the process of controlling the deployment and maintenance of interim software
releases into production environments.
Service packs are cumulative set of hotfixes, security updates, critical updates, and updates since
the release of the product, including many resolved problems that have not been made available
through any other software updates
FAST TRACK HELP
http://technet.microsoft.com/en-us/wsus/default.aspx
http://technet.microsoft.com/en-us/library/cc700845.aspx
FAST TRACK HELP
_______ /3
Understand troubl eshooting methodol ogy 53
OBJECTIVE UNDERSTANDI NG SERVER MAI NTENANCE 6. 4
Understand troubleshooting methodology
SCENARIO: Recent changes in the network congurations at Coho Winery have been successfully implemented.
Andrew Ma, the systems administrator, is pleased with his ability to organize network objects, apply group policies
to manage desktop computers, and manage security, but the changes have brought about the need to refresh the
skills of the helpdesk team.
Jeff Wang is responsible for updating the skills of the current team and training the new helpdesk hires at Coho
Winery. The helpdesk team is in charge of troubleshooting various issues that come in on a day-to-day basis from
the local winery and their remote winery locations located on both the east coast and the west coast.
Troubleshooting methodology is imperative for the success of the helpdesk team.
1. What is an example of a systemic problem?
a. a hard disk fails on a users computer
b. a worm propagates through the entire network
c. a users monitor will not turn on
2. What is the first tool in a Microsoft environment that should be used to
determine the time and type of problem a particular system may be having?
a. resource Monitor
b. task Manager
c. event Viewer
3. What application allows you to view all processes and either selectively
end a single process or the entire process tree?
a. resource Monitor
b. task Manger
c. msconfig.exe
Windows Resource
Monitor allows you
to view a process wait
chain and to end
processes that are
preventing a program
from working properly.
54 CHAPTER 6: Understandi ng Ser ver Mai ntenance
Answers
1. An example of a systemic problem is when:
b. a worm propagates through the entire network. Answers A and C are specific to a single systems
problems, not systemic.
2. The first tool in a Microsoft environment that should be used to determine the time and type of problem is:
c. Event Viewer
3. To view all processes an either selectively end a single process or the entire process tree, use the
a. Resource Monitor
Essential details
Event Viewer maintains logs about program, security, and system events on your computer.
Resource Monitor is a system tool that allows you to view information about the use of hardware
(CPU, memory, disk, and network) and software (file handles and modules) resources in real time.
Event viewer can be accessed through Start->Programs->Administrative Tools->Server manager->
Diagnostics->Event Viewer.
Default location for event logs:
%systemroot%\system32\config
FAST TRACK HELP
http://www.microsoft.com/resources/documentation/windows/xp/all/
proddocs/en-us/snap_event_viewer.mspx?mfr=true
http://technet.microsoft.com/en-us/library/cc766042.aspx
http://technet.microsoft.com/en-us/library/dd883276(WS.10).aspx
FAST TRACK HELP
_______ /3
MTA 98-366
NETWORKING
FUNDAMENTALS
1
Understanding
Networking
Infrastructures
IN THI S CHAPTER
1.1 Understand the concepts of the internet, intranet, and extranet
1.2A Understand local area networks (LANs)
1.2B Understand local area networks (LANs)
1.3A Understand wide area networks (WANs)
1.3B Understand wide area networks (WANs)
1.4 Understand wireless networking
1.5 Understand network topologies and access methods
Understand the concepts of the internet, intranet, and extranet 59
Understand the concepts of the internet, intranet, and extranet
SCENARIO: Before going to class, Sidney stops by Fourth Coffee for an iced coffee. The owner of Fourth Coffee,
Josh, stops to talk with Sidney because he knows that she enjoys solving computer problems. Josh asks Sidney
if she can help him manage Fourth Coffees server and wireless network.
Josh has a few projects for Sidney to start working on immediately. He would like to be able to access Fourth
Coffees server from his home and mobile phones. In addition, he is concerned about keeping his customers
computers safe from viruses and hackers. Also, Josh would like to provide internal company information such as
schedules and company policies to his employees.
Sidney thanks Josh and tells him that shell start working on his projects today right after class.
1. What will Sidney need to install for Josh to be able to access Fourth Coffees server from his home
and mobile phones?
a. a firewall
b. a VPN
c. an intranet
2. A firewall is to a network as:
a. a door is to a classroom
b. an eraser is to a pencil
c. a movie is to a screen
3. The primary goal of an intranet is to:
a. allow different businesses to share information
b. let users access different websites
c. provide company information to internal employees
OBJECTIVE UNDERSTANDI NG NETWORKI NG I NFRASTRUCTURES 1. 1
Even though a
browsers security
settings may be set high,
a rewall still should be
used.
60 CHAPTER 1: Understanding Net working Infrastructures
Answers
1. Josh wants to be able to access Fourth Coffees server from his home and mobile phones, so Sidney will
install a:
b. VPN. A VPN is a Virtual Private Network.
2. A firewall is to a network as:
a. a door is to a classroom. Firewalls keep computers safe and doors keep classrooms safe
and quiet so that students may study.
3. An intranets primary goal is to:
c. provide company information to internal employees. Extranets allow different business to share
information and the Internet lets users access different websites.
Essential details
VPNs create a private network and provide a secure tunnel across the Internet.
Firewalls can be hardware devices.
For security zones, keep the security level as high as possible.
In Microsoft
Internet Explorer
click Tools and then click Internet Options to set your security settings.
Mobile phones can be used to connect to a companys servers.
FAST TRACK HELP
http://msdn.microsoft.com/en-us/library/aa503420.aspx
http://support.microsoft.com/kb/174360
http://msdn.microsoft.com/en-us/library/ms953581.aspx
FAST TRACK HELP
_______ /3
Understand l ocal area net works (LANs) 61
OBJECTIVE UNDERSTANDI NG NETWORKI NG I NFRASTRUCTURES 1. 2A
Understand local area networks (LANs)
SCENARIO: Kim is studying to become an animator at the Graphic Design Institute. Michael, Kims friend from
class, asks Kim to study with him after class in the schools computer lab.
When Kim arrives in the lab she sees that Michael has already started his laptop and is connected to the schools
network. Kim starts her laptop and attempts to connect to the schools network when she realizes that she forgot
her wireless card. Kim tells Michael that shell have to run home and get her wireless card. Michael tells her that
she does not need to have her wireless card because she can connect directly to the network.
Kim asks Michael to show her how and he pulls out a cable and starts connecting it to her laptops internal, wired
NIC and explaining the steps.
1. What type of network is Kim trying to connect to?
a. WAN
b. LAN
c. PAN
2. To verify that Kims NIC (network interface card) works, Michael pings 127.0.0.1,
which is known as the:
a. loopback address
b. dynamic address
c. static address
3. A NIC is to a LAN as:
a. lyrics are to a song
b. a key is to a door
c. a movie is to a TV
When
troubleshooting
network connections,
use ping and ipcong.
62 CHAPTER 1: Understanding Net working Infrastructures
Answers
1. Kim is trying to connect to the schools:
b. LAN. A LAN is a Local Area Network.
2. To test Kims NIC Michael pings the:
a. loopback address. The loopback address is 127.0.0.1 and a successful ping verifies that the NIC works.
3. A NIC is to a LAN as:
b. a key is to a door. A key provides access through a door just as a computer is required to have a NIC to
access a LAN.
Essential details
LANs connect local computers together in a small geographical area.
Perimeter networks provide an extra layer of security for a companys internal network.
Computers connect to a LAN through a NIC (network interface card).
The loopback address is a reserved, static address of 127.0.0.1.
In Microsoft Windows
7, right-click Network and select Properties to view your network configuration.
FAST TRACK HELP
http://windows.microsoft.com/en-US/windows7/
Why-can-t-I-connect-to-a-network
http://support.microsoft.com/kb/169790
http://msdn.microsoft.com/en-us/library/ee494910.aspx
FAST TRACK HELP
_______ /3
Understand l ocal area net works (LANs) 63
Understand local area networks (LANs)
SCENARIO: Brian just graduated from his local community college in IT and started working for Adventure Works
as an IT Technician. His new boss, Annie, decides to send him on a business trip to Seattle where he will help set
up the computers in their new store.
When Brian arrives in Seattle he immediately checks into his hotel. He asks Erin, the hotel manager, if the hotel
has Internet access. Erin tells Brian that the hotel has both wired and wireless LAN connections available, which
he may use to access the Internet for free! Plus the hotel will be expanding Internet connectivity to the pool area
soon.
Brian is thrilled that the hotel provides free Internet access so that he can work at night, if necessary, to succeed
in his rst IT job.
1. When Brian connects a cable from his laptops NIC into an RJ45 jack he is connecting to the:
a. VLAN
b. wired LAN
c. wireless LAN
2. A VLAN is also called a:
a. logical network
b. internal network
c. external network
3. What will be Erins best solution for providing Internet connectivity
to the pool area?
a. expand the hotels wired network
b. expand the hotels wireless network
c. add a new WAN
OBJECTIVE UNDERSTANDI NG NETWORKI NG I NFRASTRUCTURES 1. 2B
Access points are
used to connect
wireless devices to
wired networks.
64 CHAPTER 1: Understanding Net working Infrastructures
Answers
1. Connecting a cable from a laptops NIC into a RJ45 jack allows Brian to use the hotels:
b. wired LAN. Wired LANs use cables and wireless LANs use radio, microwave, or infrared light.
2. Another name for a VLAN is:
a. logical network. VLANs segment broadcast traffic, which in turn increases network performance.
3. The best solution Erin should implement to expand Internet connectivity to the pool area is:
b. expand the hotels wireless network. A wireless LAN is easy to install in locations such as pool areas
and hotel lobbies where it can be difficult to run cables.
Essential details
VLANs are created on switches and help improve network performance.
Wired networks take time to install because wires need to be pulled to all of the connection jacks.
Wireless LANs are easy to expand to remote areas.
Security can be implemented in both wired and wireless LANs.
In Microsoft Windows 7, click the wireless network icon (on the right side of the taskbar) to view the available
wireless networks.
FAST TRACK HELP
http://windows.microsoft.com/en-US/windows7/
What-you-need-to-set-up-a-home-network
http://www.microsoft.com/protect/data/home/wireless.aspx
http://windows.microsoft.com/en-US/windows7/
View-and-connect-to-available-wireless-networks
FAST TRACK HELP
_______ /3
Understand wi de area net works ( WANs) 65
Always choose the
most efcient
IT solution to meet the
goals of a given
IT situation.
Understand wide area networks (WANs)
SCENARIO: Fourth Coffees business is booming! Josh, the owner, decides that now is the time to expand his
business. In the next month he will open one new location 30 miles south. In three months he will open another
location 30 miles north.
Josh wants to have a network between all three coffee shops. He is also concerned about security over the
existing VPN that provides him with access to the coffee shops network from his home and mobile phones.
When Josh shares his expansion plans and IT concerns with Sidney, his IT Consultant, she tells Josh that she has
the solutions. Sidney can easily expand the network because she has been studying WANs in her college classes.
1. To link all three of Fourth Coffees LANs together, Sidney will create a:
a. LAN
b. PAN
c. WAN
2. Between the original coffee shop and the first expansion location, Sidney decides to order
a private, dedicated line from the phone company known as:
a. a leased line
b. dial-up
c. ISDN
3. Sidney reassures Josh that the existing VPN is secure because the data
transferred across the public network is:
a. defragmented
b. encrypted
c. zipped
OBJECTIVE UNDERSTANDI NG NETWORKI NG I NFRASTRUCTURES 1. 3A
66 CHAPTER 1: Understanding Net working Infrastructures
_______ /3
Answers
1. Sidney will link all three of Fourth Coffees LANs together by creating a:
c. WAN. A WAN is a Wide Area Network which spans a large geographical area.
2. The private, dedicated line that Sidney orders from the phone company to connect the original coffee shop
and the first expansion location is called a:
a. leased line. The cost for a leased line depends upon the speed.
3. Fourth Coffees VPN is secure because the data transferred across the public network is:
b. encrypted. Encrypted data is scrambled, which protects it from unauthorized network clients.
Essential details
WANs can span completely around the worldfrom the United States to Australia!
A WAN link selection depends upon a companys goals for speed, availability, cost, and so on.
The Plain Old Telephone Service (POTS) is the oldest communications network.
For small companies, leased lines are a great WAN solution for connecting two locations.
Always protect data by encrypting it prior to transferring it across the Internet.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/bb727043.aspx
http://www.cisco.com/en/US/docs/internetworking/technology/handbook/
Intro-to-WAN.html
http://www.microsoft.com/windows/windows-7/features/bitlocker.aspx
FAST TRACK HELP
Understand wi de area net works ( WANs) 67
Every country has
its own unique
IT standards
and procedures.
Understand wide area networks (WANs)
SCENARIO: While attending college, Allie accepts an IT internship at Tailspin Toys in Denver, Colorado. She realizes
that this is an amazing opportunity for her to apply the skills that she has learned in her networking classes.
Richard, Tailspin Toys CIO, informs her that she will be working with Cristian, another IT intern, who works for
Tailspin Toys in Paris, France. Together they will determine the different types of WAN connections available
in the United States and France. Both locations will use point-to-point, dedicated, digital circuits between their
two local ofces within their respective countries. Speed for the digital circuits needs to be a minimum bandwidth
of 1 Mbps. In addition, Allie will need to research different home connection subscriptions available for Tailspin
Toys employees so that they can access the companys network via the Internet.
Allie and Cristian have fun challenges to solve!
1. Cristian determines that the point-to-point, dedicated, digital circuit that is available in Paris and
meets the minimum bandwidth of 1 Mbps is the:
a. E1
b. F1
c. T1
2. Allie determines that the United States equivalent to Cristians chosen
digital circuit is the:
a. E1
b. T1
c. U1
3. One home connection that Allie researches is a high-speed digital
communication technology over standard copper telephone wire called:
a. Cable TV
b. DSL
c. VPN
OBJECTIVE UNDERSTANDI NG NETWORKI NG I NFRASTRUCTURES 1. 3B
68 CHAPTER 1: Understanding Net working Infrastructures
_______ /3
Answers
1. In Paris, the point-to-point, dedicated, digital circuit that Cristian finds that meets the 1 Mbps minimum
bandwidth is the:
a. E1. The E1 is available through Europe and has a bandwidth of 2.048 Mbps.
2. In the United States, Allie determines that the equivalent digital circuit to the E1 is the:
b. T1. The T1 is available through the United States and has a bandwidth of 1.544 Mbps.
3. For home connections, Allie finds a high-speed digital communication technology that operates
over standard copper telephone wire, which is called:
b. DSL. DSL and Cable broadband Internet access technologies are popular choices for connecting home
or small business systems to the Internet.
Essential details
E1 and E3 are WAN connections available in Europe versus T1 and T3 for the United States.
DSL and Cable broadband Internet access technologies each have a corresponding modem.
Dial-up and ISDN have decreased in popularity while DSL and Cable have become more popular.
Even more WAN technologies exist, such as Frame Relay and ATM (Asynchronous Transfer Mode).
WAN links need to be optimized for efficient and fast performance.
FAST TRACK HELP
http://speedtest.emea.microsoftonline.com/
http://technet.microsoft.com/en-us/library/cc753764(WS.10).aspx
http://technet.microsoft.com/en-us/library/bb726928.aspx
FAST TRACK HELP
Understand wirel ess net working 69
Always secure a
wireless network
so that your data
stays safe.
Understand wireless networking
SCENARIO: Scott wants to set up a wireless network in his familys house for Internet connectivity. If he is successful
in creating a secure wireless network, his parents will pay for his rst semester in IT at college! To ensure his success,
Scott enlists his friend Susan, who has already set up a secure wireless network for her family.
Susan takes Scott on a shopping trip to their local electronics store to purchase the necessary equipment of a
wireless router which supports the most current wireless networking standards. The familys desktop system will
be wired and their new laptop will use wireless. The family uses DSL for their Internet connection.
After their shopping trip, Susan and Scott start setting up the wireless network. Will Scott succeed and earn a free
semester at college?
1. The most current wireless networking standard is:
a. 802.11n
b. 802.3
c. Bluetooth
2. To provide strong encryption protection without an enterprise authentication
server, Scott uses:
a. SSID
b. WEP
c. WPA-PSK
3. After the wireless network is completed, Scotts Dad sits on the deck and
successfully connects the laptop to the Internet through their new,
private, and secure:
a. Gigahertz
b. VLAN
c. Wi-Fi hotspot
OBJECTIVE UNDERSTANDI NG NETWORKI NG I NFRASTRUCTURES 1. 4
70 CHAPTER 1: Understanding Net working Infrastructures
_______ /3
Answers
1. The wireless networking standard that is most current is:
a. 802.11n. Two of the popular networking standards being used are 802.11g and 802.11n.
2. Strong encryption protection without an enterprise authentication server is provided through:
c. WPA-PSK. WPA-PSK is for personal/small business use; WPA-Enterprise, which uses authentication serv-
ers, is for an enterprise business.
3. On the deck, Scotts Dad connects his laptop to the Internet through their private and secure:
c. Wi-Fi hotspot. Public Wi-Fi hotspots are available in a variety of locations such as coffee shops,
schools, airports, and restaurants.
Essential details
Each of the wireless networking standards has different characteristics, such as speed, distance, frequency,
and so on.
Connect a WAP (wireless access point) to a wired router to provide connectivity between the wireless devices
and wired network.
WPA (Wi-Fi Protected Access) and WPA2 is more secure than WEP (Wired Equivalent Privacy).
WP-Enterprise and WP2-Enterprise are used in business environments and work with an
802.1X authentication server.
The 802.1X authentication method is used in business environments and requires
a certificate or smart card for network access.
FAST TRACK HELP
http://standards.ieee.org/getieee802/802.11.html
http://windows.microsoft.com/en-US/windows7/
Set-up-a-security-key-for-a-wireless-network
http://windows.microsoft.com/en-US/windows-vista/
What-are-the-different-wireless-network-security-methods
FAST TRACK HELP
Understand net work topol ogi es and access methods 71
It is important to
know the advantages
and disadvantages
of various topologies.
Understand network topologies and access methods
SCENARIO: During winter break from college, Jack decides to go skiing at Alpine Ski House, a small wilderness
resort. He brings his laptop to the resort and nds out that wireless Internet connectivity is not available to the
skiers. Alpine Ski House has only one desktop computer connected to the Internet.
Jack decides that this would be a great opportunity for him to apply the skills he is learning in class, so he asks to
speak with the owner of Alpine Ski House, Molly. She willingly discusses her networking dilemmas with Jack. Should
she implement a star or bus network topology? What is a mesh? Does she need a switch? Molly has too many
IT questions and not enough answers, so she decides to hire Jack.
Jack starts to design a network solution for Alpine Ski House between his skiing sessions.
1. The topology concerned with how data gets transferred within the network is the:
a. logical topology
b. mesh topology
c. physical topology
2. The topology considered more reliable because all of the nodes are connected
to each other is the:
a. bus topology
b. mesh topology
c. star topology
3. What topology should Jack choose for Mollys network?
a. bus
b. ring
c. star
OBJECTIVE UNDERSTANDI NG NETWORKI NG I NFRASTRUCTURES 1. 5
72 CHAPTER 1: Understanding Net working Infrastructures
_______ /3
Answers
1. Within the network, the topology that deals with how data gets transferred is the:
a. logical topology. The logical topology works with the physical topology, which is concerned with how
the devices are physically connected together.
2. The topology where all the nodes are connected to each other to form a reliable network is the:
b. mesh topology. Mesh topologies contain redundant wiring that provides multiple paths to the same
destination.
3. For Mollys network at Alpine Ski House, the topology Jack should choose is the:
c. star. The star is the one of the most popular topologies implemented today because of its low cost and
ease of installation.
Essential details
Bus topologies were popular along with coaxial cable.
Mesh topologies are more expensive because of the redundant wiring.
In star topologies a switch is usually used as the central device along with twisted pair cable.
Ring topologies are used as backbones for large networks with fiber cable and may contain redundant rings.
CSMA/CD is similar to a chat room, while CSMA/CA (Collision Avoidance) is similar
to a classroom.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/bb632621.aspx
http://www.cisco.com/en/US/docs/internetworking/technology/
handbook/Intro-to-LAN.html
http://www.giac.org/resources/whitepaper/network/32.php
FAST TRACK HELP
2
Understanding
Network Hardware
IN THI S CHAPTER
2.1A Understand switches
2.1B Understand switches
2.2 Understand routers
2.3A Understand media types
2.3B Understand media types
Understand swi tches 75
OBJECTIVE UNDERSTANDI NG NETWORK HARDWARE 2. 1A
A MAC address is
also called a physical
address and can be
viewed with ipcong/all.
Understand switches
SCENARIO: Michelle is logged into one of her social networking sites when she receives an urgent text message
from her friend Robert. Robert is trying to study for his IT networking class nal and has some questions
regarding the concepts and needs help. Michelle offers to meet Robert at Fourth Coffee.
While Michelle and Robert are studying at Fourth Coffee, Sidney, the IT Consultant at Fourth Coffee, stops by the
table to say hi to Michelle, who is a friend of hers. Michelle tells Sidney that she is helping Robert study for a test.
Sidney tells Robert that it is more fun to look at real equipment to learn the concepts and offers them a tour of
Fourth Coffees IT network.
While on the tour, Sidney starts to quiz Robert about the different networking components. Robert passes
Sidneys test. What about you?
1. A computers MAC address is:
a. assigned by a Network Administrator
b. located on the NIC
c. acquired from an ISP (Internet Service Provider)
2. The OSI model is to networking as:
a. music is to a Zune
b. cookies are to milk
c. fashion rules are to fashion
3. A smart Layer 2 device that has an IP address, connects the office computers
together, and provides full bandwidth to each port is called a:
a. managed hub
b. managed switch
c. unmanaged switch
76 CHAPTER 2: Understanding Net work Hardware
_______ /3
Answers
1. The MAC address for a computer is:
b. located on the NIC. The MAC address is determined by the vendor of the NIC.
2. The OSI model is to networking as:
c. fashion rules are to fashion. Just as stripes and solids do not usually match, networking devices
perform certain functions and follow specific rules based on their OSI model layer.
3. A device that provides full bandwidth to each port, connects computers together, has an IP address, and
operates at Layer 2 of the OSI model is a:
b. managed switch. Switches that are managed contain an IP address.
E ssential details
Know the layers of the ISOs (International Standards Organization) OSI model.
Hubs and repeaters are Layer 1 devices, switches and NICs are Layer 2, and routers are Layer 3.
Switches can create VLANs (Virtual Local Area Networks), which isolate network broadcast traffic.
Bandwidth is the throughput or the data transfer rate.
If you have a fast port but a slow cable, the network will operate at the slowest speed, which is the cables
speed.
FAST TRACK HELP
http://www.cisco.com/cisco/web/solutions/small_business/resource_center/
articles/connect_employees_and_offices/what_is_a_network_switch/index.html
http://www.cisco.com/en/US/docs/internetworking/technology/handbook/
Intro-to-Internet.html
http://www.cisco.com/en/US/prod/switches/
networking_solutions_products_genericcontent0900aecd806c7afe.pdf
FAST TRACK HELP
Understand swi tches 77
OBJECTIVE UNDERSTANDI NG NETWORK HARDWARE 2. 1B
It is important to
know the layers of
the OSI model and
how they operate.
Understand switches
SCENARIO: Joel is working in his college dorm room on a term paper when he loses Internet connectivity.
Because his laptop seems ne, Joel decides to enlist his friend Scott, who manages the dorms network, to help
him out.
Joel nds Scott and they go to the dorms network room to determine what has happened. While in the network
room, Joel learns more about how the dorms LAN is congured. Joel remembers that switches operate at
Layer 2 and shares that with Scott. However, Scott informs Joel that there are actually Layer 3 switches, too! Scott
also tells Joel that a new switch module is expected next week and hardware redundancy is being added.
After the issue is resolved, Joel returns to his dorm room to work on the term paper. However, he keeps thinking
about all he has learned and realizes that IT is both challenging and fun!
1. A Layer 3 switch performs:
a. Layer 2 forwarding and Layer 3 switching in hardware
b. Layer 2 segmenting and Layer 3 switching in hardware
c. Layer 2 switching and Layer 3 forwarding in hardware
2. A switch is to a network as:
a. a frame is to a picture
b. a portal is to the web
c. a case is to a computer
3. A motherboard is to a computer as:
a. a backplane is to a switch
b. a MAC address is to a switch
c. a certificate is to a switch
78 CHAPTER 2: Understanding Net work Hardware
_______ /3
Answers
1. The sophisticated Layer 3 switch performs:
c. Layer 2 switching and Layer 3 forwarding in hardware. This is a very smart device operating
at a higher layer!
2. A switch is to a network as:
b. a portal is to the web. A switch is a connection point for all local clients just like a portal is a collection
point for different web resources.
3. A motherboard is to a computer as:
a. a backplane is to a switch. Modules may be inserted into a switchs backplane for expansion and
upgrading purposes.
E ssential details
Switches are more than just a connection point for computers in a LAN.
Choose the right networking device for the specific goal.
Hardware redundancy provides highly available networks.
Managed switches provide more options for network support.
Use VLANs to segment systems from each other, which in turn enhances security.
FAST TRACK HELP
http://www.cisco.com/web/about/ac123/ac147/archived_issues/ipj_1-2/
switch_evolution.html
http://windows.microsoft.com/en-US/windows7/
How-do-hubs-switches-routers-and-access-points-differ
http://technet.microsoft.com/en-us/library/bb742373.aspx
FAST TRACK HELP
Understand routers 79
Routers are very
smart Layer 3 devices
that are used to connect
networks together.
OBJECTIVE UNDERSTANDI NG NETWORK HARDWARE 2. 2
Understand routers
SCENARIO: After setting up his familys wireless network, Scott decides that he needs to acquire more hands-on
experience using routers. Ty, his friend, recommends volunteering at the local Humane Society because he has
heard that they have a lot of IT issues.
Scott approaches the Director of the Humane Society, Justin, about volunteering. Justin immediately welcomes
Scott to his team! Justin would like Scott to install a network that will connect the ve desktop systems that they
currently have in the ofce to a server. Through the network the employees should have Internet access. Plus, he
would like to establish a connection to a different Humane Societys server in a neighboring town so that they
can share information. Justin anticipates expansion and would like to plan accordingly.
Scott is thrilled to receive this opportunity and knows he has a lot of studying to do!
1. The Humane Society cannot afford a router but they do have a switch and a Windows Server.
What should Scott do?
a. tell Justin that theyll have to wait until they can afford a router
b. use the switch because a Layer 2 device can perform the same functions as a router
c. use the switch to connect the desktops and servers and then install routing software
on the server
2. One week later a router is installed and Scott needs to figure out what routes
the router knows, so he:
a. accesses the routers NAT database and views the routes
b. accesses the routers routing table and views the routes
c. pings the router and it returns the routes
3. When Scott views the routes he sees that the router is learning new routes
because of:
a. dynamic routing
b. NAT
c. static routing
80 CHAPTER 2: Understanding Net work Hardware
_______ /3
Answers
1. Because the Humane Society has a switch and a Windows Server, Scott should:
c. use the switch to connect the desktops and servers and then install routing software on the
server. Through software, Windows Server can act just like a router and perform the same functions.
2. To determine what routes the router knows, Scott:
b. accesses the routers routing table and views the routes. The routing table contains static and
dynamic routes.
3. The router is learning new routes as a result of:
a. dynamic routing. The router continuously learns about new routes and routes that are no longer
available.
E ssential details
Routing tables are shared between neighboring routers.
The router always chooses the best path with the lowest cost from source to destination.
NAT allows a private address to be translated to a public address for Internet access.
Computers, routers, and other IP devices need a unique 32-bit IP address and a 32-bit IP subnet mask to
communicate in an IP network.
Computers also need a gateway address, which is the connected routers IP address.
FAST TRACK HELP
http://www.cisco.com/en/US/tech/tk648/tk361/
technologies_tech_note09186a0080094831.shtml
http://www.cisco.com/cisco/web/solutions/small_business/resource_center/
articles/connect_employees_and_offices/
what_is_a_network_switch/index.html
http://technet.microsoft.com/en-us/network/bb545655.aspx
FAST TRACK HELP
Understand media t ypes 81
It is important to
know the advantages
and disadvantages of
the different cable types!
OBJECTIVE UNDERSTANDI NG NETWORK HARDWARE 2. 3A
Understand media types
SCENARIO: Ever since The School of Fine Art has been actively participating in different social networking sites,
their enrollment has been exceeding their buildings capacity! Jon, the CIO, and Brian, the IT Manager, are
working through the different options available for wiring the new building they are planning to build in spring
and possibly updating the existing building.
Jon is concerned about the planned long distance between the two buildings, interference from different
electrical issues the School of Fine Art has been experiencing, and choosing the best media for the their goals.
Brian and Jon discuss the best cabling options available for their new building and start planning the long-term
goals for the School of Fine Art.
1. The best media choice for data to travel long distances without the risk of interference is:
a. fiber
b. thin coax
c. unshielded twisted-pair
2. Fiber:
a. can only be used for short distances
b. is extremely inexpensive
c. transmits data in the form of light
3. Any type of undesirable electromagnetic emission or electrical/electronic
disturbance is known as:
a. EIGRP
b. EMI
c. STP
82 CHAPTER 2: Understanding Net work Hardware
_______ /3
Answers
1. The best media choice for data to travel long distances without the risk of interference is:
a. fiber. Fiber is an excellent choice for long distances and it keeps data secure.
2. Fiber:
c. Transmits data in the form of light. Data traveling via fiber cable is transferred extremely fast for
long distances.
3. Interference in the form of electromagnetic emission or electrical/electronic disturbance is known as:
b. EMI. Interference can alter, modify, and drop data as it is transferred across media.
E ssential details
Fiber has a variety of different type of connectors that connect into switches, routers, and so on.
Fiber is available in single-mode and multimode.
Coax is commonly used for TV connections today rather than enterprise network installations.
UTP is commonly used today in star and extended star topologies because it is inexpensive and easy
to install.
Wireless provides many advantages over traditional cabling choices and therefore continues to increase
in popularity.
FAST TRACK HELP
http://www.ciscopress.com/articles/article.asp?p=31276&seqNum=4
http://www.youtube.com/watch#!v=PqmFne1gel4&feature=related
http://www.cisco.com/en/US/netsol/ns340/ns394/ns348/ns337/
networking_solutions_package.html
FAST TRACK HELP
Understand media t ypes 83
The speed and
intended distance
are critical factors
in selecting transmission
media.
OBJECTIVE UNDERSTANDI NG NETWORK HARDWARE 2. 3B
Understand media types
SCENARIO: The School of Fine Art created a project plan to design a network closet for their new building on
campus. Jon, the CIO, would like to recruit students from a local community college to assist with this project.
Mary Kay, one of the recruited students, becomes the project leader. The rst task assigned to the students will
be to choose the appropriate cable type to use for wiring the required classrooms and the backbone of the LAN.
The media goals for the cable running to the classrooms include ease of installation, keeping costs low, and being
wired. The media goals for the backbone include being fast and being redundant. The backbone cabling will be
more expensive and that is incorporated into the budget.
Mary Kay and her team of students are ready for the challenge! Are you ready to join the team?
1. Based on the media goals, the type of cable that should be run to the classrooms is:
a. coaxial
b. fiber
c. UTP
2. Based on the media goals, the type of cable that should be used for the backbone is:
a. fiber
b. STP
c. wireless
3. Jon asks Mary Kay what media she would recommend for the common areas.
She replies:
a. Wireless, because of ease of installation and flexibility.
b. Fiber, because of its low cost.
c. Wireless because it is secure by default without any configuration.
84 CHAPTER 2: Understanding Net work Hardware
_______ /3
Answers
1. Mary Kay and her team analyze the media goals for the classroom and choose:
c. UTP. UTP is the popular choice for a variety of wired installations because it is inexpensive and
easy to install.
2. Mary Kay and her team analyze the media goals for the backbone and choose:
a. fiber. Fiber is the popular choice for enterprise backbones and may be implemented in dual rings to
provide redundancy.
3. For the type of media to install in the common areas, Mary Kay quickly and easily answers:
a. Wireless, because of ease of installation and flexibility. Wireless is the preferred choice even
though it will have to be configured to make it more secure.
E ssential details
UTP cables in LANs contain RJ45 connectors.
Cat 5e and 6 are popular for new UTP installations.
Because of safety concerns, it is relatively easy to create UTP cables and a lot more difficult
to create fiber cables.
Cables need to be organized efficiently and properly labeled.
Know and follow the maximum distances for cable runs and even for wireless
deployments.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc750550.aspx
http://www.belden.com/03Products/03_CableBasics.cfm
http://www.ciscopress.com/articles/article.asp?p=169686
FAST TRACK HELP
3
Understanding
Protocols and Services
IN THI S CHAPTER
3.1A Understand the OSI model
3.1B Understand the OSI model
3.2 Understand IPv4
3.3A Understand IPv6
3.3B Understand IPv6
3.4 Understand names resolution
3.5 Understand networking services
3.6 Understand TCP/IP
86 CHAPTER 2: Understanding Net work Hardware
Understand the OSI model 87
OBJECTIVE UNDERSTANDI NG PROTOCOLS AND SERVI CES 3. 1A
Understand the OSI model
SCENARIO: Cassie and her friend Christian have just accepted new jobs at Lucerne Publishing. Cassie will be an IT
Networking Technician supporting Microsoft Windows Servers. Christian will be an IT Web Developer working on
Lucerne Publishings website.
On their rst day of work they attended Lucerne Publishings new employee orientation to learn all about the
companys policies. Various individuals provided lots of detailed information regarding policies and procedures
related to their various departments.
After the orientation Cassie turned to Christian and began talking with him about what they had just learned
during their orientation. Christian tells Cassie that the conversation reminds him of when they were in school and
she would quiz him on what they had just learned in class. Can you pass Cassies quiz on the OSI model?
1. The OSI model contains:
a. three layers
b. five layers
c. seven layers
2. Data is placed onto the physical network medium at the:
a. application layer
b. network layer
c. physical layer
3. OSI is to networking as:
a. a text message is to a mobile phone
b. a game rule is to football
c. a word is to a book
Remember the
OSI models layers
and their order via a
mnemonic phrase All
People Seem To Need
Daily Praise!
88 CHAPTER 3: Understanding Protocols and Servi ces
_______ /3
Answers
1. In the ISOs OSI model there are:
c. seven layers
2. The layer where data is placed onto the physical network medium is called the:
c. physical layer. The Physical layer (Layer 1) puts the data onto the wire at the source computer and then
it is sent to the destination computer.
3. OSI is to networking as:
b. a game rule is to football. It is important to follow the standards when networking just like it is
important to follow the game rules when playing football.
Essential details
Know the OSI models seven layers and the standards they represent.
Standards are followed so that computers and devices can speak the same language in order to
communicate with each other.
Each layer communicates with the other layers directly above and below.
Data is encapsulated or wrapped up at each layer within a different wrapper.
Protocols are a set of rules that provide guidelines for computer communication.
FAST TRACK HELP
http://support.microsoft.com/kb/103884
http://technet.microsoft.com/en-us/library/cc959881.aspx
http://www.cisco.com/en/US/docs/internetworking/technology/handbook/
Intro-to-Internet.html
FAST TRACK HELP
Understand the OSI model 89
OBJECTIVE UNDERSTANDI NG PROTOCOLS AND SERVI CES 3. 1B
Understand the OSI model
SCENARIO: Cassie is excited as she arrives for her second day on the job at Lucerne Publishing as an IT Network-
ing Technician. She will job shadow Holly for a couple of days to learn more about her job responsibilities.
Holly gives Cassie a tour of Lucerne Publishings datacenter, which contains all of the Microsoft Windows Servers
that Cassie will help support. As they are leaving the datacenter, Brian from the Accounting Department stops
Holly to tell her that he has been having a problem connecting to the network. Holly tells Brian that she and
Cassie will help solve the problem.
To solve Brians problem, Holly and Cassie use tools to gather information about his IP address and then work
through the layers of the TCP/IP model to determine why his computer is having networking problems. The prob-
lem will be solved quickly with knowledge of the OSI model!
1. The TCP/IP model contains:
a. four layers and is not used today
b. four layers and follows the standards of the OSI reference model
c. seven layers and was created before the OSI model
2. All hosts participating in a TCP/IP network, including Brians computer,
are assigned:
a. a MAC address
b. a port number
c. an IP address
3. A packet at Layer 3 becomes:
a. a frame at Layer 2
b. a packet at Layer 2
c. a network address
The ipcong
and ipcong/all
commands provide
information that is
useful for troubleshooting
networks.
90 CHAPTER 3: Understanding Protocols and Servi ces
_______ /3
Answers
1. The TCP/IP model contains:
b. four layers and follows the standards of the OSI reference model. The TCP/IP model is an actual
implementation of the OSI reference model even though it contains fewer layers.
2. All hosts participating in a TCP/IP network, including Brians computer, are assigned:
c. an IP address. All computers and devices in a TCP/IP network need an IP address, subnet mask, and
default gateway.
3. A Layer 3 packet becomes:
a. a frame at Layer 2. Data encapsulation at Layer 3 takes the form of a packet and at Layer 2 turns
into a frame.
Essential details
The TCP/IP model, or the TCP/IP protocol suit, contains four layers and protocols at each layer.
Different encapsulation types exist at the different layers, such as packets at the Network layer.
TCP operates at the Transport layer and IP operates at the Network layer.
All computers and devices participating in a TCP/IP network require an IP address,
subnet mask, and default gateway.
There are a few ports that should be remembered including: 53 (DNS),
80 (HTTP), 25 (SMTP), 110 (POP3).
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc786900(WS.10).aspx
http://windows.microsoft.com/en-US/windows-vista/Change-TCP-IP-settings
http://technet.microsoft.com/en-us/sysinternals/bb897557.aspx
FAST TRACK HELP
Understand I Pv4 91
OBJECTIVE UNDERSTANDI NG ACTI VE DI RECTORY 3. 3
IPv4 is still used
everywhere even
though IPv6 is also
available.
OBJECTIVE UNDERSTANDI NG PROTOCOLS AND SERVI CES 3. 2
Understand IPv4
SCENARIO: Today is the rst day of college classes for Paul and he is looking forward to learning more about
networking mobile devices.
Paul has several items on his to-do list before going to his rst class. First, he stops by the registration desk to
make a quick change to his schedule. The Registrar asks him for his student identication number so that she
can process the change. Next, he stops by the bookstore and the cashier asks him for his student identication
number so that she can process his book order. Luckily, he nds his classroom just in time for the class to begin.
After class, Paul tells his friend Scott that the professor talked about IP version 4 addresses. Scott decides to quiz
Paul because Scott has already taken the class and is sure he knows what Paul should have learned today!
1. An IP address is to a computer as:
a. a student identification number is to a student
b. chocolate is to a chocolate chip cookie
c. fur is to a polar bear
2. Characteristics of IPv4 include:
a. classes and 32-bit addresses
b. classes and 64-bit addresses
c. zones and 32-bit addresses
3. A default gateway is also known as:
a. an access point
b. a switch
c. a router
92 CHAPTER 3: Understanding Protocols and Servi ces
_______ /3
Answers
1. An IP address is to a computer as:
a. a student identification number is to a student. An IP address is unique to a computer just like each
student has a unique identification number that is different from all of the other students identification
numbers.
2. IPv4 characteristics include:
a. classes and 32-bit addresses. IPv4 contains Class A through E classes and all IP addresses
are 32-bit in length.
3. Another name for a default gateway is:
c. a router. The router provides a way for local subnet traffic to exit their subnet and travel to another
network as their final destination.
Essential details
IP addresses contain four octets and each octet contains eight bits.
Ranges of IP addresses are reserved for private networks.
A broadcast address is similar to an e-mail distribution list because information that is sent to a specific
broadcast address will be sent to all devices on that specific subnet.
Servers use static addresses; clients use dynamic IP addresses.
DHCP servers provide IP addresses to clients for a set lease time.
FAST TRACK HELP
http://support.microsoft.com/kb/164015
http://technet.microsoft.com/en-us/library/cc940018.aspx
http://technet.microsoft.com/en-us/network/bb530961.aspx
FAST TRACK HELP
Understand I Pv6 93
OBJECTIVE UNDERSTANDI NG ACTI VE DI RECTORY 3. 4
An IPv6 address
contains eight groups
of hexadecimal
characters separated by
colons. Example: 3ffe:
ffff:0000:2f3b:02aa:
00ff:fe28:9c5a!
OBJECTIVE UNDERSTANDI NG PROTOCOLS AND SERVI CES 3. 3A
Understand IPv6
SCENARIO: Today is nally the day that Randy is going to upgrade his current mobile phone!
When Randy arrives at The Phone Company, which sells almost every phone available, he is approached by
sales associate Laura. Laura is eager to help him choose a phone to meet his needs. Randy has some questions
regarding the two models he has preselected. Laura does an excellent job in explaining the differences between
the two phones. One economy model has a touch screen but does not offer scalability, or expansion, for future
needs because it only supports IPv4 addresses. Another model has the best of everything, including a large touch
screen and support for both IPv4 and IPv6.
Randy is torn between saving money and having a leading-edge phone. Laura tells him to consider his goals
regarding how he will use his phone and how long he intends to keep his phone. If you were Randy, which phone
would you choose?
1. IPv4 is to IPv6 as:
a. English is to Danish
b. Microsoft Windows XP is to Microsoft Windows 7
c. Microsoft Word 2010 is to Microsoft Word 2007
2. If Randy buys the IPv6 phone and uninstalls IPv4 support, he can still
communicate with an IPv4 device when he:
a. is connected to a IPv4 default gateway
b. is connected to a Dual Stack Architecture network
c. converts his IPv6 address to an IPv4 address manually
3. Randys new IPv6 phone would have a:
a. 32-bit IP address
b. 64-bit IP address
c. 128-bit IP address
94 CHAPTER 3: Understanding Protocols and Servi ces
_______ /3
Answers
1. IPv4 is to IPv6 as:
b. Microsoft Windows XP is to Microsoft Windows 7. Because businesses are moving to Windows 7,
it is becoming the new standard, similar to the way businesses are migrating to IPv6.
2. IPv4 devices and Randys IPv6 phone may still communicate with each other when Randy:
b. is connected to a Dual Stack Architecture network. A network environment that is running both
IPv4 and IPv6 simultaneously will provide communication between the two standards.
3. The new IPv6 phone that Randy may buy would have a:
c. 128-bit IP address. IPv4 addresses are 32 bits and IPv6 addresses are 128 bits.
Essential details
IPv4 addresses contain the numbers 0-255 and IPv6 addresses contain hexadecimal characters.
Hexadecimal characters include the numbers 0-9 and letters A-F.
IPv6 is becoming the new standard.
Windows provides support for both IPv4 and IPv6 through the Dual Stack Architecture.
Teredo, ISATAP, and 6to4 are tunneling technologies that provide transitional and
backward compatibility between IPv6 and IPv4 networks.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/bb726995.aspx
http://windows.microsoft.com/en-US/windows-vista/
IPv6-frequently-asked-questions
http://technet.microsoft.com/en-us/network/cc917486.aspx
FAST TRACK HELP
Understand I Pv6 95
OBJECTIVE UNDERSTANDI NG PROTOCOLS AND SERVI CES 3. 3B
Understand IPv6
SCENARIO: Classes are nished for the semester and winter break has begun. Next semester all classes will use
e-books, so Doug has decided to sell his current physical books to make a little extra money to buy great
holiday gifts for his family and friends. Doug chooses to sell his books through Lucerne Publishings new website.
He registers on the website, lists his books, and is ecstatic that one of the books sells immediately.
After receiving the shipping details and packaging the book, it occurs to him that the process of addressing and
packaging the book is similar to the way IP packets are structured and encapsulated. The book is encapsulated
into an envelope and the envelope contains both his return address and the address for its nal destinationjust
like an IP packet contains a source and destination address!
1. At the Networking Layer, in an IPv6 network, data is encapsulated into an IPv6:
a. envelope
b. header
c. packet
2. An IPv6 subnet mask is written in:
a. decimal
b. hexadecimal
c. octal
3. Subnet masks are to an IP address as a:
a. keyboard is to a computer
b. website is to a link
c. zip code is to a postal address
Ipcong displays
both IPv4 and IPv6
addresses.
96 CHAPTER 3: Understanding Protocols and Servi ces
_______ /3
Answers
1. In an IPv6 network, at the networking layer, data is encapsulated into an IPv6:
c. packet
2. A subnet mask for IPv6 is written in :
b. hexadecimal. IPv6 subnet masks are written in hexadecimal; IPv4 subnet masks are in decimal.
3. Subnet masks are to an IP address as a:
c. zip code is to a postal address. A zip code determines the city and state a package is to be
delivered to, which is similar to performing a bitwise AND operation of the subnet mask
and IP address to determine the subnet of the IP address.
Essential details
IPv4 and IPv6 packets both contain the source and destination IP addresses that are used by the router to
route the packet.
IPv6 addresses contain a dedicated subnetting portion.
Identify the subnet that an IP address belongs to in a network by performing a bitwise AND operation of the
subnet mask and IP address.
The loopback address for IPv4 is 127.0.0.1 and for IPv6 is 0:0:0:0:0:0:0:1 or ::1 (compressed
format).
FAST TRACK HELP
http://www.cisco.com/en/US/products/ps6553/
products_ios_technology_home.html
http://msdn.microsoft.com/en-us/library/aa915659.aspx
http://www.juniper.net/techpubs/en_US/junos9.6/
information-products/topic-collections/config-guide-routing/
id-10122335.html
FAST TRACK HELP
Understand names resol uti on 97
OBJECTIVE UNDERSTANDI NG PROTOCOLS AND SERVI CES 3. 4
Understand names resolution
SCENARIO: Laura Steele is packing for her big trip to Australia. Her IT Internship class is travelling to Australia
to study IT best practices in a different country. She is looking forward to the adventure and to expanding her
knowledge. She knows that her career could take her any place in the world!
At the airport, Laura and her classmates check in at the Blue Yonder Airlines ticket counter. The ticket agent asks
Laura her name and she tells the agent that her full name is Laura Steele Polly. Next, the ticket agent asks Laura
for her drivers license number and Laura provides it to the ticket agent. The names and license number indicate
that both refer to the same individual. Finally, after the ticket agent is fully satised that Laura Steele is really
Laura Steele Polly, Laura is given her boarding pass.
After receiving their boarding passes the students stand in the security line. While waiting for their turn, the
students talk about the ticket check-in procedures. Laura Steele shares with her classmates that the
check-in procedure reminds her of name resolution. Is it similar?
1. A domain name is to an IP address as:
a. a kangaroo is to Australia
b. Laura Steeles name is to her drivers license number
c. Laura Steeles student identification number is to her name
2. When Laura Steele browses the Web on her mobile phone and types
in http://www.microsoft.com and presses Enter:
a. the domain name Microsoft.com is resolved to an IP address
b. the IP address is a calculated address based on the domain name
c. WINS checks the local LMHOSTS file and determines the MAC address
of the domain name
3. The server that translates domain names to their corresponding
IP addresses is called a:
a. DHCP server
b. DNS server
c. WINS server
It is usually easier
to remember domain
names and more
difcult to remember
IP addresses.
98 CHAPTER 3: Understanding Protocols and Servi ces
_______ /3
Answers
1. A domain name is to an IP address as:
b. Laura Steeles name is to her drivers license number. Both resolve a name to a number
and identify the same location or person.
2. On her mobile phone, when Laura Steele types in http://www.microsoft.com and presses Enter:
a. the domain name microsoft.com is resolved to an IP address. The domain name microsoft.com will
be translated by a DNS server to its respective IP address.
3. Domain names are resolved to their corresponding IP addresses by the:
b. DNS server. DHCP servers provide dynamic IP addresses to clients, DNS servers resolve domain names
to IP addresses, and WINS servers map computer NetBIOS names to IP addresses.
Essential details
WINS servers resolve NetBIOS names to IP addresses and assist in reducing NetBIOS traffic on subnets.
DNS servers resolve domain names to IP addresses.
DNS servers are part of the Internets infrastructure.
DNS servers are also used in both enterprise and small business networks.
Different DNS record types exist on a DNS server.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc725802.aspx
http://technet.microsoft.com/en-us/network/bb629410.aspx
http://technet.microsoft.com/en-us/library/bb727005.aspx
FAST TRACK HELP
Understand net working ser vi ces 99
OBJECTIVE UNDERSTANDI NG PROTOCOLS AND SERVI CES 3. 5
Understand networking services
SCENARIO: Fourth Coffees business continues to grow. Josh, Fourth Coffees owner, has decided to expand to
California. Sidney, his IT consultant, will travel to Santa Clara, California and set up a remote wireless network that
will be connected to Fourth Coffee headquarters in Seattle, Washington. Sidney will congure the wireless router
to act as a DHCP server. There will be an onsite le server which will provide access to local resources, as well as
provide DNS services. In addition, Josh would like to be able to access the network remotely so that he can keep
up with business while on the road.
As Sidney leaves Fourth Coffee to catch her ight home, Josh stops her and asks how IPsec could be used in their
network infrastructure. Sidney laughs and asks Josh if he has been busy reading his latest computer magazine
online. He smiles and wishes her a safe trip.
1. The DHCP server will provide a:
a. dynamic IP addresses to the clients
b. static IP addresses to the clients
c. static IP addresses to the servers
2. A Remote Access Server is to a client as a:
a. lion is to Africa
b. locked car door is to a car
c. pixel is to a digital camera
3. Regarding Joshs question, IPsec is:
a. a protocol suite used for securing IP communications
b. used to assign static and dynamic IPv6 address to clients
c. used to provide security to IPv6 addresses
When a system
boots up it requests an
IP address from a DHCP
server through the DORA
(Discover, Offer, Request,
Acknowledge) process
100 CHAPTER 3: Understanding Protocols and Servi ces
_______ /3
Answers
1. Servers that offer DHCP services provide a:
a. dynamic IP address to the clients. Dynamic IP addresses are assigned to clients and can change when
a lease is renewed. Static IP addresses are assigned to a server so they retain the same address and can
be easily located.
2. A Remote Access Server is to a client as a:
b. locked car door is to a car. A Remote Access Server (RAS) is protected by a firewalls, and if a client
is authenticated the client will be able to access the RASs services just like a key will allow a driver to
access a car.
3. To answer Joshs question, IPsec is :
a. a protocol suite used for securing IP communications. IPsec consists of open standards and uses
cryptographic security services.
Essential details
Clients are generally assigned dynamic address.
Servers are assigned static address so that they may be easily located on a network.
DHCP servers assign dynamic addresses to clients.
Remote Access Servers, also known as Communication Servers, provide access
to remote network resources.
IPsec, created by IETF (Internet Engineering Task Force), secures IP communications
through secure authentication and encryption.
FAST TRACK HELP
http://technet.microsoft.com/en-us/network/bb643151.aspx
http://technet.microsoft.com/en-us/library/cc754634(WS.10).aspx
http://technet.microsoft.com/en-us/network/bb531150.aspx
FAST TRACK HELP
Understand TCP/I P 101
OBJECTIVE UNDERSTANDI NG PROTOCOLS AND SERVI CES 3. 6
Understand TCP/IP
SCENARIO: Sara just received an interesting e-mail from Andrew. Sara met Andrew a year ago in her rst
networking class at Maple College and ever since then they have been spending a lot of time together
studying. However, now things have changed and Andrew has just asked her out on a real date!
She immediately replies to the e-mail and says, Yes! Immediately after hitting send, Sara receives an
e-mail indicating that her reply e-mail to Andrew was not delivered. Sara reaches for her mobile phone and
begins texting Andrew when it dawns on her that she might possibly x this computer problemor at least
determine what might have gone wrong.
Will she be able to resolve the problem so that she can go on a date with Andrew? Can you help her?
1. Sara first decides to use the pathping tool because it:
a. acts as a terminal emulation program that will automatically troubleshoot the issue
b. determines the degree of packet loss along the path the data is traveling
c. shows the route that is taken by the packet as it moves across the IP network
2. Next Sara tries to see if she can reach the default gateway by using the
a. netstat tool
b. ping tool
c. loopback address
3. Based on the results, Sara decides that she needs to refresh her
DHCP settings by using the:
a. telnet tool
b. ipconfig tool
c. local loopback IP
Using the
analytical tools in the
most efcient order
will save time.
102 CHAPTER 3: Understanding Protocols and Servi ces
_______ /3
Answers
1. The pathping tool that Sara used:
b. determines the degree of packet loss along the path the data is traveling. This is a useful tool;
however, Sara could have saved time by first checking her computers connectivity to the default
gateway.
2. To see whether her computer can reach the default gateway she used the:
b. ping tool. Depending upon the issue, the ping tool is usually one of the first tools used during
troubleshooting.
3. To refresh her DHCP settings, Sara used the:
b. ipconfig tool. The ipconfig/release will release Saras current IP address and the ipconfig/renew will
give her computer a new IP address.
Essential details
To check connectivity, first ping your loopback address (127.0.0.1), then ping your computers IP address, then
ping your default gateway, and finally ping the remote host.
Ping contains different options for IPv4 and IPv6.
Ipconfig/all displays lots of useful information, including DNS servers.
Tracert traces the route a packet takes from the source to destination.
Telnet logs into a router or computer.
FAST TRACK HELP
http://support.microsoft.com/kb/814155
http://windows.microsoft.com/en-US/windows7/
Using-command-line-tools-for-networking-information
http://www.cisco.com/en/US/tech/tk828/
technologies_tech_note09186a00800a61c7.shtml
FAST TRACK HELP
MTA 98-367
SECURITY
FUNDAMENTALS
1
Understanding
Security Layers
IN THI S CHAPTER
1.1 Understand core security principles
1.2 Understand physical security
1.3 Understand Internet security
1.4 Understand wireless security
107
Understand core security principles
SCENARIO: Blue Yonder Airlines has expanded over the past 18 months and has recently gone through a security
audit to ensure that the technical system is secure. Several areas needing improvement were identied. The CIO
has asked Toni Poe, Blue Yonder Airlines security consultant, to provide some essential security training for the
front-line staff. The goal is to minimize the risk for potential security threats by educating staff members in the
area of social engineering, as well as some basic security principles.
Toni has assessed the security rights of each staff member related to computer access and perimeter access.
Toni notes that some staff members have elevated privileges to access Blue Yonder Airlines intranet site. He also
knows that it is important to stress the Condentiality, Integrity, and Availability triangle in his training.
1. Toni plans to implement the principle of least privilege. How will this affect the staff members?
a. staff members will maintain their current access to all resources
b. staff members will be granted the smallest set of privileges to the resources
c. staff members will have to log on as administrator to have access to their resources
2. What would be an example of providing availability as it relates to security training?
a. making sure all the workstations are turned on
b. ensuring that all staff members have perfect attendance for work
c. protecting against a Distributed Denial of Services attack
3. What is an example of social engineering?
a. calling a staff member while pretending to be someone else to gain information
that can provide access to sensitive information
b. developing social awareness of security threats within an organization
c. building a social networking website
OBJECTIVE UNDERSTANDI NG SECURI TY LAYERS 1. 1
Social engineering
is not related to social
networking. The ultimate
goal of a hacker is to
obtain as much information
by exploiting the human
side of security.
Understand core securi t y principl es 107
108 CHAPTER 1: Understanding Securi t y Layers
Answers
1. Implementing the principle of least privilege means that:
b. staff members will be granted the smallest set of privileges to the resources
2. Providing availability as it relates to security training means:
c. protecting against a Distributed Denial of Services attack
3. An example of social engineering could include:
a. calling a staff member while pretending to be someone else to gain information that can
provide access to sensitive information
Essential details
The CIA (confidentiality, Integrity and Availability) Triangle is the concept of ensuring the prevention
of unauthorized disclosure of information, the erroneous modification of information, and the prevention of
unauthorized withholding of information or resources.
The principle of least privilege requires that each subject in a system be granted the most restrictive set of
privileges (or lowest clearance) needed for the performance of authorized tasks.
Social engineering is any type of behavior that can inadvertently or deliberately aid an attacker in gaining
access to a users password or other sensitive information.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc875841.aspx
FAST TRACK HELP
_______ /3
Understand physi cal securi t y 109
OBJECTIVE UNDERSTANDI NG SECURI TY LAYERS 1. 2
Understand physical security
SCENARIO: Erin Hagens has just been promoted to security ofcer for Woodgrove Bank. This position carries
huge responsibility for the safety of the customers money and information, not to mention the banks
reputation. This role necessitates that she keep current on a long list of requirements for securing Woodgrove
Bank. A banking industry regulatory agency has informed Erin that the bank will undergo a security audit to
ensure that they are in compliance with industry regulations and standards. Erin understands the request and
must do her due diligence to provide whatever information the regulators need as they target potential security
holes. Her biggest concern is the physical security of the banks systems.
1. What can Erin do to ensure physical security of the bank desktop computers?
a. disable the use of floppy drives or USB drives by using group policies
b. have a guard posted in every cubical area
c. obtain locking mechanisms for each desktop so they cannot be carried away
2. Erin has a concern that people can authenticate to the servers in the data center. What can she do
to prevent normal users from logging onto those systems?
a. make sure the server is locked up
b. remove the keyboards from all servers
c. create a group policy that applies to the servers to Deny Log on Locally
for all non-administrative users
3. What can Erin do to prevent the use of key loggers in the bank?
a. ensure that the terminals are locked and do a periodic inspection of the ports
on the systems
b. nothingErin cannot control what gets plugged into her computers
c. convert all computers to touch screen monitors
It may not be
nancially feasible or
physically possible for
the bank to convert
all systems to touch
screens.
110 CHAPTER 1: Understanding Securi t y Layers
Answers
1. To ensure physical security of desktop computers, Erin can:
a. disable the use of floppy drives or USB drives by using group policies. Most computers do have a
mechanism to attach a locking device to the desktops, however, disabling USB and floppy drives
disables a larger threat.
2. To prevent normal users from logging onto the systems, Erin can:
c. create a group policy that applies to the servers to Deny Log on Locally for all
non-administrative users. A bigger issue is people are in the data center with physical
access. However, normal users should not have the ability to log on locally.
3. To prevent the use of key loggers in the bank, Erin will have to:
a. ensure that the terminals are locked and do a periodic inspection of the ports on the systems
Essential details
Keystroke logging (often called key logging) is the process of recording the keys typed on a keyboard,
typically without the users knowledge.
Access controls are the mechanisms for limiting access to certain items of information or to certain controls
based on users identities and their membership in various predefined security groups..
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/bb457125.aspx
http://www.microsoft.com/smallbusiness/security.aspx
FAST TRACK HELP
_______ /3
Understand Internet securi t y 111
OBJECTIVE UNDERSTANDI NG SECURI TY LAYERS 1. 3
Understand Internet security
SCENARIO: Terry Adams is the desktop administrator for Tailspin Toys. To stay current with the latest Internet
technologies, Tailspin Toys has decided to upgrade their browsers to Internet Explorer (IE) 8. Terry wants to
make sure that they utilize many of the security features built into the browser while still maintaining functionality
within the companys intranet. Terry also would like to educate his users to be good Internet citizens and
practice safe web surng. He knows that the rst line of defense in Internet security is an informed and
skilled user.
1. Terry wants to configure the Internet zone feature in IE 8 in such a way that users can easily access
content on the local intranet while still maintaining a high level of security. What should he do?
a. create a perimeter network and make sure the intranet site is located there and have a single PC in each
department designated the Intranet Browsing PC (IBPC)
b. go into the Internet Options, choose Security and add their intranet site to the list of Local Intranet Sites
c. print the content of the intranet site weekly and distribute it through interoffice mail
2. What can Terry tell his staff to look for to be assured that they are on a secured website?
a. a padlock in the lower right corner of the browser and https:// in the address bar
b. the contact information on the site
c. they should not be browsing secure sites because you cant trust any site
3. What is the security level set to in the Restricted Sites zone?
a. low; the sites are restricted and therefore not a concern
b. high; disables most features, has the maximum safeguards, and protects
against harmful content
c. medium; a nice balance between too restrictive and too open
The default level in
the restricted sites
zone is set to High.
112 CHAPTER 1: Understanding Securi t y Layers
Answers
1. To configure the Internet zone feature in IE 8 and enable users to easily browse the local intranet, Terry
should:
b. go into the Internet Options, choose Security and add their intranet site to the list of Local
Intranet Sites
2. To be sure that they are on a secure site, staff members can look for a:
a. a padlock in the lower right corner of the browser and https:// in the address bar. This does not
guarantee that the site is secure. However, it is a start.
3. The security level in the Restricted Sites zone is:
b. high; disables most features, has the maximum safeguards, and protects against harmful
content
Essential details
An Internet zone contains websites that are not on your computer or on your local intranet, or that are not
already assigned to another zone. The default security level is Medium.
A secure site is a website with the capability of providing secure transactions, ensuring that credit
card numbers and other personal information will not be accessible to unauthorized parties..
FAST TRACK HELP
http://support.microsoft.com/kb/174360
FAST TRACK HELP
_______ /3
Understand wirel ess securi t y 113
OBJECTIVE UNDERSTANDI NG SECURI TY LAYERS 1. 4
Understand wireless security
SCENARIO: Pilar Ackerman is the systems administrator for Fourth Coffeea national chain of very popular and
protable coffee cafs. Competition in the coffee caf business is erce! To maintain a competitive edge, Fourth
Coffee plans to add open, high-speed, wireless access for their customers and secured wireless for employees at
all 200 Fourth Coffee locations. Pilar is faced with several security concerns and must ensure that their business
trafc is secured. In addition to that, he is under pressure to make this new feature a winning strategy.
1. What is the most secure protocol that Pilar can implement to ensure that the business-related
traffic is encrypted?
a. Wired Equivalent Privacy (WEP)
b. WiFi Protected Access (WPA) 2
c. Extensible Authentication Protocol (EAP)
2. Aside from encrypting the business wireless traffic, what else can Pilar do to add another
level of security?
a. implement access point isolation and hide the Service Set Identifier (SSID)
b. turn off the business access points when customers come in
c. enable MAC filtering
3. Pilar would like his employees to be independent in troubleshooting their own
wireless connections before contacting him. What basic troubleshooting step
that he can instruct them to do?
a. reboot their computers
b. power cycle the wireless access points
c. right-click the network icon in the system tray and select Troubleshoot Problems
Power cycling the
access point would
disconnect other users
from the network.
114 CHAPTER 1: Understanding Securi t y Layers
Answers
1. The most secure protocol that Pilar can implement to ensure that the business-related traffic is encrypted is:
b. WiFi Protected Access (WPA) 2. EAP is a feature of security that handles authentication
and WPA is more secure than WEP.
2. Pilar can add another level of security by:
a. implementing access point isolation and hiding the Service Set Identifier (SSID). MAC filtering
is an option; however, MAC addresses can be faked or spoofed. Hiding the SSID is a simple security
measure that can be implemented.
3. Pilar can instruct the staff to troubleshoot by:
c. right-click the network icon in the system tray and selecting Troubleshoot Problems
Essential details
A Service set identifier (SSID) is a 32-character, unique identifier attached to the header of packets sent
over a WLAN that acts as a password when a mobile device tries to connect to the communicating stations
on a wireless LAN.
Wi-Fi protected access (WPA) is a Wi-Fi standard that was designed to improve upon the security features
of WEP.
Wired equivalent privacy (WEP) is an encryption algorithm system included as part
of the 802.11 standard, developed by the Institute of Electrical and Electronics Engineers
as a security measure to protect wireless LANs from casual eavesdropping.
FAST TRACK HELP
http://technet.microsoft.com/en-us/magazine/2005.11.securitywatch.aspx
http://windows.microsoft.com/en-US/windows-vista/
What-are-the-different-wireless-network-security-methods
http://www.windowsnetworking.com/articles_tutorials/
Securing-Wireless-Network-Traffic-Part1.html
FAST TRACK HELP
neerss
_______ /3
2
Understanding
Operating System
Security
IN THI S CHAPTER
2.1A Understand user authentication
2.1B Understand user authentication
2.2 Understand permissions
2.3 Understand password policies
2.4 Understand audit policies
2.5A Understand encryption
2.5B Understand encryption
2.6 Understand malware
BETA COURSEWARE EXPIRES NOVEMBER 26, 2010
Understand user authentication
SCENARIO: Jim Hance is a security administrator for Coho Winery. A variety of security threats have occurred
over the past few months and management is more than a little concerned. They cannot afford to have the
system jeopardized; their customers expect a reliable and secure site. Jim is reviewing the security policies
for Coho Winery to determine where the company may need stronger policies or at least to update the
existing policies and security measures. His rst task is determining the companys strengths as it relates
to user authentication.
1. Jim knows that stronger passwords are a critical element in the security plan. What characteristics
make up a strong password?
a. contains 7+ characters; does not contain the user name, real name, or company name
b. contains sequential numbers embedded within the company name
c. contains the users last name and email address
2. What protocol can be used to secure workstation and computer authentication across the network?
a. TCP/IP
b. Kerberos
c. Lightweight Directory Access Protocol
3. What strategy can Jim implement to reduce the number of times a user would
have to authenticate to access a particular resource?
a. two-factor authentication
b. digital certificates
c. Single Sign-on (SSO)
Understand user authenti cati on 117
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM SECURI TY 2. 1A
Reducing the
number of times a
user has to authenticate
can reduce the
possibilities of his or her
credentials being
captured.
118 CHAPTER 2: Understandi ng Operati ng System Securi t y
Answers
1. A strong password:
a. contains 7+ characters; does not contain the user name, real name, or company name
2. To secure workstation and computer authentication across the network, Jim can use:
b. Kerberos
3. To reduce the number of times a user would have to authenticate to access a particular resource, Jim can
implement:
c. Single Sign-on (SSO)
Essential details
Authentication is the process of obtaining identification credentials such as name and password from a user
and validating those credentials against some authority.
Kerberos authenticates the identity of users attempting to log on to a network and encrypts their
communications through secret-key cryptography.
Lightweight directory access protocol (LDAP) is a network protocol designed to work on TCP/IP stacks to
extract information from a hierarchical directory such as X.500.
Remote authentication dial-in user service (RADIUS) is an Internet protocol in which
an authentication server provides authorization and authentication information
to a network server to which a user is attempting to link.
FAST TRACK HELP
http://www.microsoft.com/windowsserver2008/en/us/ad-main.asp
http://web.mit.edu/Kerberos/#what_is
http://technet.microsoft.com/en-us/library/bb463152.aspx
FAST TRACK HELP
_______ /3
Understand user authenti cati on 119
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM SECURI TY 2. 1B
Understand user authentication
SCENARIO: The Graphic Design Institute (GDI) has more than 30,000 students. The security of the students personal
information, including nancial data, address, family contacts, special health needs, and grades, is the top priority of
the network administrative team. However, over the past few months student data has been compromised on several
occasions. Personal data has shown up on a social networking site, much to the embarrassment of the network team.
GDI ofcers have asked the network administrator, Todd Rowe, to implement stronger authentication measures for
the students, as well as eliminate IT staff from logging on with elevated privileges. Todd has several options, but is
aware of the need to keep the processes fairly easy for the helpdesk staff.
1. Todd wants to implement two-factor authentications. What can he use?
a. smart card and user password
b. two passwords
c. two user IDs with two passwords
2. What service can the GDI staff use instead of signing in with elevate privileges?
a. Remote Desktop
b. Secondary Logon-Run As
c. User Manager for Domains
3. What is a disadvantage of using biometric identification?
a. the user must have hands
b. cost is prohibitive for many organizations
c. a retina scan can be faked
Biometric
identication is
extremely secure;
however, the devices to
support biometrics are
cost-prohibitive.
120 CHAPTER 2: Understandi ng Operati ng System Securi t y
Answers
1. To implement two-factor authentications, Todd can use:
a. smart card and user password
2. Instead of signing in with elevated privileges, the staff can use:
b. Secondary Logon-Run As
3. A disadvantage of biometric identification is:
b. cost is prohibitive for many organizations
Essential details
A certificate is an electronic credential that authenticates a user on the Internet and intranets.
Public key infrastructure (PKI) is an asymmetric scheme that uses a pair of keys for encryption: the public
key encrypts data, and a corresponding secret key decrypts it.
The Run As command allows a user to run specific tools and programs with different permissions than the
users current logon provides.
Steps to change your password:
Press <control><alt><delete> and select Change Password
Steps to use Secondary Logon or Run As. . .
Right-click the application icon and select Run As Administrator
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc782756(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc756862(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc261673(office.12).aspx
FAST TRACK HELP
_______ /3
Understand permissi ons 121
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM SECURI TY 2. 2
Understand permissions
SCENARIO: Fabrikam, Inc. has recently under gone a basic reorganization and a variety of corporate changes. Shawn
Richardson is the network administrator at Fabrikam and has been assigned the task of aligning the company servers
with the new organizational reality. As a rst step, Shawn has completed a security audit of the companys Microsoft
Windows Server
2008 R2 le servers and has determined that folder and share security needs to be revised based on
corporate reorganization. Shawn must present his plan to management and give directions to his team members to
complete the project.
1. Shawn has noticed that some shares on the file system are not secured. What is the default
permission setting when a share is created?
a. everyone with Read permission
b. administrators with the Full Control permission
c. everybody with the Full Control permission
2. Why should Shawn enforce User Account Control (UAC) across the domain?
a. so that he can control the user accounts
b. to help prevent unauthorized changes to computers on the domain
c. to allow the users to authenticate with the administrator password to perform
an administrative task
3. What feature (also available with Active Directory objects) will make Shawns job
easier when reassigning permissions by not having to assign permissions
to every parent and child folder?
a. batch files
b. inheritance
c. staff people
Inheritance allows
the propagation for
rights or permissions
from a parent object
to a child object. This
feature can be blocked
or removed.
122 CHAPTER 2: Understandi ng Operati ng System Securi t y
Answers
1. When a share is created, the default permission is:
a. everyone with Read permission
2. Shawn should enforce User Account Control (UAC) across the domain because:
b. it will help prevent unauthorized changes to computers on the domain
3. Shawns job can be made easier when reassigning permissions by using:
b. inheritance
Essential details
Permissions include Full control, Modify, Read & Execute, List folder Contents, Read, and Write and can be
applied to both folder and file objects. Permissions can also be applied to Active Directory objects.
Inheritance is the concept of permissions that are propagated to an object from a parent object.
Inheritance is found in both file system permissions and Active Directory permissions. It does
not apply to share permissions.
New Technology File System (NTFS), FAT, and FAT32. The primary difference between NTFS and FAT file
systems is the ability apply security to the file system. You can grant or deny various permissions
on NTFS. NTFS also supports the ability to encrypt data.
Share and NTFS permissions are applied based on how the resource is accessed.
Share permissions are effective when the resource is being accessed through the
network whereas NTFS permissions are effective all the time. When share and
NTFS permissions are applying to the same resource, the most restrictive
permission wins.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc730772.aspx
http://technet.microsoft.com/en-us/library/cc771375.aspx
http://technet.microsoft.com/en-us/library/cc770906(WS.10).aspx
FAST TRACK HELP
_______ /3
Understand password poli ci es 123
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM SECURI TY 2. 3
Understand password policies
SCENARIO: Jay Hamlin has been given the unenviable task of enforcing stronger password policies for
Wingtip Toys. He understands the need for complex passwords of a minimum length, but is having a difcult
time making the staff understand how the security of the entire Wingtip Toys organization can depend upon
these couple requirements along with a few more that he plans to put into place. He must also determine how
many times a user can attempt to log in before his or her account is locked out, how often users must change
passwords, and how often users can reuse a favorite password.
His plan for a Password Complexity Policy includes the following criteria for passwords:
Cannot contain the users login name
Must be at least 6 characters or greater
Must contain three of the following four characters: upper case, lower case, number, and special character
1. What dilemma is Jay facing if he makes his password requirements too difficult?
a. a complex password can be hard to guess and difficult to remember
b. Jay will no longer have friends at work
c. users will not use the passwords
2. What does the policy of maximum password age mean?
a. determines how old the user must be to create a password
b. refers to the duration before a password has to be changed
c. refers to how old the password must be before the user is allowed to change it
3. What happens when you set the value of Enforce Password History to 10?
a. the user has 10 attempts to validate his or her password
b. the password must be used for at least 10 days before it can be changed
c. the system remembers the last 10 passwords and will not allow the user to reuse
any of the previous 10
Password history
prevents users from
reusing their passwords.
124 CHAPTER 2: Understandi ng Operati ng System Securi t y
Answers
1. The dilemma Jay faces with difficult password requirements is that:
a. a complex password can be hard to guess and difficult to remember
2. Maximum password age:
b. refers to the duration before a password has to be changed
3. When you set the value of Enforce Password History to 10:
c. the system remembers the last 10 passwords and will not allow the user to reuse any
of the previous 10
E ssential details
Account lockout is a security feature in Windows that locks a user account if a number of failed logon
attempts occur within a specified amount of time, based on security policy lockout settings.
A password attack is an attack on a computer or network in which a password is stolen and decrypted or is
revealed by a password dictionary program.
Password sniffing is a technique employed by hackers to capture passwords by intercepting data packets
and searching them for passwords.
Microsoft Windows Server 2008 allows for fine-grained password policies, which allows
for more flexible password policy assignment throughout an organization within
Active Directory
.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc784090(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc875814.asp
FAST TRACK HELP
_______ /3
Understand audi t poli ci es 125
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM SECURI TY 2. 4
Understand audit policies
SCENARIO: The network for Margies Travel must be very secure. The les contain customer information including
credit card numbers, birthdates, and addresses, as well as photocopies of passports. Identity theft would be a real
possibility if the system was hacked into. Obviously, this is not an acceptable risk for Margies Travel.
Arlene Huff is the systems administrator for Margies Travel. The company has asked her to track who attempts to
log into the system and at what times of the day the attempts occur. They also have asked her to create a system
to track when condential les are opened and by whom. Arlene gladly took on this task and did not raise a huff.
1. Arlene wants to log when someone fails to log into the system as administrator, but why would she
want to log when they are successful also?
a. to determine if and when someone is authenticating successfully with elevated privileges
b. to make sure they are getting in without any problems
c. to monitor drive space on the computer
2. Where are file audit events written when auditing is enabled?
a. audit event log
b. pfirewall.log
c. security event log
3. Why is it important to properly secure audit logs?
a. so that potential hackers cannot delete the event logs to cover their tracks
b. its not important, no one looks at audit logs
c. so only authorized personnel can view the log files
Skilled computer
hackers will modify
the audit logs when
they are nished obtaining
information so that it
will appear as though they
were never there.
126 CHAPTER 2: Understandi ng Operati ng System Securi t y
Answers
1. Arlene wants to log when someone successfully logs into the system as well as when they fail:
a. to determine if and when someone is authenticating successfully with elevated privileges.
If someone failed four times and was then successful the fifth time it could indicate hacker activity.
2. Enabled file auditing events are written in the:
c. security event log
3. It important to properly secure audit logs
a. so that potential hackers cannot delete the event logs to cover their tracks
Essential details
Auditing is the process an operating system uses to detect and record security-related events, such as an
attempt to create, access, or delete objects such as files and directories.
An audit policy is a policy that determines the security events to be reported to the network administrator.
The security log, which can be generated by a firewall or other security device, lists events that could affect
security, such as access attempts or commands, and the names of the users involved.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/dd408940(WS.10).aspx
http://technet.microsoft.com/en-us/library/dd349800(WS.10).aspx
FAST TRACK HELP
_______ /3
Understand encr ypti on 127
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM SECURI TY 2. 5A
Understand encryption
SCENARIO: Adventure Works has recently expanded its mobile sales force. The management team has recently
come to recognize the unique security considerations associated with hundreds of laptop computers
simultaneously located in hundreds of unsecure locations.
David Johnson is the network administrator in charge of the Adventure Works mobile sales force. He has recently
come under re from the management team regarding the sensitive data that could potentially fall into the
competitions hands if any of the laptop computers were to be stolen or misplaced. They must have a solution
that can ensure the condentiality of data on the mobile stations that are all running Windows
7 Enterprise
and they need it soon!
1. What can David enable to make sure their data is safe?
a. Encrypting File System (EFS)
b. password protected screen saver
c. BitLocker
2. What must be configured to ensure that the Bitlocker
storage can be reclaimed?
a. the salespersons personal identification and login credentials
b. BitLocker to use data recovery agents
c. the Secret Retrieval Agent
3. What are some considerations David will have to ponder when deciding
to use BitLocker?
a. the conscientiousness and self-discipline of the sales staff
b. the deployment of hardware because BitLocker requires a system reserved partition
c. its so easy that there arent any serious considerations
Bitlocker requires
a system-reserved
partition created during
a standard installation.
128 CHAPTER 2: Understandi ng Operati ng System Securi t y
Answers
1. To make sure the data is safe, David must enable:
c. BitLocker
2. To ensure that the secured data can be reclaimed in the event that Bitlocker protected storage is moved to
another computer, the administrator must create and properly store:
b. BitLocker to use data recovery agents
3. When using BitLocker, the administrator must consider:
b. the deployment of hardware because BitLocker requires a system reserved partition
Essential details
BitLocker (ToGo) drive encryption is a data-protection feature available in Windows Server 2008 R2 and
in some editions of Windows 7.
Encrypting file system (EFS) is a feature of Windows that allows you to store information on your hard disk
in an encrypted format.
Encryption is the process of encoding data to prevent unauthorized access, especially during transmission.
FAST TRACK HELP
http://technet.microsoft.com/en-us/windows/dd408739.aspx
http://technet.microsoft.com/en-us/library/cc732774.aspx
http://technet.microsoft.com/en-us/library/ee706523(WS.10).aspx
http://technet.microsoft.com/en-us/library/ee706518(WS.10).aspx
FAST TRACK HELP
_______ /3
Understand encr ypti on 129
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM SECURI TY 2. 5B
Understand encryption
SCENARIO: The owner of Southridge Video takes great pride in the close relationship that she has with the
managers in the various branch ofces up and down the coast. Weekly communication is the key to maintaining
the relationships and keeping on top of business progress and challenges.
The owner and managers would like to replace their Monday morning conference call with a secure Monday
morning video conference between corporate headquarters and the various branch ofces. They have asked the
WAN administrator, Jeff Wang, to create a cost-effective solution. The solution must work between the remote
branch ofces, so having a dedicated connection between ofces is too expensive. The best solution is to utilize
each ofces Internet connection.
1. What will create a secured connection over an unsecured network?
a. Virtual Private Network (VPN)
b. configuring the callback feature on their Routing and Remote Access Server
c. using a social networking site to have the conference meetings
2. Jeff needs to decide between Point to Point Tunneling Protocol (PPTP) or Layer 2 Tunneling
Protocol (L2TP). Which protocol is more secure?
a. PPTP
b. L2TP
c. neither, they both pass information in clear text
3. What is a public certificate?
a. an award given in recognition of superior business security policies
b. part of a two-part encryption that is not shared with other parties
c. a digitally signed statement that is commonly used for authentication and to secure
information on open networks
secure
A private key
certicate is a portion
of two-part encryption
that resides with the
originating computer
and is not shared.
130 CHAPTER 2: Understandi ng Operati ng System Securi t y
Answers
1. A secured connection over an unsecured network can be created with a:
a. Virtual Private Network (VPN)
2. The more secure protocol is:
b. L2TP. PPTP uses MPPE for security, which is less secure than L2TP, which uses IPsec as its encryption
method.
3. A public certificate is:
c. a digitally signed statement that is commonly used for authentication and to secure
information on open networks
Essential details
Layer 2 tunneling protocol with Internet protocol security (L2TP/IPSec) is a combination of PPTP and
Layer 2 Forwarding (L2F) that uses IPsec for encryption.
The user keeps the private key secret and uses it to encrypt digital signatures and to decrypt received
messages.
The user releases the public key to the public, who can use it for encrypting messages to be sent to the user
and for decrypting the users digital signature.
A virtual private network (VPN) is a secured tunnel running over a public network
such as the Internet that uses encryption technology so that data is safe from being
intercepted and understood by unauthorized users.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc700805.aspx
FAST TRACK HELP
ng
_______ /3
Understand mal ware 131
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM SECURI TY 2. 6
Understand malware
SCENARIO: Consolidated Messenger handles customer feedback for many area businesses. Each day they receive
thousands of email messages from happy and unhappy customers, which they funnel to the appropriate
individuals at their client companies.
Mary Kay Anderson is the systems administrator for Consolidated Messenger. The company has had several
outbreaks of viruses on the network that seem to have been propagated through email. They have asked Mary
Kay to host a lunch and learn session to educate Consolidated Messenger staff about malicious software and
email. Mary Kay has also been assigned the task to nd a solution that will better protect the system.
1. What should the staff members do when they receive a suspicious email from a customer or
coworker that contains an embedded hyperlink?
a. delete the email and then contact Mary Kay and the customer or coworker
b. quickly click the hyperlink to see what might happen to assess the threat themselves
c. forward the email to other coworkers warning them that the email is not legitimate
2. What can Mary Kay do to prevent suspicious emails from entering their network?
a. install Microsoft
Forefront
and Threat Management Gateway and configure it to
block malicious emails
b. disable internet email
c. threaten coworkers that they will be dismissed if they forward any email
3. What tool can Mary Kay download to remove malicious software (malware)?
a. Remote Server Administration Tools (RSAT)
b. Microsoft Windows Malicious Software Removal Tool
c. any web-advertised security software toolsthey are all the same
A malicious
software removal
tool is included in
Windows updates.
132 CHAPTER 2: Understandi ng Operati ng System Securi t y
Answers
1. When staff members receive a suspicious email that contains an embedded hyperlink they should:
a. delete the email and then contact Mary Kay and the customer or coworker. Never forward an
email with suspicious content. If an email has an attachment or link in it, contact the sender and verify
that he or she sent the message.
2. To prevent suspicious emails from entering the network, Mary Kay can:
a. install Microsoft Forefront and Threat Management Gateway and configure it to block any
malicious emails. Exchange server has several spam filtering tools. Forefront and TMG are additional
security measures to better protect the system.
3. To remove malicious software (malware), Mary Kay can download:
b. Microsoft Windows Malicious Software Removal Tool
Essential details
A bot is a program that performs some task on a network, especially a task that is repetitive or
time-consuming.
A rootkit is collection of software programs that a hacker can use to gain unauthorized remote access to a
computer and launch additional attacks.
Spyware is software sometimes referred to as spybot or tracking software. Spyware
uses other forms of deceptive software and programs that conduct certain activities
on a computer without obtaining appropriate consent from the user.
A trojan is a program that appears to be useful or harmless but contains hidden code
designed to exploit or damage the system on which it is run.
A worm uses self-propagating malicious code that can automatically distribute
itself from one computer to another through network connections.
FAST TRACK HELP
http://www.microsoft.com/downloads/details.aspx?FamilyId=F24A8CE3-
63A4-45A1-97B6-3FEF52F63ABB&displaylang=en
http://support.microsoft.com/kb/889741
FAST TRACK HELP
ies
code
_______ /3
3
Understanding
Network Security
IN THI S CHAPTER
3.1 Understand dedicated rewalls
3.2 Understand Network Access Protection (NAP)
3.3A Understand Network Isolation
3.3B Understand Network Isolation
3.4 Understand protocol security
134 CHAPTER 2: Understandi ng Operati ng System Securi t y
BETA COURSEWARE EXPIRES NOVEMBER 26, 2010
Understand dedi cated f irewalls 135
OBJECTIVE UNDERSTANDI NG NETWORK SECURI TY 3. 1
Understand dedicated rewalls
SCENARIO: Matt Berg has earned several Microsoft certications and is now his own boss as an independent
security consultant. Trey Research has retained his services to perform a security assessment of their network.
Trey Research has several servers that are exposed to the Internet and they fear that their internal network may
be vulnerable to an attack. They have a single perimeter rewall, but they dont know if that is enough. Matts job
is to assess the situation and make recommendations as to how Trey Research can protect their data.
1. What should Matt recommend that Trey Research to do with their Internet exposed servers?
a. create a perimeter network to isolate those servers from the internal network
b. outsource the associated services
c. no action is neededthe servers are fine where they are on the internal network
2. Is a single perimeter firewall sufficient for Trey Research?
a. yesa single firewall provides more than enough protection in any environment
b. noTrey Researchs concerns are justified. They should have several security appliances that provide
defense in depth for their organization as well as enabling workstation software firewalls and antivirus
c. nothey should also create a DMZ
3. Does stateful packet inspection or stateless packet inspection provide
better security?
a. a stateless packet inspection because it is more efficient and can stop more
packets
b. neitherthey do not provide any type of security
c. stateful because it inspects the packets as they pass through the connection
Stateless packet
inspection is a faster
type of security and
requires less memory
but is not completely
reliable.
136 CHAPTER 3: Understanding Net work Securi t y
Answers
1. Matt should recommend that Trey Research:
a. create a perimeter network to isolate those servers from the internal network. Internet-exposed
servers and devices should not reside on an internal network. They should be segmented or
isolated into a secured part of the network.
2. Is a single perimeter firewall sufficient for Trey Research?
b. noTrey Researchs concerns are justified. They should have several security appliances that
provide defense in depth for their organization as well as enabling workstation software
firewalls and antivirus. No single solution can secure a network; however, providing several layers of
security reduces a companys exposure.
3. The better packet inspection choice is:
c. stateful, because it inspects the packets as they pass through the connection
Essential details
A firewall is a security system intended to protect an organizations network against external threatssuch
as hackerscoming from another network, such as the Internet.
Packet filtering is the process of controlling network access based on IP addresses.
Firewalls will often incorporate filters that allow or deny users the ability to enter
or leave a local area network (LAN).
A proxy server is a security appliance that manages Internet traffic to and from a
local area network and can provide other features, such as document caching and
access control.
FAST TRACK HELP
http://www.microsoft.com/windowsxp/using/security/internet/
sp2_wfintro.mspx
http://technet.microsoft.com/en-us/library/cc700828.aspx
http://technet.microsoft.com/en-us/library/cc700820.aspx
FAST TRACK HELP
_______ /3
Understand Net work Access Protecti on (NAP) 137
OBJECTIVE UNDERSTANDI NG NETWORK SECURI TY 3. 2
Understand Network Access Protection (NAP)
SCENARIO: Adventure Works is one of the nations largest suppliers of high-end sporting equipment. Twenty-ve
Adventure Works sales associates travel throughout the country selling sporting equipment to retailers. They
return to corporate headquarters every Friday with their laptops for meetings and training.
Allie Bellew is the network administrator for Adventure Works and would like to implement a method for ensur-
ing that the mobile devices are in a good state of security health when they access the corporate network
during these Friday meetings.
1. What control or strategy can Allie implement to assure security health?
a. Network Access Protection, which will verify the integrity of each mobile device
b. virus scans each time sales associates log in
c. re-imaging each laptop prior to connecting to the network
2. Aside from protecting against a virus infected laptop, what else can NAP do?
a. protect against lost data
b. nothing elseit is simply a glorified virus scan
c. verify the complete integrity of the device by checking that it has the most recent
software updates or configuration changes
3. What can Allie do about computers that are not compatible with NAP?
a. upgrade the computers that are not compatible
b. define exceptions in NAP for those devices that are not compatible
c. prevent those devices from using the network
Exceptions can be
dened for mission-
necessary systems until
they can be upgraded.
138 CHAPTER 3: Understanding Net work Securi t y
Answers
1. Allie can implement:
a. Network Access Protection, which will verify the integrity of each mobile device
2. Aside from protecting against a virus infected laptop, NAP can:
c. verify the complete integrity of the device by checking that it has the most recent software
updates or configuration changes. Systems that have not received updates can be as problematic as
systems infected by malware.
3. For computers that are not compatible with NAP, Allie should:
b. define exceptions in NAP for those devices that are not compatible
Essential details
Network Access Protection (NAP) is a new platform and solution that controls access to network resources
based on a client computers identity and compliance with corporate governance policy.
NAP enforcement points are computers or network access devices that use NAP or can be used with
NAP to require the evaluation of a NAP clients health state and provide restricted network access or
communication.
FAST TRACK HELP
http://technet.microsoft.com/en-us/network/cc984252.aspx
http://technet.microsoft.com/en-us/network/bb545879.aspx
http://www.microsoft.com/windowsserver2008/en/us/nap-faq.aspx
FAST TRACK HELP
_______ /3
Understand Net work Isolati on 139
OBJECTIVE UNDERSTANDI NG NETWORK SECURI TY 3. 3A
Understand Network Isolation
SCENARIO: Coho Winery has been in the winery business for three generations. They still produce quality wine
from the same vineyards and in the same ancient cellars. Even most of their business organization has remained
the same for decades. Its now time to update the corporate side of Coho with new technologies related to their
data-keeping infrastructure.
Karen Berg has been assigned the task of assessing Coho Winerys network infrastructure and to provide recom-
mendations based on their specic needs:
Most of the employees need Internet access.
The computers in the winery plant are isolated and dont need Internet access.
Work at home employees should have Virtual Private Network access using IP Security.
1. What can Karen do to prevent the plant computers from gaining Internet access?
a. create a VLAN that does not allow Internet access but is trunked to the main network
b. manually configure each computer so it doesnt have a gateway
c. remove Internet Explorer from the computers
2. What technology will Karen have to implement to allow Internet access for
office employees without exposing them to the Internet?
a. set up one walk-up computer that has a public IP address so it can access the
Internet
b. give each office user a dialup modem to establish an Internet connection
c. implement a router to perform Network Address Translation that will allow several
private addresses to participate on a public network
3. What Microsoft Windows Server 2008 R2 role can accomplish both the
Internet access and VPN solution?
a. DHCP
b. Remote Desktop Service
c. Routing and Remote Access Service
Most server
operating systems have
some form of routing
technology. Minimum
requirements include
having multiple network
interface cards (NICs).
140 CHAPTER 3: Understanding Net work Securi t y
Answers
1. To prevent the plant computers from gaining internet access, Karen can:
a. create a VLAN that does not allow Internet access but is trunked to the main network
2. To allow Internet access for office employees without exposing them to the Internet, Karen can:
c. implement a router to perform Network Address Translation that will allow several private
addresses participate on a public network. Most retail wireless routers perform Network Address
Translation or Port Address translation, which will allow home network devices (Xbox, laptops, and so
on) to have Internet access.
3. Microsoft Windows Server 2008 R2 can accomplish both the Internet access and VPN solution with:
c. Routing and Remote Access Service (RRAS). RRAS can serve as both a VPN and Internet gateway.
VPN access can be secured using several security protocols including IP Security (IPsec).
Essential details
Network Address Translation (NAT) is the process of converting between IP addresses used within an
intranet or other private network and Internet IP addresses.
Routing is the process of forwarding packets between networks from source to destination.
A Virtual LAN (VLAN) is a group of hosts with a common set of requirements that communicate as if they
were attached to the same broadcast domain, regardless of their physical location.
FAST TRACK HELP
http://technet.microsoft.com/en-us/network/bb531150.aspx
http://technet.microsoft.com/en-us/network/bb545655.aspx
http://www.microsoft.com/downloads/en/details.
aspx?FamilyID=7E973087-3D2D-4CAC-ABDF-CC7BDE298847&displaylang=en
http://en.wikipedia.org/wiki/Virtual_LAN
FAST TRACK HELP
n
_______ /3
Understand Net work Isolati on 141
OBJECTIVE UNDERSTANDI NG NETWORK SECURI TY 3. 3B
Understand Network Isolation
SCENARIO: Arlene Huff is the systems administrator for Margies Travel and has been very busy in recent weeks
securing company and customer data. There had been suspicious activity on the network, but thankfully Arlenes
actions to track network users have secured the system. But the challenge of securing condential data is an
ongoing task.
The owner of the company, Margie, would like her remote travel agents to have access to the corporate network
so that they can check email and post appointments booked for that day. Margie has decided to allow the travel
agents to use their home computers but must be assured that the information is secured. The security of client
information is her top priority.
1. What would be the best general solution for Margies Travel?
a. implement a VPN server to allow the travel agents remote access
b. set up a modem bank and have the travel agents purchase modems for their home computers so they
can dial the office
c. there isnt a solution for what Margie wants
2. What is a potential risk in having the travel agents use their home computers
for VPN access?
a. nothingthe VPN handles everything and encrypts the data
b. the travel agents may forget to disconnect which will keep the VPN connection
open preventing others from connecting
c. simply having a VPN does not prevent potential viruses and malware on the
home computer from infecting the network
3. Arlene is worried about would-be attackers penetrating the VPN. What can
she set up to lure attackers to better understand their methods?
a. a honeypot outside the perimeter network, which is a falsified program that can
emulate a VPN or service
b. a fancy website that says Nothing to see here
c. a fake VPN that never answers
Honeypots are
located all across the
Internet and are used to
discover methods that
attackers might use to
compromise a system.
142 CHAPTER 3: Understanding Net work Securi t y
Answers
1. The best general solution for Margies Travel is to:
a. implement a VPN server to allow the travel agents remote access. She can configure the VPN to
use several methods of encryption.
2. The risk in having the travel agents use home computers for VPN access is that::
c. simply having a VPN does not prevent potential viruses and malware on the home computer
from infecting the network. Arlene can use Direct Access, which is new with Windows 7 and Windows
Server 2008 R2, to help mitigate potential risks.
3. To lure attackers to better understand their methods Arlene can create:
a. a honeypot outside the perimeter network, which is a falsified program that can emulate
a VPN or service
Essential details
A perimeter network (also known as DMZ, demilitarized zone, and screened subnet) is a physical or logical
network that contains and exposes an organizations external services to a larger, untrusted network, usually
the Internet.
Internet Protocol Security (IPsec) is an Internet protocol security standard that provides a general
policybased IP layer security mechanism that is ideal for providing host-by-host
authentication. IPsec policies are defined as having security rules and settings that
control the flow of inbound data.
Virtual private network (VPN) nodes on a public network such as the Internet
communicate among themselves using encryption technology so that the messages are
as safe from being intercepted and understood by unauthorized users, as though the
nodes were connected by private lines.
FAST TRACK HELP
http://technet.microsoft.com/en-us/network/dd420463.aspx
FAST TRACK HELP
es are es are
the the
_______ /3
Understand protocol securi t y 143
OBJECTIVE UNDERSTANDI NG NETWORK SECURI TY 3. 4
Understand protocol security
SCENARIO: Since Todd Rowe, the network administrator at the Graphic Design Institute, implemented stronger
security measures to protect student data, the number of reported leaks has fallen to zero! The administration is
pleased but Todd knows it is a constant battle to keep data secure from attacks.
Todds friend Neil Black is an expert on the methods used to attack private data stores. Todd has asked Neil to
give a presentation to the administration and ofce employees on network security, protocol security measures,
attack methods, and prevention. Todd knows that an informed staff is part of the complete strategy in preventing
and intercepting attacks.
1. What type of attack configures a computer to appear as another computer on a trusted network by
using the IP address or the physical address?
a. identity spoofing
b. computer faking
c. application-layer attack
2. What security protocol can help protect data from being modified, corrupted,
or accessed without authorization?
a. DNSSEC
b. IP Security (IPsec)
c. NetBIOS
3. What type of an attack poisons a network or computer to the point
where the system is rendered unusable?
a. man-in-the-middle attack
b. password attack
c. denial of service (DOS) attack
There are several
forms of distributed
denial of services (DOS)
attacks that can either
hinder a computer, server,
or application from
functioning.
144 CHAPTER 3: Understanding Net work Securi t y
Answers
1. An attack that configures a computer to appear as another computer on a trusted network is:
a. identity spoofing
2. The security protocol that can help protect data from being modified, corrupted, or accessed without
authorization is:
b. IP Security (IPsec). Ipsec can be used not only for VPN security but also with local area network traffic.
80 percent of most security attacks come from within the organization. Assuming that the data inside
the perimeter firewall is safe is a dangerous assumption.
3. An attack that poisons a network or computer to the point where the system is rendered unusable is a:
c. denial of service (DOS) attack
Essential details
Sniffing is the act of monitoring network traffic for data, such as cleartext passwords or configuration
information.
Identity spoofing (IP address spoofing) occurs when the attacker uses an IP address of a network,
computer, or network component without being authorized to do so.
Internet protocol security (IPsec) supports network-level data integrity, data confidentiality, data origin
authentication, and replay protection. Because IPsec is integrated at the Internet layer
(layer 3), it provides security for almost all protocols in the TCP/IP suite.
Domain name system (DNS) is a hierarchical, distributed database that contains
mappings between names and other information, such as IP addresses. DNS allows users
to locate resources on the network by converting friendly, human-readable names
such as www.microsoft.com to IP addresses that computers can connect to.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc959354.aspx
http://technet.microsoft.com/en-us/library/ee649205(WS.10).aspx
FAST TRACK HELP
users
_______ /3
4
Understanding
Security Software
IN THI S CHAPTER
4.1 Understand client protection
4.2 Understand email protection
4.3 Understand server protection
146 CHAPTER 4: Understanding Securi t y Sof t ware
Understand cli ent protecti on 147
OBJECTIVE UNDERSTANDI NG SECURI TY SOFTWARE 4. 1
The hash rule
creates a hash checksum
based on the executable.
The path rule restricts
software located within a
certain path.
Understand client protection
SCENARIO: Jeff Hay is the network administrator for Tailspin Toys. During the off-season for toy sales, the Tail-
spin technology staff is kept busy maintaining and upgrading various systems in preparation for the busy holiday
sales spike.
Jeff is eager to have this time to service all of the computers and update the software. He is concerned about
company employees installing software from the Internet. Jeff realizes that using reputable antivirus software can
only do so much. The network consists of a mix of Windows XP, Windows 7, and Windows Server 2008 R2.
1. What can Jeff do to ensure that the computers have the latest security updates?
a. implement Windows Software Update Services to control all Microsoft updates
for both the operating systems and any Microsoft product in use
b. come in early every Monday and run Windows Updates on each computer
c. email company employees and instruct them to perform Windows Updates during their lunch breaks
2. What can Jeff do to prevent company employees from downloading and installing software from
the Internet?
a. enable User Account Control on all Windows 7 computers as well as configure
software restriction policies
b. send a strongly worded email with the Internet Usage Policy attached to all users
c. disable Internet access for all users
3. What method should Jeff use to identify Internet software in Software
Restriction Policies?
a. hash rule
b. path rule
c. zone rule
148 CHAPTER 4: Understanding Securi t y Sof t ware
Answers
1. To ensure that the computers have the latest security updates, Jeff can:
a. implement Windows Software Update Services to control all Microsoft updates for both
the operating systems and any Microsoft product in use
2. To prevent employees from downloading and installing software from the Internet, Jeff can:
a. enable User Account Control on all Windows 7 computers as well as configure software
restriction policies
3. To identify Internet software in Software Restriction Policies, Jeff can use:
c. zone rule
Essential details
Antivirus is a computer program that scans a computers memory and mass storage to identify, isolate, and
eliminate viruses, and also examines incoming files for viruses as the computer receives them.
User account control (UAC) helps prevent malicious programs (malware) from damaging a computer and
helps organizations deploy a better-managed desktop. With UAC, applications and tasks always run in the
security context of a non-administrator account, unless an administrator specifically authorizes
administrator-level access to the system.
FAST TRACK HELP
http://www.microsoft.com/security_essentials/market.aspx
http://technet.microsoft.com/en-us/library/bb457141.aspx
http://technet.microsoft.com/en-us/library/bb456987.aspx
http://windows.microsoft.com/en-ZA/windows7/what-is-user-account-control
FAST TRACK HELP
trol
_______ /3
Understand email protecti on 149
OBJECTIVE UNDERSTANDI NG SECURI TY SOFTWARE 4. 2
Antivirus software
on an email server
does not provide
protection against
spam.
Understand email protection
SCENARIO: Recently the Coho Winery has experienced a series of problems with email spam; some employees
have even fallen prey to identity theft through phishing scams. John Kane is the systems administrator for Coho
Winery and the task of resolving the problems has landed directly on his desk. After some research he has come
up with some solutions. John intends to address these issues by implementing various security measures and
most important, providing some much-needed company education as it relates to best practices while using
email.
1. What can John do to help reduce the amount of spam that hits their Microsoft Exchange server?
a. at a minimum, enable reverse DNS lookup on the SMTP virtual server
b. disable Internet email
c. change their domain name
2. What should Coho users do when they receive an email from a company they know with a request
to click the link to verify their account information?
a. delete the email
b. forward to the rest of the company with a warning not to click on the link
c. click the link because they know that it is a legitimate message based on
the company name
3. Aside from enabling reverse DNS lookups, what else can John do to secure
his Exchange server?
a. enable Autodiscover
b. add Sender Policy Framework (SPF)
c. update the antivirus software
150 CHAPTER 4: Understanding Securi t y Sof t ware
Answers
1. To help reduce the amount of spam that hits their Microsoft Exchange server, John can:
a. at a minimum, enable reverse DNS lookup on the SMTP virtual server. Configuring the system to do
a reverse DNS lookup crosschecks the domain name with a PTR record that is the IP address associated
with that domain name. If the IP address does not match the record associated with that domain name, it
is not delivered.
2. When users receive an email from a company they know with a request to verify their account information,
they should:
a. delete the email. Companies will not ask for account information through email in todays climate.
Users should be diligent when receiving an email like this. They can also call the company to alert them
of the message.
3. Aside from enabling reverse DNS lookups, John can:
b. add Sender Policy Framework (SPF). SPF allows the administrator to configure the server to establish
who is allowed to send email from their domain.
Essential details
Spam is unsolicited, unwanted email sent by someone with whom the recipient has no personal or business
relationship.
Phishing and pharming are techniques used to trick computer users into revealing
personal or financial information.
An SPF record is an extension of the SMTP protocol that prevents spammers from
forging the From fields in email messages by verifying that the IP address in the
SMTP Received header is authorized to send email for the senders domain.
Spoofing is the impersonation of an email sender, IP connection, or a domain that
causes an email message to appear as though it originates from a sender other than
the actual sender of the message.
FAST TRACK HELP
http://technet.microsoft.com/en-us/exchange/dd251269.aspx
http://www.microsoft.com/athome/security/email/phishing/video1.mspx
http://www.microsoft.com/presspass/features/2003/nov03/11-17spamfilter.mspx
FAST TRACK HELP
m m
at
han
_______ /3
Understand ser ver protecti on 151
OBJECTIVE UNDERSTANDI NG SECURI TY SOFTWARE 4. 3
Stronger passwords
do not reduce the
exposure of a domain
controller.
Understand server protection
SCENARIO: A few years ago Humongous Insurance (HI) reorganized their business and technology infrastructure.
Alfons Parovsky has recently been hired as the server administrator for HI. The records regarding the security
updates are rather sketchy and he does not want any major security lapses to occur during his time as the
administrator. To be sure everything is up to standards, Alfons has decided to immediately perform a security
assessment on the datacenter. He would like to ensure that the servers meet all the necessary security
requirements and are being updated regularly. Alfons also wants to ensure that HI does not have any
exposures to the networks in their remote locations.
1. What tool can Alfons use to assess HI servers have any vulnerabilities related to the operating
system and installed software?
a. Microsoft Baseline Security Analyzer
b. Event Viewer
c. Resource Monitor
2. What service can Alfons enable to ensure that the servers are receiving all necessary software
updates?
a. Windows Backup Service
b. Routing and Remote Access Service
c. Windows Software Update Service
3. What can Alfons do to ensure that the domain is secure in the remote locations?
a. install a Read-Only domain controller in the remote sites
b. remove any servers in the remote sites and have employees transfer files
using email
c. enforce stronger password policies in the remote sites using fine-grained passwords
152 CHAPTER 4: Understanding Securi t y Sof t ware
Answers
1. To assess vulnerabilities related to the operating system and installed software, Alfons can use:
a. Microsoft Baseline Security Analyzer. MBSA is an easy-to-use tool that can provide instant feedback
and resources to identify potential vulnerabilities on servers and workstations. It analyzes the operating
system and any installed Microsoft software.
2. To ensure that the servers are receiving all necessary software updates, Alfons can enable:
c. Windows Software Update Service. Alfons can create a separate group for his servers so that he can
selectively manage what updates are installed and when.
3. To ensure that the domain is secure in the remote locations, he can:
a. install a Read-Only domain controller (RODC) in his remote sites. Read-only domain
controller (RODC) is a new type of domain controller in the Windows Server 2008 operating system.
With an RODC, organizations can easily deploy a domain controller in locations where physical security
cannot be guaranteed.
Essential details
DNS dynamic update enables DNS client computers to register and dynamically update their resource
records with a DNS server whenever changes occur.
Microsoft Baseline Security Analyzer (MBSA) is a tool designed for the IT professional
that helps small and medium-sized businesses determine their security state
in accordance with Microsoft security recommendations and offers specific
remediation guidance.
Windows Server Update Services (WSUS) enables information technology
administrators to deploy the latest Microsoft product updates to computers
that are running the Windows operating system.
FAST TRACK HELP
http://technet.microsoft.com/en-us/security/cc184923.aspx
http://technet.microsoft.com/en-us/security/cc185712.aspx
http://technet.microsoft.com/en-us/library/cc755058(WS.10).aspx
FAST TRACK HELP
_______ /3
MTA 98-349
WINDOWS
OPERATING SYSTEM
FUNDAMENTALS
1
Understanding
Operating System
Congurations
IN THI S CHAPTER
1.1/1.2 Congure Control Panel options; Congure desktop settings
1.3 Understand native applications and tools
1.4/1.5 Understand mobility; Understand remote management and
assistance
Conf i gure Control Panel opti ons; Conf i gure desktop set tings 157
Congure Control Panel options; Congure desktop settings
SCENARIO: Lori Penor is the system administrator for Coho Winery. Coho Winery has just upgraded ve of their
computers to Windows 7 Professional; however, the computers need to be congured for optimal performance.
They have also purchased three additional computers preloaded with Windows 7 Professional. Loris task is to
create a consistent desktop for the winery staff. In addition, Coho Winery has an employee with vision problems,
so Lori must accommodate that workers needs with an appropriate workstation display. Last but not least, due to
the delicate nature of grapes and their dependency on weather, users must have quick access to the forecast so
they can schedule harvesting tasks accordingly.
1. How can Lori accommodate the employee with special visual needs with Windows 7?
a. Purchase a larger screen.
b. Configure the Ease Of Access magnifier and train the worker how to use it.
c. Adjust the screen resolution so that it is larger.
2. What can Lori do to provide immediate weather forecasts?
a. Place each workstation strategically by a window so users can simply look out the window to see what
the weather is like.
b. Print out the forecast every day and place it in each employees in-basket.
c. Add to each users computer display a Weather gadget configured for his
or her ZIP code and in large view, which will display a three-day forecast.
3. What can Lori do to help optimize the five upgraded workstations
without adding more hardware upgrades?
a. Configure the workstations to use the Windows Classic theme, which uses
less memory.
b. Delete files to free up drive space.
c. Encourage her users to take a coffee break while their computers are processing.
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM CONFI GURATI ONS 1. 1/1. 2
Gadgets can
be congured
for local news,
time zones, and
weather.
158 CHAPTER 1: Understanding Operating System Conf i gurati ons
Answers
1. How can Lori accommodate the employee with special visual needs with Windows 7?
b. Configure the Ease Of Access magnifier and train the worker how to use it. The Magnifier will
work better then adjusting the screen resolution, which would degrade the sharpness of the display.
Purchasing a larger screen doesnt solve the issue without further configuration.
2. What can Lori do to provide immediate weather forecasts?
c. Add to each users computer display a Weather gadget configured for his or her ZIP code
and in large view, which will display a three-day forecast.
3. What can Lori do to help optimize the five upgraded workstations without adding more hardware
upgrades?
a. Configure the workstations to use the Windows Classic theme, which uses less memory. Freeing
up drive space does not optimize their systems unless other tools, such as a disk defragmenter, are used.
Essential details
A gadget is a single-purpose application like news, pictures, or games that can be installed on the Windows
7 desktop.
The Aero desktop features a translucent glass design with subtle window animations and new window
colors.
The Control Panel is a utility that enables users to configure operating system
features and perform related tasks such as hardware and software setup and
configuration, security, system maintenance, and user account management.
FAST TRACK HELP
http://www.microsoft.com/windows/windows-7/features/gadgets.aspx
http://www.microsoft.com/enable/training/windowsvista/eoa.aspx
FAST TRACK HELP
_______ /3
Understand nati ve appli cati ons and tools 159
Understand native applications and tools
SCENARIO: Michael Patten is the desktop administrator for Tailspin Toys. His job is to help employees to be as
efcient as possible with their computer tasks. Members of the sales department have asked Michael to nd
an easier way for them to access their favorite websites without having to navigate to their Favorites folders.
They also would like Michael to help them distribute training videos for new employees on the toy assembly line.
Finally, they would like an easier method to access frequently used folders on the company network. Michaels
budget does not allow for purchasing additional equipment or software. The good news is that the company
recently purchased new workstations running Windows 7 Professional for the entire workforce.
1. How can Michael distribute the training videos without purchasing new software?
a. Michael can burn the video to a DVD and make sure the employees each sign it out for the weekend.
b. Michael can stream the training video across the network using Windows Media Player.
c. Michael can schedule in-person trainings during regular employee meetings.
2. What can Michael do to make employees favorite websites easier to access?
a. Michael can create a folder that contains shortcuts for each site on their desktops.
b. Michael can assign each website as an additional tabbed Windows Internet
Explorer home page.
c. Michael can ensure that all users are running Internet Explorer 9 and train them
how to pin their favorite websites to the taskbar.
3. What Windows Explorer technology can Michael use to make folders
easier to access?
a. File and folder compression
b. Jump lists
c. Folder options
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM CONFI GURATI ONS 1. 3
Windows Media
Player and Media
Center can both
share media across
a network to other PCs.
160 CHAPTER 1: Understanding Operating System Conf i gurati ons
Answers
1. How can Michael distribute the training videos without purchasing new software?
b. Michael can stream the training video across the network using Windows Media Player.
Windows 7 Professional includes Windows Media Player, which has the ability to share video across
networks.
2. What can Michael do to make employees favorite websites easier to access?
c. Michael can ensure that all users are running Internet Explorer 9 and train them how to pin
their favorite websites to the taskbar. Creating shortcuts in a folder may be more cumbersome, and
training the users to pin their own websites allows them to customize their favorites without having to
ask Michael for help.
3. What Windows Explorer technology can help Michael make their folders easier to access?
b. Jump lists
Essential details
The System Configuration utility (MSCONFIG) helps identify problems with Windows configuration.
It does not manage the programs that run when Windows starts.
Windows Media Player is a client/control that receives a stream for playback from a server
providing Windows Media files or local content. This is not t he same as the Windows
Media Center, which can show, pause, and record HDTV, show DVDS, play music,
display photos, show online shows, and share media from one PC to another.
A safer Internet browsing experience is possible thanks to security features
including ActiveX Filter, a cross-site scripting filter, and InPrivate Browsing.
FAST TRACK HELP
http://windows.microsoft.com/en-US/windows7/products/
features/windows-media-player-12
http://windows.microsoft.com/en-US/internet-explorer/products/
ie-9/features/pinned-sites
FAST TRACK HELP
,
_______ /3
Understand mobili t y; Understand remote management and assistance 161
Understand mobility; Understand remote management and assistance
SCENARIO: Dean Halstead is an independent consultant who manages the mobile travel agents for Margies
Travel. All the travel agents have laptops running Windows 7 Professional. Margie has asked Dean to nd
a solution for managing these laptops while her staff is on the road. Dean jokes that he would be more than
happy to travel to Cancun to troubleshoot laptops, but he understands Margies request. The agents have several
complaints that Margie is eager to resolve. The agents need to adjust the screen brightness and power settings
to conserve battery life when they are in airports or in ight. They also need access to their les on the company
network when they are traveling without having to use external media or copy items back and forth.
1. What can Dean do so that the agents can adjust their laptop settings quickly and easily?
a. Create shortcuts on their desktops for each setting.
b. Train the agents to use the Windows Mobility Center, which includes tools to modify mobile settings,
including screen brightness and power settings.
c. Suggest that Margie purchase additional batteries for each agent to use when batteries run low.
2. How can Dean resolve issues on the agents laptops when they are traveling?
a. Call each agent and walk them through troubleshooting steps over the phone.
b. Ask the agents to ship their laptops back to him in the home office.
c. Enable Remote Desktop on each laptop and connect remotely to agents
laptops when needed.
3. What can Dean do to allow the agents to work on their files when offline?
a. Configure Offline Files and set up the laptops to use the Sync Center to
synchronize files when the agents log off so that files are available when
they are away from the network.
b. Create a batch file that agents can use to copy files back and forth whenever
they leave.
c. Give each agent a universal serial bus (USB) memory stick to use when they need to
copy their files.
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM CONFI GURATI ONS 1. 4/1. 5
Ofine folders can
be congured to
make les available
in an outage or with
mobile users.
162 CHAPTER 1: Understand mobili t y; Understand remote management and assistance
Answers
1. What can Dean do so that the agents can adjust their laptop settings quickly and easily?
b. Train the agents to use the Windows Mobility Center which includes tools to modify mobile
settings including screen brightness and power settings.
2. How can Dean resolve issues on the agents laptops when they are traveling?
c. Enable Remote Desktop on each laptop and connect remotely to agents laptops when needed.
This would also involve locating each laptops external IP address or having to negotiate firewall
settings. Remote Assistance would be an option as well.
3. What can Dean do to allow the agents to work on their files when offline?
a. Configure Offline Files and set up the laptops to use the Sync Center to synchronize files when
the agents log off so that files are available when they are away from the network.
Essential details
Remote Desktop Connection is a technology that allows a user to sit at a computer (sometimes called
the client) and connect to a remote computer (sometimes called the host) in a different location.
The Sync Center is a feature of Windows that enables the user to keep information and files synchronized
between a computer and data stored in folders on network servers and with certain mobile devices that
are compatible with Sync Center.
The Windows Mobility Center displays the most commonly used settings, such as
brightness, volume, battery status, and wireless network status. Different tiles
are displayed depending on the system, and some tiles are added by the
laptop manufacturer.
FAST TRACK HELP
http://windows.microsoft.com/en-US/windows-vista/
Sync-Center-frequently-asked-questions
http://windows.microsoft.com/en-US/windows7/
Using-Windows-Mobility-Center
FAST TRACK HELP
as
_______ /3
2
Installing and Upgrading
Client Systems
IN THI S CHAPTER
2.1/2.2 Identify Windows operating system editions; Identify upgrade
paths
2.3 Understand installation types
2.4 Understand virtualized clients
I denti f y Windows operating system edi ti ons; I denti f y upgrade paths 165
OBJECTIVE I NSTALLI NG AND UPGRADI NG CLI ENT SYSTEMS 2. 1/2. 2
Identify Windows operating system editions; Identify upgrade paths
SCENARIO: Aneta Olecka is the desktop support manager for Humongous Insurance. Her supervisor has asked
her to determine the viability of upgrading their existing systems running Windows XP Professional and Windows
Vista Business to Windows 7. This is no easy task for such a large company. The rst step for Aneta is to determine
whether their existing systems can be upgraded. In addition to meeting the necessary system requirements, she
must determine which edition of Windows 7 she can upgrade to from Windows Vista Business and determine if
the existing programs and hardware are compatible with Windows 7. And, of course, she needs to transfer any
existing data and programs to the upgraded systems.
1. What is the easiest method to determine the issues that Aneta may run into if she proceeds with
the upgrade?
a. Upgrade a system running Windows XP and a system running Windows Vista Business over the
weekend to discover what works and what doesnt.
b. Assume that Windows 7 will work on the machines running Windows XP and almost guarantee they will
run on the ones running Windows Vista Business because upgrades always work without issues.
c. Aneta should download the Windows 7 Upgrade Advisor, check each system, and view the report of
potential issues.
2. What editions(s) of Windows 7 would Aneta be able to upgrade to from
Windows Vista Business?
a. She cant; there isnt an upgrade path from Windows Vista Business.
b. She could upgrade to either Windows 7 Professional or Ultimate edition.
c. She can upgrade to any version she chooses.
3. How can Aneta copy the existing data from the systems running Windows XP
to the upgraded systems running Windows 7?
a. Use Windows Easy File Transfer, which is a free download from Microsoft.
b. Copy all data and program settings to universal serial bus (USB) drives and then
re-create those directory structures on Windows 7.
c. Tell her users to email themselves all their personal data and record all their settings.
Windows 7
Upgrade Advisor
is a free download
that scans the PC
for any potential
compatibility issues.
166 CHAPTER 2: Installing and Upgrading Cli ent Systems
Answers
1. What is the easiest method to determine the issues that Aneta may run into if she proceeds with the
upgrade?
c. Anetas should download the Windows 7 Upgrade Advisor, check each system, and view the
report of potential issues.
2. What editions(s) of Windows 7 would Aneta be able to upgrade to from Windows Vista Business?
b. Upgrade to either Windows 7 Professional or Ultimate edition.
3. How can Aneta copy the existing data from the systems running Windows XP to the upgraded systems
running Windows 7?
a. Use Windows Easy File Transfer, which is a free download from Microsoft.
Essential details
Upgrade Advisor scans a PC for potential issues with hardware, devices, and installed programs
and recommends remedies before upgrading to Windows 7.
Computer systems are upgraded to change to a newer, usually more powerful or sophisticated operating
system version.
Windows Easy File Transfer makes is easier to transfer files and settings from
older systems to Windows 7.
FAST TRACK HELP
http://windows.microsoft.com/en-US/windows7/products/features/
windows-easy-transfer
http://www.microsoft.com/windows/windows-7/get/upgrade-advisor.aspx
http://windows.microsoft.com/en-us/windows7/help/
upgrading-from-windows-vista-to-windows-7
http://windows.microsoft.com/en-US/windows7/help/
upgrading-from-windows-xp-to-windows-7
FAST TRACK HELP
_______ /3
Understand installati on t ypes 167
OBJECTIVE I NSTALLI NG AND UPGRADI NG CLI ENT SYSTEMS 2. 3
Understand installation types
SCENARIO: Phyllis Harris was recently hired by World Wide Importers as their desktop deployment manager.
Phyllis claims that she can save the company thousands of dollars by streamlining their desktop rollout process.
Historically, World Wide Importers installed their workstations using the High Touch Installation (HTI) strategy.
They had two IT members perform installations all day long when new PCs had to be rolled out. This was ne
when they were a small company with only 20 desktops, but now they have 500 computers and roll out more
than 150 every six months as they continue to grow. Phyllis plans to use several tools to automate installations
with limited user interaction.
1. What tool can Phyllis use to deploy Windows 7 installation over the network?
a. Use a bootable floppy disk to connect to the network share and run Setup.exe from the distribution
point.
b. Use Windows Deployment Services (WDS) to perform multiple installations simultaneously.
c. Run Windows Update over the network to make sure all the installed systems are updated.
2. What deployment strategy would best suit World Wide Importers?
a. Hire high school interns to perform installations for two months.
b. Use Lite Touch Installation (LTI).
c. Use Zero Touch Installation (ZTI).
3. What can Phyllis create so that the Windows 7 installations will run
automatically with preconfigured settings?
a. A batch file that copies all the necessary information and launch it after the
installation completes.
b. A bootable USB device that contains all the drivers and necessary software to
complete the installati on.
c. An answer file to embed on her installation media or WDS distribution folder.
An answer le
can be used to
congure Windows
settings during
installation.
168 CHAPTER 2: Installing and Upgrading Cli ent Systems
Answers
1. What tool can Phyllis use to deploy Windows 7 installation over the network?
b. Use Windows Deployment Services (WDS) to perform multiple installations simultaneously.
2. What deployment strategy would best suit World Wide Importers?
c. Use Zero Touch Installation (ZTI). This strategy requires no interaction during deployment.
The process is fully automated through System Center Configuration Manager R2.
3. What can Phyllis create so that the Windows 7 installations will run automatically with preconfigured
settings?
c. An answer file to embed on her installation media or WDS distribution folder.
Essential details
An answer file is a file used to configure Windows settings during installation. The answer file contains all
the settings that are required for an unattended installation.
High Touch Installation (HTI) is a manual deployment in which Windows is installed on each client using
the retail installation DVD and manually configured on each computer.
Lite Touch Installation (LTI) requires limited interaction during deployment. Interaction occurs at the
beginning of the installation, but the remainder of the process is automated.
Zero Touch Installation (ZTI) requires no interaction during deployment.
The process is fully automated through System Center Configuration Manager R2.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/ee523216(WS.10).aspx
http://technet.microsoft.com/en-us/library/dd919179(WS.10).aspx
http://technet.microsoft.com/en-us/library/dd919178(WS.10).aspx
http://technet.microsoft.com/en-us/windows/dd179859.aspx
FAST TRACK HELP
.
_______ /3
Understand vir tuali zed cli ents 169
OBJECTIVE I NSTALLI NG AND UPGRADI NG CLI ENT SYSTEMS 2. 4
Understand virtualized clients
SCENARIO: Christian Hess is a systems administrator for Woodgrove Bank. The board of directors has asked Christian
to check the feasibility of upgrading their desktops to Windows 7. Christian has been anticipating this request since
the release of the operating system and has done quite a bit of research on the subject. The banking industry is
always one of the last business segments to switch to newer technologies, primarily due to their dependency on older
nancial software and being governed by stringent regulatory agencies that ensure banks duciary responsibilities.
Christian is aware that some of the banks software will not run on Windows 7 at this time. The board also has asked
for an alternative to rolling out new PCs so often and if there is a better way to manage their infrastructure.
1. What could Christian use to run applications that run only on Windows XP?
a. He can have two PCs at each desk and teller window configured with a keyboard-video-mouse (KVM)
switch. One PC would run Windows 7 and the supported applications, and the other would run
Windows XP and the older applications.
b. He can have a centralized PC in the middle of the bank lobby running Windows XP with all necessary
applications installed. Each user can sign up to use the machine to complete their work.
c. He can configure each Windows 7 PC with Windows XP Mode and install
the older applications in XP Mode.
2. What Windows 7 editions can Christian consider using if he wants
to use Windows XP Mode?
a. Home, Millennium, and 98 Second editions
b. Professional, Enterprise, and Ultimate editions
c. Business, Professional, and Super Ultimate Premium editions
3. What technology can Christian consider as a potential solution to
the boards request to reduce the number of PC rollouts?
a. Christian should consider Virtual Desktop Infrastructure (VDI).
b. He should tell the board that upgrading PCs is just part of normal business
operations and they will have to come to terms with it.
c. Christian should consider Remote Desktop Services (RDS).
Windows 7 Home
Premium and
Starter do not
support XP Mode.
170 CHAPTER 2: Installing and Upgrading Cli ent Systems
Answers
1. What could Christian use to run applications that run only on Windows XP?
a. He can configure each Windows 7 PC with Windows XP Mode and install the older applications
in XP Mode. Christian should verify that the applications will run in XP Mode and comply with any
regulatory agencies.
2. What Windows 7 editions can Christian consider using if he wants to use Windows XP Mode?
b. Professional, Enterprise, and Ultimate editions. XP Mode is not supported on Home Premium
or Starter edition.
3. What technology can Christian consider as a potential solution to the boards request to reduce the number
of PC rollouts?
c. Christian should consider Virtual Desktop Infrastructure (VDI). VDI allows an administrator to have
a central point of desktop management and recoverability.
Essential details
Microsoft Virtual Desktop Infrastructure (VDI) is a centralized desktop delivery solution. The concept
of VDI is to store and run desktop workloads, including a Windows client, applications, and data in a
server-based virtual machine in a data center.
Virtual desktop is a desktop enhancement tool that expands the computers desktop
environment through the use of software.
A virtual machine is a computer within a computer, implemented in software.
A virtual machine emulates a complete hardware system, from processor to network
card, in a self-contained, isolated software environment.
Windows XP Mode comes as a separate download and works only with Windows
7 Professional, Ultimate, and Enterprise editions.
FAST TRACK HELP
http://windows.microsoft.com/en-us/windows7/products/features/
windows-xp-mode
http://www.microsoft.com/virtualization/en/us/products-desktop.aspx
http://technet.microsoft.com/en-us/edge/microsoft-virtual-desktop-infrastructure-vdi-explained.aspx
FAST TRACK HELP
ork
ws ws
_______ /3
3
Managing Applications
IN THI S CHAPTER
3.1 Understand application installations
3.2 Understand user account control (UAC)
3.3 Remove malicious software
3.4 Understand services
3.5 Understand application virtualization
Understand appl i cati on i nstal lati ons 173
Understand application installations
SCENARIO: April Reagan works for Tailspin Toys as the desktop administrator in charge of maintaining 35 PCs.
Although working in a toy factory sounds like it would be a lot of fun, its quite a challenge for April to keep
up with changing technology and new applications. Recently, she was assigned the task of installing a new toy
design application on 20 PCs. Unfortunately employees on several of these computers have had access to this
software and it has not been updated recentlya situation that complicates Aprils installation task. Fortunately
her company is using computers that run Microsoft Windows 2008 R2 Active Directory Domain Services (AD DS).
April is faced with several options to complete the installation and would like to make it as manageable and
efcient as possible. She can perform manual installations, copy the les to a folder on the network, and perform
network installations, or she can use Group Policy to complete her tasks.
1. What installation method would be the best choice for April?
a. She should do a manual installation at each PC.
b. She should perform network installations because this is the easiest method.
c. She should use Group Policy so that she can centrally manage, secure, and update all installations.
2. If April chooses Group Policy to manage her software, how will she disable it
for the users who shouldnt have access to the software?
a. She can run down and uninstall the software between shifts and then rerun Group
Policy when the permitted users come back.
b. The software can be selected to uninstall when it falls out of scope when another
user that is not authorized to run the software logs in.
c. She can assume that the users wont possibly search to see what programs are
running on the system.
3. What is the best way for April to update the software?
a. She can add upgrades to the software within Group Policy.
b. She can uninstall the software manually on each PC, recreate the Group Policy package,
and then reinstall the software.
c. She can create instructions for the users to update the software themselves.
OBJECTIVE MANAGI NG APPLI CATI ONS 3. 1
age,
Group Policies
allow for central
management and
deployment of software
updates and security.
174 CHAPTER 3: Managi ng Appl i cati ons
Answers
1. What installation method would be the best choice for April?
c. She should use Group Policy so that she can centrally manage, secure, and update all
installations. Group Policy allows the administrator to install software based on user, create consistency
through security, and centrally update and deploy applications.
2. If April chooses Group Policy to manage her software, how will she disable it for the users who shouldnt
have access to the software?
b. The software can be selected to uninstall when it falls out of scope when another user that is
not authorized to run the software logs in.
3. What is the best way for April to update the software?
a. She can add upgrades to the software within Group Policy.
Essential details
An application is a program designed to assist in the performance of a specific task, such as word
processing, accounting, or inventory management.
Group Policy is a collection of settings stored within documents created by the Group Policy snap-in,
a utility in Windows. These settings are stored at the domain level and affect users and computers
contained in sites, domains, and organizational units.
User Account Control (UAC) is a feature in Windows that helps the user stay in control
of the computer by issuing notices when a program makes a change that requires
administrator-level permission.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc738858(WS.10).aspx
http://windows.microsoft.com/en-US/windows7/products/features/
user-account-control
http://technet.microsoft.com/en-us/windowsserver/bb310732.aspx
FAST TRACK HELP
controll
ss
_______ /3
Understand user account control (UAC) 175
Understand user account control (UAC)
SCENARIO: Jim Hance works for Alpine Ski House as the system administrator. Jim has had several problems with
the computers in the lobby that are available for Alpine Ski House patrons to check weather conditions or use the
Internet. These computers are older and run Windows XP. Jim continually has to resolve issues of malware being
installed as customers browse various websites. Jim realizes that the users are probably not intentionally installing
malicious software, so he has decided that upgrading the computers to Windows 7 will help solve the problems.
1. What feature in Windows 7 will help solve Jims problems?
a. User Account Control (UAC), which prompts users whenever modifications are being made to
the operating system
b. Aero desktop, which can include gadgets for weather forecasts
c. A Microsoft firewall
2. Jim has an Administrator account; what can he do to run the Ski Report application on new
computers without getting prompted by UAC?
a. Install the program on the old computers running Windows XP to bypass the prompts.
b. Set the User Account Control Policy setting to disable Admin Approval.
c. Set the Privilege Level to run as Administrator.
3. What does UAC help prevent?
a. UAC helps prevent users from unintentionally installing malicious software.
b. UAC prevents users from logging in as Administrator.
c. UAC prevents users from controlling user accounts.
OBJECTIVE MANAGI NG APPLI CATI ONS 3. 2
UAC is a feature
in Windows that can
help the user control
the computer.
176 CHAPTER 3: Managi ng Appl i cati ons
Answers
1. What feature in Windows 7 will help solve Jims problems?
a. User Account Control (UAC), which will prompt users whenever modifications are being made
to the operating system
2. Jim has an Administrator account; what can he do to run the Ski Report application on new computers
without getting prompted by UAC?
b. Jim can set the User Account Control Policy setting to disable Admin Approval.
3. What does UAC help prevent?
a. UAC helps prevent users from unintentionally installing malicious software.
Essential details
Malicious software is software created and distributed for harmful purposes, such as invading computer
systems with viruses, worms, or innocent-looking plug-ins and extensions that mask other destructive
capabilities.
User Account Control (UAC) is a feature in Windows that helps the user stay in control of the computer by
issuing notices when a program makes a change that requires administrator-level permission.
UAC works by adjusting the permission level of your user account. If youre doing tasks that
can be done as a standard user, such as reading email, listening to music, or creating
documents, you have the permissions of a standard user, even if youre logged on as
an administrator.
FAST TRACK HELP
http://windows.microsoft.com/en-US/windows7/products/features/
user-account-control
http://technet.microsoft.com/en-us/library/cc709691(WS.10).aspx
http://technet.microsoft.com/en-us/library/ee679793(WS.10).aspx
FAST TRACK HELP
as
_______ /3
Remove mali ci ous sof t ware 177
Remove malicious software
SCENARIO: Toni Poe works for Northwind Traders as an IT consultant. Tonis job includes removing malicious
software from PCs and laptops, as well as securing the computers. Northwind Traders, a small international
clothing business, requires that their two salespeople do a lot of traveling. The salespeople require Internet access
while they are on the road and dont always use the safest practices when they are browsing the Internet. Toni
is aware of the risks involved with a salesperson browsing the web on an open network while having a cup of
coffee, so she has researched tools that she can use to not only remove suspected malware but also prevent it
from affecting the laptops running Windows 7 Professional. Tonis budget is pretty small, so she has to make wise
decisions when choosing the software.
1. What feature of Windows 7 can help protect the laptops from spyware and other threats?
a. Windows Explorer
b. Windows Defender
c. Windows Proxy 2.0
2. Toni was given a laptop to troubleshoot. She suspects that it has become infected with malware.
What can she do to remove that malicious software safely?
a. Download and run the Malicious Software Removal Tool.
b. Nothingthe laptop is now a large paperweight.
c. Browse through each folder and Registry key to look for suspicious files.
3. What can Toni install to help prevent viruses from infecting the laptops?
She doesnt have any funds to purchase anything at this time.
a. Microsoft Security Essentials, if the company has 10 or fewer computers.
b. The Malicious Software Removal Tool.
c. Nothing is available; everything that she needs requires purchasing a license.
OBJECTIVE MANAGI NG APPLI CATI ONS 3. 3
Microsoft Security
Essentials is a free
antivirus product
available for personal
and small business
use.
178 CHAPTER 3: Managi ng Appl i cati ons
Answers
1. What feature of Windows 7 can help protect the laptops from spyware and other threats?
b. Windows Defender. Windows Defender is software that helps protect a computer against pop-ups,
slow performance, and security threats caused by spyware and other unwanted software.
2. Toni was given a laptop to troubleshoot. She suspects that it has become infected with malware. What can
she do to remove that malicious software safely?
a. Download and run the Malicious Software Removal Tool. The Malicious Software Removal Tool is
a free download that scans the system for known malware. It does not prevent malware.
3. What can Toni install to help prevent viruses from infecting her laptops? She doesnt have any funds to
purchase anything at this time.
a. Microsoft Security Essentials if the company has 10 or fewer computers.
Essential details
Malicious software (malware) is software created and distributed for harmful purposes, such as invading
computer systems in the form of viruses, worms, or innocent-seeming plug-ins and extensions that mask
other destructive capabilities.
The Registry is a central hierarchical database in Windows used to store information necessary to configure
the system for one or more users, applications, and hardware devices.
Spyware is software that performs certain behaviors, generally without appropriately
obtaining your consent first.
A virus is a small software program designed to spread from one computer to
another and to interfere with computer operations.
FAST TRACK HELP
http://www.microsoft.com/security/pc-security/malware-removal.aspx
http://www.microsoft.com/security_essentials/
http://www.microsoft.com/windows/products/winfamily/defender
/default.mspx
FAST TRACK HELP
_______ /3
Understand ser vi ces 179
Understand services
SCENARIO: Holly Holt is a systems administrator for Lucerne Publishing, a highly recognized publishing company
that specializes in barbecue cookbooks. One of the editors was having difculty printing several chapters of a
recent cookbook and contacted Holly to nd out what can be done to get the printer to work. This editor also
has informed Holly that he is continually getting warnings when he starts his computer in the morning, indicating
that his rewall has failed to start, and he is concerned that his computer may be compromised. Holly examines
his computer and when she looks at the System Event Log, she notices a Service Control Manager error indicating
that the rewall service has failed to start. Holly opens the Services console and starts the Windows Firewall
Service without any problem.
1. What can Holly do to ensure that the Windows Firewall Service starts as expected?
a. Visit the editors office every morning and manually start the service after the machine has booted.
b. Configure the service to have a delayed start temporarily and research why the service isnt starting
automatically.
c. Ask the editor not to plug into the network until she gets the issue resolved.
2. What should Holly do first to troubleshoot the editors printing issues?
a. Verify that the Print Spooler status indicates that it is running.
b. Check to be sure the printer has paper.
c. Ask the editor to email the chapters to her so she can print a copy.
3. After some investigation, Holly notices that the editor attempted to print
the same job 20 times after it failed the first time. She cannot delete the
print jobs because the queue states that it is Not Responding. What should
Holly do to clear the print queue and correct the print issues?
a. Reboot the workstation.
b. Restart the Print Spooler service from the Services console.
c. Unplug the printer, wait several minutes, and plug it back in.
OBJECTIVE MANAGI NG APPLI CATI ONS 3. 4
The Print Spooler
service loads les
to memory for later
printing.
180 CHAPTER 3: Managing Applications
Answers
1. What can Holly do to ensure that the Windows Firewall Service starts as expected?
b. Configure the service to have a delayed start temporarily and research why the service isnt
starting automatically. If the service will start after the other services load, there could be a conflict
during startup. The interim solution would be to set the startup type to a delayed startup in an effort to
get the system functioning and secured until the issue is corrected.
2. What should Holly do first to troubleshoot the editors printing issues?
a. Verify that the Print Spooler status indicates that it is running. Printing services are suspended if
the Print Spooler service is stopped.
3. After some investigation, Holly notices that the editor attempted to print the same job 20 times after it
failed the first time. She cannot delete the print jobs because the queue states that it is Not Responding.
What should Holly do to clear the print queue and correct the print issues?
b. Restart the Print Spooler service from the Services console. Print jobs can become corrupted.
Restarting the Print Spooler service clears all print queues and resets the printer objects.
Essential details
A service is an application type that runs in the system background without a user interface and is similar to
a UNIX daemon process. Services provide core operating system features, such as
web serving, event logging, file serving, printing, cryptography, and error reporting.
The System Event Log contains events logged by Windows system components.
For example, the failure of a driver or other system component to load during startup
is recorded in the system log. The event types logged by system components
are predetermined by Windows.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc785922(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc739213(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc736564(WS.10).aspx
FAST TRACK HELP
rtup t
_______ /3
Understand appl i cati on vir tual i zati on 181
Understand application virtualization
SCENARIO: Walter Harp is a systems administrator for Humongous Insurance (HI). HI is planning to deploy new
software, including Microsoft Ofce 2010. They are also upgrading their desktops to Windows 7 Professional. HI
has several third-party applications that are not compatible with Windows 7. Walter has considered running those
applications in XP Mode, but he is looking at other options that may make his job easier.
Walter wants to streamline his work and to gain the ability to not only support the olderapplications, but also
manage centrally the new applications that he is planning to deploy. HI has several remote ofces that will be
involved in this upgrade and deployment. The remote ofces have been using Remote Desktop Services (RDS) to
gain access to their corporate network.
1. What technology or method can Walter use to support the older applications?
a. Stick with using Windows XP Mode on the new workstations running Windows 7 Professional.
b. Implement Microsoft Enterprise Desktop Virtualization (MED-V) to help support the older applications
by running them in a virtual machine that can be managed centrally.
c. Purchase keyboard-video-mouse (KVM) switches and run both desktops side by side.
2. How can Walter use RDS to handle his rollout?
a. Have each user connect remotely to the RDS server to run the Office products.
b. Use the RemoteApp feature to deploy applications remotely to both internal and
mobile users without requiring them to establish an entire desktop session.
c. Sell the RDS server and use the additional funds to purchase companion PCs
for the remote offices running the older applications.
3. What technology can Walter use as an alternative to RDS to deploy Office 2010?
a. Use App-V to virtualize and centrally manage Office 2010.
b. Create DVDs of the software and allow his users to install the software themselves.
c. Use Group Policies to install Office 2010 for each user.
OBJECTIVE MANAGI NG APPLI CATI ONS 3. 5
Ofce 2010
deployment by
user conguration
is not supported.
182 CHAPTER 3: Managi ng Appl i cati ons
Answers
1. What technology or method can Walter use to support the older applications?
b. Implement Microsoft Enterprise Desktop Virtualization (MED-V) to help support the older
applications by running them in a virtual machine that can be managed centrally. MED-V is a
centrally managed solution that can eliminate application conflict as well as supports using a virtual
machine for older applications.
2. How can Walter use RDS to handle his rollout?
b. Use the RemoteApp feature to deploy applications remotely to both internal and mobile users
without requiring them to establish an entire desktop session. RemoteApp allows for deployment
of applications through several interfaces. This would also help their remote users to access applications
through a web browser.
3. What technology can Walter use as an alternative to RDS to deploy Office 2010?
a. Use App-V to virtualize and centrally manage Office 2010. App-V can be used to configure and
deploy virtual applications that can be centrally managed and updated.
Essential details
Remote Desktop Services (RDS)is a server role in Windows Server 2008 R2 that provides technologies that
enable users to access Windows-based programs that are installed on a Remote Desktop
Session Host (RD Session Host) server, or to access the full Windows desktop.RDS enables
the user to deploy and maintain software efficiently in an enterprise environment.
RemoteApp enables the user to make programs that are accessed remotely through
RDS appear as if they are running on the users local computer.
A virtual application is an application that can run in a self-contained, virtual
environment. The virtual environment contains the information necessary to
run the application on the client without installing the application locally.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/ee958112.aspx
http://www.microsoft.com/windows/enterprise/products/mdop/med-v.aspx
http://www.microsoft.com/windowsserver2008/en/us/rds-product-home.aspx
FAST TRACK HELP
ugh
px
_______ /3
4
Managing Files and
Folders
IN THI S CHAPTER
4.1 Understand le systems
4.2 Understand le and print sharing
4.3 Understand encryption
4.4 Understand libraries
Understand f il e systems 185
OBJECTIVE MANAGI NG FI LES AND FOLDERS 4. 1
Understand le systems
SCENARIO: Toni Poe is a network administrator for the outdoor sports outtting company, Adventure Works.
Adventure Works is releasing a new snowboard clothing line and anticipates sales to set new records. They have
decided to deploy laptops running Windows 7 Enterprise edition to their existing regional sales staff. Toni has
congured the staff laptops to do a daily backup to external hard drives that were purchased with each laptop.
Toni is worried that these drives may not be secure and also is concerned that they may run out of space while
being used on the road.
1. What must Toni do first to secure the external drives?
a. Remind the sales staff of the importance of these drives and that they should never let them out of their
sight . . . ever!
b. Attach a secure lockedcablefrom the laptop to the drive.
c. Verify and convert the drives to NTFS. They most certainly are FAT32 if they were purchased recently.
2. Why must Toni convert the drives to NTFS?
a. NTFS will permit her to enable compressionon the drives if she needs to free up drive space.
b. She doesnt have to convert them to NTFS; she trusts her staff to not lose the drives.
c. NTFS has built-in security for file and folder permissions.
3. What other advantages does NTFS provide?
a. NTFS supports larger volume sizes and inherent encryption.
b. Nothing; NTFS does not offer any advantages over FAT32 volumes.
c. NTFS supports only the 8.3 filename format.
An iteration, in
this context, is one trip
through the loop.
An iteration, in ti
this context, is one trip ex
through the loop. h
FAT32 does not
support drive
compression.
186 CHAPTER 4: Managing Fil es and Fol ders
Answers
1. What must Toni do first to secure the external drives?
c. Verify and convert the drives to NTFS. They most certainly are FAT32 if they were purchased
recently. Most external drives and USB flash drives are formatted in FAT32 for compatibility reasons.
2. Why must Toni convert the drives to NTFS?
a. NTFS will permit her to enable compression on the drives if she needs to free up drive space.
3. What other advantages does NTFS provide?
a. NTFS supports larger volume sizes and inherent encryption. Windows 7 also includes the
BitLocker feature, which is designed for encrypting external and mobile drives.
Essential details
FAT file system is a file system that has the file allocation table (FAT) located at the beginning of a logical
volume. FAT was designed for small disks and simple folder structures. Two copies of the FAT are stored on
the volume. If one copy of the FAT is corrupted, the other FAT is used.
NT file system (NTFS) is an advanced filesystem designed for use specifically with MicrosoftWindows NT.
It supports long filenames, full security access control, file system recovery, extremely large storagemedia,
and various features for the Windows NTPOSIX subsystem.
FAST TRACK HELP
http://windows.microsoft.com/en-US/windows-vista/
Comparing-NTFS-and-FAT-file-systems
http://windows.microsoft.com/en-US/windows7/
Convert-a-hard-disk-or-partition-to-NTFS-format
FAST TRACK HELP
_______ /3
Understand f il e and print sharing 187
OBJECTIVE MANAGI NG FI LES AND FOLDERS 4. 2
Understand le and print sharing
SCENARIO: Cassie Hicks is a desktop administrator for Fourth Coffee. The companys CIO has asked her to
network all the coffee shops computers so that they can share les and printers. All the computers are running
Windows 7 Professional. Cassie accepts the task and begins to investigate the best way to accomplish her
assignment. She knows there are les that arent condential and can be modied by anyone. She can set up
sharing with only one printer at each coffee shop. She wants the shares to be easily accessible and doesnt want
the jittery baristas clicking through the le system hunting for the daily specials yer that they need to print each
morning.
1. How can Cassie permit network files to be modified by users?
a. Enable public folder access on the computers.
b. Save the files to a USB thumb drive and insist that users copy the files to the drive.
c. Create email accounts for the users so that they can modify files and send them to one another.
2. What can Cassie do to ensure that the baristas can find the flyers they need easily?
a. Ask the baristas to use the net use command to map a drive to the shares each morning.
b. Map a network drive for each share and select the Reconnect At Logon check box.
c. Place detailed instructions on how to locate the files at each computer.
3. What can Cassie do to provide printer access to every computer in every shop?
a. Use a USB printer sharing device and cables to connect each computer
to the printer.
b. Locate the printer with the most central computer and share that printer
with all the other computers.
c. Purchase inexpensive printers for each computer.
A mapped
network drive will
be displayed in
Windows Explorer
under Network
Locations.
188 CHAPTER 4: Managing Fil es and Fol ders
Answers
1. How can Cassie permit network files to be modified by users?
a. Enable public folder access on the computers. Public folders allow all users to have complete access
to the contents. The network profile must be modified to allow this feature.
2. What can Cassie do to ensure that the baristas can find the flyersthey need easily?
b. Map a network drive for each share and select the Reconnect At Logon check box. The
Reconnect At Logon setting re-maps the same drive letter when the user logs back on to the system in
a later session.
3. What can Cassie do to provide printer access to every computer in every shop?
b. Locate the printer with the most central computer and share that printer with all the other
computers.
Essential details
Files and folders (directories) can be made accessible to other users over a network by sharing.
The permission settings determine the type of access that a particular user has to a resource (file, folder,
or share). Permissions are assigned via the resources property sheet. Permissions are granted by the system
administrator, owner of the resource, or other authorized person.
FAST TRACK HELP
http://windows.microsoft.com/en-us/windows7/File-sharing-essentials
http://windows.microsoft.com/en-US/windows7/Share-files-with-someone
FAST TRACK HELP
ee
_______ /3
Understand encr ypti on 189
OBJECTIVE MANAGI NG FI LES AND FOLDERS 4. 3
Understand encryption
SCENARIO: Woodgrove Bank is a small community bank with ve branch ofces. Their loan ofcers rotate to each
branch as needed. They each have laptops running Windows 7 Professional and also have external mobile drives
for data storage and backups. Due to the sensitive nature of banking, it is of high importance to Woodgrove
Bank to ensure that their customers information is secure. Woodgrove Bank has hired Jeff Price, a security
consultant, to perform a security audit and submit his ndings and recommendations to the board of directors.
This information is vital because the bank will be undergoing a security audit from their governing regulatory
agency.
1. Jeffs initial recommendation is to have the laptops secured with BitLocker. What must be done
first to make this change?
a. Purchase BitLocker because Woodgrove Bank does not have licensing for it.
b. Upgrade the laptops to Windows 7 Enterprise or Ultimate edition because BitLocker is not available with
Windows 7 Professional.
c. The bank doesnt have to do anything; it is ready.
2. What recommendation can Jeff make for securing the removable storage drives?
a. Secure the drives with Encrypting File System (EFS).
b. Secure the drives with BitLocker To Go.
c. Make sure that the drives are locked to the desks when they arrive.
3. What hardware must the laptops have to provide better security through
BitLocker?
a. Security locks on the outside of the laptops, so the loan officers can secure the
machine physically.
b. Trusted Platform Module (TPM) can be used in addition to BitLocker.
c. Smart card readers for authentication.
TPM is a hardware
feature on most new
computers that
can be used in
conjunction with
BitLocker technology.
190 CHAPTER 4: Managing Fil es and Fol ders
Answers
1. Jeffs initial recommendation is to have the laptops secured with BitLocker. What must be done first to make
this change?
b. Upgrade their laptops to Windows 7 Enterprise or Ultimate edition because BitLocker is not
available with Windows 7 Professional.
2. What recommendation can Jeff make for securing the removable storage drives?
b. Secure the drives with BitLocker To Go. Bitlocker To Go secures the entire drive. EFS is primarily used
for securing file systems.
3. What hardware must the laptops have to provide better security through BitLocker?
b. Trusted Platform Module (TPM) can be used in addition to BitLocker.
Essential details
Cryptography is the science of providing security for information. It has been used historically as a means
of providing secure communication between individuals, government agencies, and military forces. Today,
cryptography is a cornerstone of the modern security technologies used to protect information and resources
on both open and closed networks.
Encryption is the process of coding plaintext to create ciphertext.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc700811.aspx
http://technet.microsoft.com/en-us/library/cc732774.aspx
FAST TRACK HELP
_______ /3
Understand librari es 191
OBJECTIVE MANAGING FILES AND FOLDERS 4.4
Understand libraries
SCENARIO: Christian Hess is the desktop administrator for Coho Vineyard. Coho has just purchased
10 computers and 2 laptops congured with Windows 7 Professional that will be networked together.
The 2 laptops are for traveling sales representatives.
They need to have access to their les when they are not connected to the company network. In the past, they have
had problems maintaining the most recent version of documents because they used the process of copying from
the network, making changes, and then later trying to remember to copy the modied les back to the network.
They need a more reliable way to maintain the latest versions. They also would like to organize network les more
easily into a single repository of different types of les rather than continuing to map to different drives.
1. What can Christian do to solve the sales representatives problems?
a. Configure each laptop to use Offline Folders and mark their network shares to Always Be Available Offline.
b. Require that documents have to be checked out and limit modifications.
c. Have employees email documents to their inboxes so that they are available outside the network.
2. How can Christian use the features of Windows 7 to organize the winerys
files better?
a. Create folders labeled for each file type.
b. Configure libraries to be the central repositories for multiple network locations.
c. Set up each computer to maintain a specific file type and require the users to
rotate workstations.
3. How can the sales representatives synchronize their documents when
they return from a trip?
a. If the files are not configured to synchronize automatically, they can use the
Sync Center to synchronize files.
b. They can compare their files with the network files and merge the changes manually.
c. They can assume the corporate office is too busy with wine tastings to make any changes and just
dump their files back to the network.
An iteration, in
this context, is one trip
through the loop.
.
nges and just ges
An iteration, in ti
this context, is one trip ex
through the loop. h
A library can
contain les
from several
locations, both
local and
network.
192 CHAPTER 4: Managing Fil es and Fol ders
Answers
1. What can Christian do to solve the sales representatives problems?
a. Configure each laptop to use Offline Folders and mark their network shares to Always Be
Available Offline. Offline Folders can be configured through the Sync Center.
2. How can Christian use the features of Windows 7 to organize the winerys files better?
b. Configure libraries to be the central repositories for multiple network locations. Libraries can
be configured to be optimized for different file types. Network locations must be indexed to be made
available in the library.
3. How can the sales representatives synchronize their documents when they return from a trip?
a. If the files are not configured to synchronize automatically, they can use the Sync Center to
synchronize files.
Essential details
A cache is a special memory subsystem in which frequently used data values are duplicated for quick access.
A memory cache stores the contents of frequently accessed RAM locations and the addresses where these
data items are stored.
A library is a collection of items, such as files and folders that are assembled from various locations.
The locations might be on your computer, an external hard drive, or someone elses
computer.
Synchronization is a procedure that compares and processes file versions to
ensure that they contain the same data.
FAST TRACK HELP
http://technet.microsoft.com/en-us/windows/ee431715.aspx
http://technet.microsoft.com/en-us/library/ee449406(WS.10).aspx
http://windows.microsoft.com/en-US/windows7/Understanding-
offline-files
http://technet.microsoft.com/en-us/library/dd637828(WS.10).aspx
http://technet.microsoft.com/en-us/library/ff633429(WS.10).aspx
FAST TRACK HELP
_______ /3
5
Managing Devices
IN THI S CHAPTER
5.1/5.2 Connect devices; Understand storage
5.3 Understand printing devices
5.4 Understand system devices
Connect devi ces; Understand storage 195
OBJECTIVE MANAGI NG DEVI CES 5. 1/5. 2
Connect devices; Understand storage
SCENARIO: Kim Abercrombie is a systems consultant for Litware, Inc. One of her major contracts is with the
School of Fine Art. Her responsibilities at the school include adding new peripherals to computers and managing
the data and le storage needs. The School of Fine Art has only ve computers and just upgraded to Windows
7 Professional. Recently, while Kim was in the school setting up a printer, she was asked for her ideas about
providing adequate storage for the schools data and les. Lori Penor, the director of the school, explained to Kim
that the staff wants to be able to access their documents while at home, as well as when they are in the ofce.
She was adamant that they do not want to transport les back and forth by using an external drive.
1. What can Kim recommend to satisfy the school staffs storage needs so that they can access the
data while at home as well as at the school?
a. Store documents using cloud technology.
b. Train each employee to email files to their inboxes.
c. Purchase a laptop to be shared among the employees that stores all the files.
2. Kim wants everyone to have access to the printer. How can she accomplish this?
a. Attach the printer locally using a USB connection to one of the computers
and share it.
b. Create a system where employees sign up for a specific time to use the printer.
c. Place the printer on a movable cart and teach the employees how to connect the
printer to their computers.
3. After successfully attaching the printer, what can she use to manage the
new device?
a. Device Manager
b. Devices and Printers
c. Windows Registry
Printers can be
attached locally,
directly to the
network, or by
wireless
connection.
Answers
1. What can Kim recommend to satisfy the school staffs storage needs so that they can access the data while
at home as well as at the school?
a. Store documents using cloud technology. Microsoft SkyDrive or Live Mesh can be used as a solution
for small businesses to store their important documents. This also provides a form of business continuity
because the documents are stored offsite.
2. Kim wants everyone to have access to the printer. How can she accomplish this?
a. Attach the printer locally using a USB connection to one of the computers and share it. If the
printer has network features, she could also attach it to the network and each user would have
access to it.
3. After successfully attaching the printer, what can she use to manage the new device?
b. Devices and Printers.
Essential details
Plug and Play technology provides a combination of software and hardware support that enables Windows
to detect and configure hardware with little or no user involvement. Plug and Play makes it easier to add
and configure hardware on a computer running Windows without special user knowledge of hardware
configurations.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc736617(WS.10).aspx
http://windows.microsoft.com/en-us/windows7/Install-a-printer
http://explore.live.com/windows-live-mesh?os=other
http://explore.live.com/windows-live-skydrive
FAST TRACK HELP
196 CHAPTER 5: Managing Devi ces
_______ /3
Understand printing devi ces 197
OBJECTIVE MANAGI NG DEVI CES 5. 3
Understand printing devices
SCENARIO: Ben Smith is a network associate with Graphic Design Institute (GDI). GDI has purchased several color
laser printers for the classrooms and has asked Ben to set up and congure these print devices to meet a variety
of particular needs. GDI would like all the printers set to print the students graphic designs to landscape
orientation by default. All the printers are network-capable; however, GDIs policy is for the classrooms not to be
managed by print servers. Each classroom is separate from the Active Directory Domain Services network. GDI
wants these printers available for all computers within the classroom and does not want to have to depend upon
one computer operating to share the printer.
1. How can Ben make these printers available without sharing them from another system?
a. Attach a long USB cable to each computer that can be switched out whenever a student needs to print
from his or her computer.
b. Add the printer to each computer as a local printer but use the TCP/IP address for the printer port.
c. Attach the printer to one computer. Instruct students to save their print jobs to a USB flash drive and
take turns using the printing computer.
2. How can Ben set the print jobs to landscape orientation so that students do not need to select
Landscape for each print job?
a. Navigate to the printing preferences for each computer and set the finishing
to Landscape.
b. He cant, so he must train each student to select Landscape when they print.
c. Load the paper sideways for the document to be printed in landscape orientation.
3. Ben has installed and configured all the new printers for GDI successfully. He has
received a few emails from an instructor complaining that her print jobs are not
printing. She has tried more than 20 times to print and can see all 20 print jobs
in the print queue. What can Ben do to resolve this issue?
a. Nothing; when the employee restarts the computer the next day the issue will probably
resolve itself.
b. Lead the instructor through restarting the Print Spooler service, which will reset her local printers and
clear all the print jobs.
c. Call in his supervisor to help solve the issue.
y
The Print Spooler
service manages
all print jobs and
print queues.
Answers
1. How can Ben make these printers available without sharing them from another system?
b. Add the printer to each computer as a local printer but use the TCP/IP address for the printer
port. Network-attached printers can be added as local printers by using a Transmission Control
Protocol/Internet Protocol (TCP/IP) port. This treats the printer as a locally attached printer that is not
managed by a print server.
2. How can Ben set the print jobs to landscape orientation so that students do not need to select Landscape
for each print job?
a. Navigate to the printing preferences for each computer and set the finishing to Landscape.
Setting printing preferences configures the default behavior for printers. Preferences such as
orientation, finishing, or paper tray can be configured.
3. Ben has installed and configured all the new printers for GDI successfully. He has received a few emails from
an instructor complaining that her print jobs are not printing. She has tried more than 20 times to print and
can see all 20 print jobs in the print queue. What can Ben do to resolve this issue?
b. Lead the instructor through restarting the Print Spooler service, which will reset her local
printers and clear all the print jobs. Restarting the Print Spooler service is the most common solution
to printers not responding or print jobs being stuck in the print queue. When the Print Spooler service is
restarted, all jobs must be resubmitted.
Essential details
A print queue is a representation of a printing device in Windows. Opening a print
queue displays active print jobs and their status.
A print spooler is software that intercepts a print job on its way to the printer and
sends it to disk or memory instead, where the print job is held until the printer
is ready for it.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/dd393190(WS.10).aspx
http://windows.microsoft.com/en-us/windows7/Install-a-printer
FAST TRACK HELP
198 CHAPTER 5: Managing Devi ces
nt t
dd
_______ /3
Understand system devi ces 199
OBJECTIVE MANAGI NG DEVI CES 5. 4
Understand system devices
SCENARIO: Wingtip Toys has hired Miles Reid, an independent business technology consultant, to help them with
their desktop upgrades to Windows 7 Professional. Miles has done some research and asked the right questions
regarding their existing peripheral devices. Charlie Herb, the manager for this project, has indicated that there
are several input devices that the company would like to use on the new computers, but he is unsure if they are
compatible. Wingtip Toys also would like to know if some of the internal devices from the old computers might
work on the new computers. The company has already purchased one computer to test some devices, and they
have run into some issues after they updated drivers on a couple of the peripherals.
1. How can Miles determine if the existing devices at Wingtip Toys will work on the new computers
running Windows 7 Professional?
a. Test each device on the new testing computer and mark the items as compatible or not compatible.
b. Assume that all devices will work and plow forward with the upgrades.
c. Check with Windows 7 Compatibility Center to determine compatibility. He can then provide Wingtip
Toys with a list of similar devices that are compatible to replace those that are not.
2. What can be done about devices that are no longer working after the device drivers were updated?
a. Throw the devices away because they dont work.
b. Keep the old computers so they can use the old devices.
c. Because the devices worked prior to the driver update, use Device Manager and
choose Roll Back Driver to return to the previous version.
3. Miles has determined that a few devices that arent listed as compatible work
on the new workstations running Windows 7. What should he do?
a. Miles shouldnt say a word. They work and thats enough.
b. Suggest to Charlie that they should consider upgrading the devices because even
though they work, they are not supported under the new operating system.
c. Keep the devices as backups and purchase new devices.
Devices listed as
not compatible may
cause problems when
new updates are
released or other
devices are configured.
Answers
1. How can Miles determine if the existing devices at Wingtip Toys will work on the new computers running
Windows 7 Professional?
c. Check with Window 7 Compatibility Center to determine compatibility. He can then provide
Wingtip Toys with a list of similar devices that are compatible to replace those that are not.
Windows 7 Compatibility Center maintains an updated list of devices and software that are compatible
and not compatible and it also features news of upcoming updates.
2. What can be done about devices that are no longer working after the device drivers were updated?
c. Because the devices worked prior to the driver update, use Device Manager and choose Roll
Back Driver to return to the previous version. Updating drivers can sometimes cause problems. If
the device worked prior to the update, then choosing Rollback driver is an acceptable solution.
3. Miles has determined that a few devices that arent listed as compatible work on the new workstations
running Windows 7. What should he do?
b. Suggest to Charlie that they should consider upgrading the devices because even though they
work, they are not supported under the new operating system.
Essential details
A device is any piece of equipment that can be attached to a network or computer, such as a
printer, joystick, adapter, modem card, or any other peripheral equipment. A device
requires a device driver to function with Windows.
A device driver is a component used to provide I/O services for adevice such as a
modem or network adapter. Rather than access the device directly, Windows loads
device drivers and calls functions in the drivers to carry out actions on the device.
If you disable a device in a hardware configuration, it becomes nonfunctional. Disabling
a device frees the resources that were allocated to the device.
FAST TRACK HELP
http://technet.microsoft.com/en-us/library/cc776246(WS.10).aspx
http://technet.microsoft.com/en-us/windows/dd361745.aspx
http://www.microsoft.com/windows/compatibility/windows-7/en-us/default.aspx
FAST TRACK HELP
200 CHAPTER 5: Managing Devi ces
a a
ds
sabling g sablin
_______ /3
6
Understanding
Operating System
Maintenance
IN THI S CHAPTER
6.1 Understand backup and recovery methods
6.2/6.3 Understand maintenance tools; Understand updates
Understand backup and recover y methods 203
Understand backup and recovery methods
SCENARIO: Walter Harp is a business consultant and assists Coho Winery with maintaining their small network
of Window 7 Professional PCs. The company also has a pair of laptops that are running Windows 7. Walter has
set up their system so that all their data resides on one computer. Walter is concerned that Coho employees
will forget to back up their data regularly, and he needs to come up with a solution to prevent a major loss. He
also has concerns with the laptops that are used by two traveling salespeople. There are times when the laptops
perform updates that can cause some issues with their custom winery software as well.
1. What solution can Walter use to resolve the update issues with the laptops?
a. Configure the laptops to shut down at the end of the normal workday.
b. Create restore points so that when a laptop returns, he can restore the system to the point prior to the
updates that affected the software.
c. Disable the wireless cards on the laptops.
2. One laptop stops and freezes immediately after the salesperson logs in. Walter suspects a bad
driver or perhaps malware. What can he do to diagnose the problem?
a. Press F8 to enter the Advanced Boot Options menu and boot in to safe mode.
b. Plug the laptop into the network and attempt to log on as Administrator.
c. Restore a system image to the drive.
3. What can Walter do to make sure that system backups run regularly?
a. Schedule an employee to run the backup every day at 5:30 PM.
b. Configure Backup and Restore to perform an automated backup daily after
business hours.
c. Arrive at the office early each day and perform the backups himself.
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM MAI NTENANCE 6. 1
Safe mode loads
basic les and
drivers necessary
to load the Windows
operating system.
204 CHAPTER 6: Understandi ng Operati ng System Mai ntenance
Answers
1. What solution can Walter use to resolve the update issues with the laptops?
b. Create restore points so that when a laptop returns, he can restore the system to the point prior
to the updates that affected the software. Restore points restore the registry and system settings
from a previous point in time. It does not affect personal files, but it may uninstall software or drivers.
2. One laptop stops and freezes after the salesperson logs in. Walter suspects a bad driver or perhaps malware.
What can he do to begin diagnosing the problem?
a. Press F8 to enter the Advanced Boot Options menu and boot in to safe mode. Safe mode loads
basic files and drivers. If Walter suspects malware, he should not connect it to the network with the
other computers.
3. What can Walter do to make sure that the systems backups are running regularly?
b. Configure Backup and Restore to perform an automated backup daily after business hours.
Essential details
Safe mode is a troubleshooting option for Windows that starts the computer in a limited state. Only the
basic files and drivers necessary to run Windows are started.
A system image is an exact copy of a drive. By default, a system image includes the drives required for
Windows to run. It also includes Windows and your system settings, programs, and files.
FAST TRACK HELP
http://windows.microsoft.com/en-US/windows7/
Back-up-and-restore-frequently-asked-questions
http://windows.microsoft.com/en-US/windows7/help/system-repair-recovery
http://windows.microsoft.com/en-US/windows7/what-is-safe-mode
http://windows.microsoft.com/en-US/windows7/
Advanced-startup-options-including-safe-mode
FAST TRACK HELP
ery ery
_______ /3
Understand maintenance tools; Understand updates 205
Understand maintenance tools; Understand updates
SCENARIO: Jeff Hay is a desktop administrator with Blue Yonder Airlines. His job is maintaining the desktop
computers in the airport terminal to ensure that they remain secure and run efciently. The computers at the
ticket counters are running Windows 7 Professional and Jeff has had a difcult time maintaining a high level of
performance on some of them. He examined the computers and identied several things he can do to increase
performance. Jeff also knows that Windows Updates are not being installed on a timely basis and has had to
occasionally run updates during his lunch break.
1. Jeff has discovered that the computers have many unneeded temporary files. What can he do to be
sure temporary files are removed on a regular basis?
a. Teach the counter staff to search for files and delete those they think are unnecessary.
b. Create a task in Task Scheduler and run Disk Cleanup monthly.
c. Re-install the operating systems every month to keep them clean.
2. Jeff knows that using Disk Defragmenter is a great way to keep the computers running smoothly.
Should he configure another task in Task Scheduler to defragment the computers automatically?
a. No, Windows 7 defragments the hard drives automatically on a regular schedule.
b. Yes, defragmenting on a regular basis optimizes the operating system.
c. No, defragmenting is a waste of time.
3. How can Jeff manage updates so that he can enjoy his lunch breaks again?
a. Schedule the updates to be downloaded and installed automatically.
b. Train the counter staff to run the updates.
c. Nothing, he has lost 20 pounds in the last six months by skipping lunch.
OBJECTIVE UNDERSTANDI NG OPERATI NG SYSTEM MAI NTENANCE 6. 2/6. 3
Task Scheduler can
start Disk Cleanup,
however specic
drives and les
must be selected
before it can execute.
206 CHAPTER 6: Understandi ng Operati ng System Mai ntenance
Answers
1. Jeff has discovered that the computers have many unneeded temporary files. What can he do to be sure
temporary files are removed on a regular basis?
b. Create a task in Task Scheduler and run Disk Cleanup monthly. Running Disk Cleanup in
conjunction with Disk Defragmenter is an inexpensive way to maintain and optimize the Windows 7
operating system.
2. Jeff knows that using Disk Defragmenter is a great way to keep the computers running smoothly. Should he
configure another task in Task Scheduler to defragment the computers automatically?
a. No, Windows 7 defragments the hard drives automatically on a regular schedule.
3. How can Jeff manage updates so that he can enjoy his lunch breaks again?
a. Schedule the updates to be downloaded and installed automatically.
Essential details
Windows updates include additions to software that can help prevent or fix problems, improve how your
computer works, and enhance your computing experience.
Fragmentation occurs as files on a disk are deleted and new files are added. It slows disk access and
degrades the overall performance of disk operations.
A service pack is a collection updates since the release of the product, including many
resolved problems that have not been made available through any other software
updates and may contain customer-requested design changes or features.
FAST TRACK HELP
http://windows.microsoft.com/en-US/windows7/
Improve-performance-by-defragmenting-your-hard-disk
http://windows.microsoft.com/en-us/windows7/
Delete-files-using-Disk-Cleanup
http://windows.microsoft.com/en-US/windows7/Schedule-Disk-Cleanup
-to-run-regularly
http://technet.microsoft.com/en-us/library/cc700845.aspx
http://windows.microsoft.com/en-US/windows7/products/features/windows-update
FAST TRACK HELP
e
_______ /3
You might also like
- Optimizing and Testing WLANs: Proven Techniques for Maximum PerformanceFrom EverandOptimizing and Testing WLANs: Proven Techniques for Maximum PerformanceNo ratings yet
- MTA 98-368 Mobile Fundamentals - Study GuideDocument89 pagesMTA 98-368 Mobile Fundamentals - Study GuideTom100% (1)
- Chapter 6 NotesDocument7 pagesChapter 6 NotesTrevorNo ratings yet
- Windows Server 2008 Administrator 70-646Document532 pagesWindows Server 2008 Administrator 70-646scottysockoNo ratings yet
- Cisco Ccna Icnd PPT D20S05L05Document19 pagesCisco Ccna Icnd PPT D20S05L05AMIT RAJ KAUSHIKNo ratings yet
- The CBT Nuggets Training Guide To The Ccna R/S: 100-101 ICND1 OverviewDocument3 pagesThe CBT Nuggets Training Guide To The Ccna R/S: 100-101 ICND1 Overviewrose25_4u6010No ratings yet
- Alcatel-Lucent Network Routing Specialist I: Key Learning Outcomes Certification ObjectivesDocument2 pagesAlcatel-Lucent Network Routing Specialist I: Key Learning Outcomes Certification Objectivesadityabp100% (1)
- Biomass PDFDocument59 pagesBiomass PDFVignesh KumaranNo ratings yet
- Optical Fiber: By: V Jaithra Reddy PVG Madan Gopal B Srikanth ReddyDocument12 pagesOptical Fiber: By: V Jaithra Reddy PVG Madan Gopal B Srikanth Reddymadan gopalNo ratings yet
- Jones NCTI Training KitDocument129 pagesJones NCTI Training Kitjonesncti0% (1)
- Basic Linux ArchitectureDocument11 pagesBasic Linux ArchitectureJyothy LakshuNo ratings yet
- Port# TCP or UDP Port Name DescriptionDocument1 pagePort# TCP or UDP Port Name DescriptionMalluNo ratings yet
- Fiber Optics CableDocument64 pagesFiber Optics CableakramsayeedNo ratings yet
- CCNA Dumbs Part 1Document90 pagesCCNA Dumbs Part 1Vijay AnandNo ratings yet
- Comptia Linux+ Certification Exam ObjectivesDocument16 pagesComptia Linux+ Certification Exam ObjectivesJose A. Brito H.No ratings yet
- CDVI Centaur 5 1 DVR VisitorDocument39 pagesCDVI Centaur 5 1 DVR VisitorMarco Antonio RubinaNo ratings yet
- Ethernet Protocol Basics PDFDocument2 pagesEthernet Protocol Basics PDFPamelaNo ratings yet
- Traffic Control Training CourseDocument142 pagesTraffic Control Training CourseAbu FadilahNo ratings yet
- Cisco AnswerDocument28 pagesCisco AnswerSergiu SergiuNo ratings yet
- Computer NetworksDocument112 pagesComputer NetworksBalamurugan ChinnaiyanNo ratings yet
- 98-366 MVA Slides Lesson 3Document32 pages98-366 MVA Slides Lesson 3cviga100% (1)
- BoschVMS Configuration Manual EnUS 20710700043Document390 pagesBoschVMS Configuration Manual EnUS 20710700043xyzNo ratings yet
- CCNA Security Chapter 2 PowerpointDocument14 pagesCCNA Security Chapter 2 PowerpointEric NapholzNo ratings yet
- Embedded Operating Systems and Linux: Presented by Aaruni Giriraj Viiith Sem I.TDocument24 pagesEmbedded Operating Systems and Linux: Presented by Aaruni Giriraj Viiith Sem I.TAaruni GirirajNo ratings yet
- CompTIA Testkings N10-006 v2016-08-11 by Jabulani 258qDocument171 pagesCompTIA Testkings N10-006 v2016-08-11 by Jabulani 258qIrvin RamosNo ratings yet
- 98-366 MVA Slides Lesson 4Document31 pages98-366 MVA Slides Lesson 4cvigaNo ratings yet
- Exam: PW0-205 Titl E: Wireless LAN AnalysisDocument58 pagesExam: PW0-205 Titl E: Wireless LAN AnalysisnobuyukiNo ratings yet
- A New Streamlined Certification ProgramDocument18 pagesA New Streamlined Certification Programgladys medinaNo ratings yet
- CCNA Answers - CCNA Exam - CCNA ExamsDocument30 pagesCCNA Answers - CCNA Exam - CCNA ExamsMihai Gheorghe100% (1)
- BSCI Lab 10Document8 pagesBSCI Lab 10Theng OuchNo ratings yet
- 98-366 MVA Slides Lesson 5Document19 pages98-366 MVA Slides Lesson 5cvigaNo ratings yet
- 98-366 MVA Slides Lesson 2Document29 pages98-366 MVA Slides Lesson 2cvigaNo ratings yet
- 40 Cara Membuat Data CenterDocument10 pages40 Cara Membuat Data CenterAdri AntoNo ratings yet
- How To Troubleshoot Network Adapter Problems in WindowsDocument41 pagesHow To Troubleshoot Network Adapter Problems in WindowsShivakumar S KadakalNo ratings yet
- Express e User GuideDocument141 pagesExpress e User GuideSergio100% (1)
- CCNA 1 Exploration ENetwork Final Exam Form3 V 4.0Document22 pagesCCNA 1 Exploration ENetwork Final Exam Form3 V 4.0sEcZxNo ratings yet
- Security Mini Course HandbookDocument26 pagesSecurity Mini Course Handbookstr8drop904No ratings yet
- Mikrotik Data Center MUM 2014 KevinMyers 4 by 3Document31 pagesMikrotik Data Center MUM 2014 KevinMyers 4 by 3Maryudi Uchiha Mundane Person0% (1)
- CCNA1 IG v31 101705Document202 pagesCCNA1 IG v31 101705Hoody ChanNo ratings yet
- EBIT Miner Network OperationDocument9 pagesEBIT Miner Network OperationLuis AcostaNo ratings yet
- Certified Data Analyst Course in Collaboration With IBMDocument30 pagesCertified Data Analyst Course in Collaboration With IBMLakshita SharmaNo ratings yet
- 48TMSS06R1 Medium Density Fiber Optic SystemDocument55 pages48TMSS06R1 Medium Density Fiber Optic SystemMohamed NasrNo ratings yet
- Ccna 2 Module 2 v4.0Document10 pagesCcna 2 Module 2 v4.0ccnaexploration4100% (1)
- Domain 8 - Software Development SecurityDocument19 pagesDomain 8 - Software Development SecurityRasika Sampath AprNo ratings yet
- Ccna RS 200-125 417QDocument195 pagesCcna RS 200-125 417QFiqri Ibnu AzizNo ratings yet
- Modul Praktek - Beginning With Kali LinuxDocument27 pagesModul Praktek - Beginning With Kali LinuxDandy PermanaNo ratings yet
- Study Plan Microsoft MCSA Windows Server 2016-70-741Document14 pagesStudy Plan Microsoft MCSA Windows Server 2016-70-741Chow Moow100% (1)
- Thesis - 1051 - Opnet Simulation of Voice Over Mpls With Considering TeDocument44 pagesThesis - 1051 - Opnet Simulation of Voice Over Mpls With Considering TeYns AricheNo ratings yet
- CCNA Answers Chapter 1Document14 pagesCCNA Answers Chapter 1Brandon ScottNo ratings yet
- Manual CactiDocument98 pagesManual CactimonsherNo ratings yet
- Just A Glance: Cwna CwapDocument3 pagesJust A Glance: Cwna CwapRajavel Selvakumar0% (1)
- Archer AX55 Pro (EU&US) 1.0 - DatasheetDocument8 pagesArcher AX55 Pro (EU&US) 1.0 - DatasheetAhmet AteşNo ratings yet
- Windows Deployment Services A Complete Guide - 2020 EditionFrom EverandWindows Deployment Services A Complete Guide - 2020 EditionNo ratings yet
- MTADocument167 pagesMTAALDAIRNo ratings yet
- MTA SSG Developer Without CropDocument227 pagesMTA SSG Developer Without Cropbhuvii2132No ratings yet
- 98-349-Windows OS Fundamentals - Study-Guide PDFDocument65 pages98-349-Windows OS Fundamentals - Study-Guide PDFHudson Gonçalves SiqueiraNo ratings yet
- Mta 98 367 Study GuideDocument5 pagesMta 98 367 Study Guidechulla100% (1)
- 98349Document65 pages98349Jay Jay CribNo ratings yet
- Interface of Pandapos CounterDocument63 pagesInterface of Pandapos CountersnadminNo ratings yet
- Work Instruction Bill of Material 2013Document5 pagesWork Instruction Bill of Material 2013snadminNo ratings yet
- Po and Goods Received Policy (Pay by Invoice Format)Document3 pagesPo and Goods Received Policy (Pay by Invoice Format)snadminNo ratings yet
- Branch Price ChangeDocument4 pagesBranch Price Changesnadmin100% (1)
- Panda Manual Guide - Setup Payment Term 2014Document2 pagesPanda Manual Guide - Setup Payment Term 2014snadminNo ratings yet
- Good Return Debit NoteDocument3 pagesGood Return Debit NotesnadminNo ratings yet
- 200 + SQL - Server - Interview - Questions - by Shivprasad KoiralaDocument311 pages200 + SQL - Server - Interview - Questions - by Shivprasad Koiralavaraprasad11987% (39)
- PANDA Mobile Received Module New VersionDocument14 pagesPANDA Mobile Received Module New Versionsnadmin100% (1)
- Penguin - Test Your Vocabulary 5 PDFDocument58 pagesPenguin - Test Your Vocabulary 5 PDFGabriela DiazNo ratings yet
- Penguin - Test Your Vocabulary 2Document64 pagesPenguin - Test Your Vocabulary 2Magazinul de Pantofi100% (1)
- Penguin Test Your Vocabulary 3 PDFDocument65 pagesPenguin Test Your Vocabulary 3 PDFLauren HeadNo ratings yet
- Active Directory Domain Services - All - Dsadd - Parameters PDFDocument3 pagesActive Directory Domain Services - All - Dsadd - Parameters PDFsnadminNo ratings yet
- CS50 Cheat Sheet - NotesDocument9 pagesCS50 Cheat Sheet - NotessnadminNo ratings yet
- VIM Editor Commands: (Ex. 10G Goes To Line 10)Document4 pagesVIM Editor Commands: (Ex. 10G Goes To Line 10)snadminNo ratings yet
- CS50 Appliance 2014Document12 pagesCS50 Appliance 2014snadminNo ratings yet
- Binary Two's ComplementDocument3 pagesBinary Two's ComplementsnadminNo ratings yet
- Windows 7 Reference Guide PDFDocument39 pagesWindows 7 Reference Guide PDFsnadminNo ratings yet
- Mohit DL01Document2 pagesMohit DL01Ripunjay MishraNo ratings yet
- Troubleshooting Terminal Server Licensing IssuesDocument13 pagesTroubleshooting Terminal Server Licensing IssuesphcastelhanoNo ratings yet
- Computer System Servicing Assessment OutlineDocument3 pagesComputer System Servicing Assessment Outlinedatabasetechnology collegeNo ratings yet
- MS-windows-TS-DC With CiscoDocument68 pagesMS-windows-TS-DC With CiscoPhilippe AndreNo ratings yet
- Dimetra PDFDocument51 pagesDimetra PDFSohaib Omer SalihNo ratings yet
- Creating An Optimized Windows Image For A Vmware Horizon Virtual Desktop Noindex PDFDocument86 pagesCreating An Optimized Windows Image For A Vmware Horizon Virtual Desktop Noindex PDFVicky mheNo ratings yet
- AWS Step-by-Step+Instructions+-+Windows+WorkloadsDocument20 pagesAWS Step-by-Step+Instructions+-+Windows+WorkloadscatchnskNo ratings yet
- Analisis WEBDocument88 pagesAnalisis WEBNelson TorresNo ratings yet
- Module 3-FinalDocument19 pagesModule 3-FinalcamotilloNo ratings yet
- Course WS 011T00 A Windows Server 2019 AdministrationDocument10 pagesCourse WS 011T00 A Windows Server 2019 AdministrationdikeyNo ratings yet
- Virtualization Technology (At Desktop and Application)Document26 pagesVirtualization Technology (At Desktop and Application)rajput0302No ratings yet
- CIMPLICITY Secure Deployment Guide 24 08Document100 pagesCIMPLICITY Secure Deployment Guide 24 08mamobi7467No ratings yet
- Terminal Services and CitrixDocument6 pagesTerminal Services and CitrixDOUDOU-38No ratings yet
- 20745B ENU CompanionDocument199 pages20745B ENU CompanionMarculino LimaNo ratings yet
- ThinManual 11Document63 pagesThinManual 11Juan Esteban Benjumea BenjumeaNo ratings yet
- OnGuard 2008 Plus 6.1 Release NotesDocument26 pagesOnGuard 2008 Plus 6.1 Release NotesYomindo de CastroNo ratings yet
- Legit Remote Admin ToolsDocument33 pagesLegit Remote Admin ToolsIceCream Brainz100% (1)
- Lexmark E-Guide 2011 MajDocument302 pagesLexmark E-Guide 2011 MajIvana SmoljanNo ratings yet
- RTFM Red Team Field ManualDocument103 pagesRTFM Red Team Field ManualGarv SanwariyaNo ratings yet
- BlueDiamond-BPV-UserGuide-v3.0 2023 02 08Document44 pagesBlueDiamond-BPV-UserGuide-v3.0 2023 02 08Anubhav SwainNo ratings yet
- Nmap CommandsDocument8 pagesNmap CommandsginggersNo ratings yet
- Sage 500 Erp Compatibility Guide 2017Document42 pagesSage 500 Erp Compatibility Guide 2017Ariel SpallettiNo ratings yet
- VDI Deployment F4HB312823 PDFDocument51 pagesVDI Deployment F4HB312823 PDFLuis Barreto100% (1)
- Tm1 Deployment Options and Bandwidth ConsiderationsDocument10 pagesTm1 Deployment Options and Bandwidth ConsiderationsFFARALNo ratings yet
- Accpac - Guide - Installation PDFDocument122 pagesAccpac - Guide - Installation PDFcaplusincNo ratings yet
- Black Vipers Windows 10 Service Configurations Black ViperDocument42 pagesBlack Vipers Windows 10 Service Configurations Black Viperzta03No ratings yet
- Apd4 ReadmeusDocument12 pagesApd4 ReadmeusIvan Rivera CastroNo ratings yet
- How To Use Remote DesktopDocument4 pagesHow To Use Remote DesktopMANOLO C. LUCENECIONo ratings yet
- Allegro Platform System RequirementsDocument21 pagesAllegro Platform System RequirementsKarla RuizNo ratings yet
- FactoryTalk VantagePoint v3.1 Design Considerations Rev3-1-5Document28 pagesFactoryTalk VantagePoint v3.1 Design Considerations Rev3-1-5Cristian Valderrama CamposNo ratings yet