Professional Documents
Culture Documents
Critical Log Review Checklist For Security Incidents PDF
Uploaded by
viny20100 ratings0% found this document useful (0 votes)
272 views1 pageOriginal Title
CRITICAL LOG REVIEW CHECKLIST FOR SECURITY INCIDENTS.pdf
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
272 views1 pageCritical Log Review Checklist For Security Incidents PDF
Uploaded by
viny2010Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 1
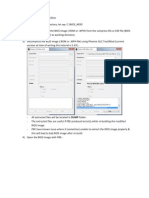
CRITICAL LOG REVIEW CHECKLIST FOR SECURITY INCIDENTS
This cheat sheet presents a checklist for reviewing critical logs when responding to a security incident. It can also be used for routine log review.
G E N E R AL APPROACH WHAT TO LOOK FOR ON NET WOR K DE V I C ES
1. Identify which log sources and automated tools you can use during Look at both inbound and outbound activities.
the analysis.
Examples below show log excerpts from Cisco ASA logs; other
2. Copy log records to a single location where you will be able to devices have similar functionality.
review them.
Traffic allowed on firewall Built connection,
3. Minimize noise by removing routine, repetitive log entries from access-list permitted
view after confirming that they are benign.
Traffic blocked on firewall access-list denied, deny inbound;
4. Determine whether you can rely on logs time stamps; consider time Deny by
zone differences.
Bytes transferred (large files?) Teardown TCP connection
5. Focus on recent changes, failures, errors, status changes, access duration bytes
and administration events, and other events unusual for your
Bandwidth and protocol usage limit exceeded, CPU utilization
environment.
6. Go backwards in time from now to reconstruct actions after and Detected attack activity attack from
before the incident. User account changes user added, user deleted,
User priv level changed
7. Correlate activities across different logs to get a comprehensive
picture. Administrator access AAA user , User locked out,
login failed
8. Develop theories about what occurred; explore logs to confirm or
disprove them.
WHAT TO LOOK FOR ON WEB S E RV E RS
P OT E N T I A L S ECURIT Y LO G SOURCE S
Excessive access attempts to non-existent files
Server and workstation operating system logs
Code (SQL, HTML) seen as part of the URL
Application logs (e.g., web server, database server)
Security tool logs (e.g., anti-virus, change detection, intrusion Access to extensions you have not implemented
detection/prevention system) Web service stopped/started/failed messages
Outbound proxy logs and end-user application logs Access to risky pages that accept user input
Remember to consider other, non-log sources for security events.
Look at logs on all servers in the load balancer pool
T Y P I C A L LOG LOC ATION S Error code 200 on files that are not yours
Linux OS and core applications: /var/log Failed user authentication Error code 401, 403
Windows OS and core applications: Windows Event Log Invalid request Error code 400
(Security, System, Application) Internal server error Error code 500
Network devices: usually logged via Syslog; some use proprietary
locations and formats
OTHER RESOURCE S
W H AT TO LO OK FO R ON LI NU X Windows event ID lookup:
Successful user login Accepted password, Accepted publickey, www.eventid.net
session opened
A listing of many Windows Security Log events:
Failed user login authentication failure, failed password
ultimatewindowssecurity.com/.../Default.aspx
User log-off session closed
Log analysis references:
User account change password changed, new user, delete user www.loganalysis.org
or deletion
Sudo actions sudo: COMMAND= FAILED su A list of open-source log analysis tools:
securitywarriorconsulting.com/logtools
Service failure failed or failure
Anton Chuvakins log management blog:
securitywarriorconsulting.com/logmanagementblog
W H AT TO LO OK FOR ON WINDOWS
Other security incident response-related cheat sheets:
Event IDs are listed below for Windows 2000/XP. For Vista/7 security zeltser.com/cheat-sheets
event ID, add 4096 to the event ID.
Most of the events below are in the Security log;
many are only logged on the domain controller. Authored by Anton Chuvakin (chuvakin.org) and
User logon/logoff events Successful logon 528, 540; Lenny Zeltser (zeltser.com).
failed logon 529-537, 539; logoff 538, 551, etc
User account changes Created 624; enabled 626; Reviewed by Anand Sastry.
changed 642; disabled 629; deleted 630
Password changes To self: 628; to others: 627 Distributed according to the
Service started or stopped 7035, 7036, etc. Creative Commons v3 Attribution License.
Object access denied 560, 567, etc
(if auditing enabled) Cheat sheet version 1.0.
You might also like
- CRITICAL LOG REVIEW CHECKLISTDocument1 pageCRITICAL LOG REVIEW CHECKLISTAli BhamlaNo ratings yet
- Cyber Security Notes Unit 3Document8 pagesCyber Security Notes Unit 3Reshma BasuNo ratings yet
- Rank Software - Threat Hunting PlaybookDocument31 pagesRank Software - Threat Hunting PlaybookDrake von DuckNo ratings yet
- Next-Generation Endpoint Security, Evolved: Gravityzone Elite SuiteDocument4 pagesNext-Generation Endpoint Security, Evolved: Gravityzone Elite SuiteSachinNo ratings yet
- Network Security Testing - CoreDocument2 pagesNetwork Security Testing - Core7h3rAmNo ratings yet
- Continuous Security MonitoringDocument14 pagesContinuous Security Monitoringtavillo1980100% (1)
- Incident Response Playbook: Phishing Investigation (Part 1) : Stop / Remove The User / Identity Off The Potential ListDocument4 pagesIncident Response Playbook: Phishing Investigation (Part 1) : Stop / Remove The User / Identity Off The Potential Listfawas hamdiNo ratings yet
- Ec Council Certified Security Analyst Ecsa v8Document5 pagesEc Council Certified Security Analyst Ecsa v8fazli3036No ratings yet
- Network Security Note Chapter 1Document20 pagesNetwork Security Note Chapter 1Chong DaxiongNo ratings yet
- TI-SIEM Rule TuningDocument13 pagesTI-SIEM Rule TuningDark Storm WolfNo ratings yet
- Secure Web Engineer Course OverviewDocument4 pagesSecure Web Engineer Course OverviewZidane LanceNo ratings yet
- Symantec - 8 Key Requirements of An IT Governance, Risk and Compliance SolutionDocument10 pagesSymantec - 8 Key Requirements of An IT Governance, Risk and Compliance SolutionHarumNo ratings yet
- PR11 LogReviewProcedureDocument7 pagesPR11 LogReviewProcedureThakur Narsing SinghNo ratings yet
- Threat Protection - Windows 10Document3,502 pagesThreat Protection - Windows 10tetkaCNo ratings yet
- ATA PlaybookDocument40 pagesATA PlaybookAaronTNo ratings yet
- Innovatum DLP WPDocument9 pagesInnovatum DLP WPlittlepaoNo ratings yet
- CCFE Detailed Forensics ReportDocument13 pagesCCFE Detailed Forensics ReportHazel Nott100% (1)
- Cybersecurity Pro Seeks New ChallengeDocument1 pageCybersecurity Pro Seeks New ChallengeigrowrajeshNo ratings yet
- Cortex XDRDocument6 pagesCortex XDRStacy Marie100% (1)
- Ransomware Prevention RecommendationsDocument2 pagesRansomware Prevention RecommendationsmufeedNo ratings yet
- Defence and Security Capability StatementDocument4 pagesDefence and Security Capability StatementTata Steel ProjectsNo ratings yet
- Enterprise IT Security: The Ultimate GuideDocument44 pagesEnterprise IT Security: The Ultimate GuideVlad VikernesNo ratings yet
- Cyber Secure Pakistan 2019 ReportDocument23 pagesCyber Secure Pakistan 2019 ReportAbbas AnsariNo ratings yet
- Service Scope and OptionsDocument2 pagesService Scope and OptionsmeimNo ratings yet
- UNIX and Linux Security ChecklistDocument59 pagesUNIX and Linux Security ChecklistAsif MahbubNo ratings yet
- Database Security FeaturesDocument4 pagesDatabase Security FeaturesAbdul Rehman ButtsarkarNo ratings yet
- M.tech Cyber Security & Incident ResponseDocument11 pagesM.tech Cyber Security & Incident ResponseAbhishek DaveNo ratings yet
- Phishing Seminar Report FinalDocument25 pagesPhishing Seminar Report FinalPiyush Mantri100% (1)
- IT SecurityDocument12 pagesIT SecuritymadhwarajganguliNo ratings yet
- CRMF Cyber Risk FrameworkDocument9 pagesCRMF Cyber Risk Frameworkleo58800% (1)
- Interview PresentationDocument3 pagesInterview PresentationKenneth IserhienrhienNo ratings yet
- Best Practices Cyber Security TestingDocument4 pagesBest Practices Cyber Security Testingtheeffani100% (1)
- Cyber Boot Camp - Day 05 - Cyber Security FrameworkDocument3 pagesCyber Boot Camp - Day 05 - Cyber Security FrameworkAnna Margarita de VegaNo ratings yet
- Cyber Kill Chain (ADID Smail)Document26 pagesCyber Kill Chain (ADID Smail)Ismail AdidNo ratings yet
- CCNA Cyber Ops (Version 1.1) - Chapter 10 Exam Answers FullDocument13 pagesCCNA Cyber Ops (Version 1.1) - Chapter 10 Exam Answers FullSaber TunisienNo ratings yet
- What Is Cyber SecurityDocument56 pagesWhat Is Cyber SecurityHumayoun SaeedNo ratings yet
- Firewall Document AnalysisDocument9 pagesFirewall Document AnalysisTabish NomanNo ratings yet
- Cyber Security Controls ChecklistDocument12 pagesCyber Security Controls ChecklistpopsalldayNo ratings yet
- How To Become Certified in Risk and Information Systems Control Cert Prep Guide Global Knowledge Us enDocument8 pagesHow To Become Certified in Risk and Information Systems Control Cert Prep Guide Global Knowledge Us entakundaNo ratings yet
- How To Become A Security AnalystDocument3 pagesHow To Become A Security AnalystMerveil LubanjaNo ratings yet
- IPD - Malware ResponseDocument28 pagesIPD - Malware ResponseshuvoNo ratings yet
- Kinara's ResumeDocument1 pageKinara's ResumeRavey KinleyNo ratings yet
- Top Threats To Cloud ComputingDocument9 pagesTop Threats To Cloud ComputingVinny BamrahNo ratings yet
- Cybersecurity Basics: Small BusinessDocument24 pagesCybersecurity Basics: Small Businessyunus emre dursunNo ratings yet
- IBM Security Ransomware Client Engagement GuideDocument46 pagesIBM Security Ransomware Client Engagement GuideOmarNo ratings yet
- Cyber Threat and Kill Chain MethodologyDocument72 pagesCyber Threat and Kill Chain MethodologyJaveria ShakilNo ratings yet
- Mobile Security Risks: Who's ListeningDocument37 pagesMobile Security Risks: Who's ListeningvinodkunmarNo ratings yet
- Session 3.4 - Cyber Security RiskDocument48 pagesSession 3.4 - Cyber Security RiskhvanhtuanNo ratings yet
- Network Security, Report 01Document5 pagesNetwork Security, Report 01dara100% (1)
- Cyber Security!Document17 pagesCyber Security!Dua KamranNo ratings yet
- What Is A Security Audit?Document5 pagesWhat Is A Security Audit?Joe LagartejaNo ratings yet
- Guide to Procuring a Security Operations Centre (SOCDocument10 pagesGuide to Procuring a Security Operations Centre (SOCep230842No ratings yet
- SOC SIEM Use CasesDocument9 pagesSOC SIEM Use Casesjawwad joeNo ratings yet
- Protect Sensitive Data with DLP SolutionsDocument2 pagesProtect Sensitive Data with DLP Solutionsamitdhawan1No ratings yet
- Cyber SecurityDocument11 pagesCyber SecurityGM RajputNo ratings yet
- Top 15 Indicators of CompromiseDocument7 pagesTop 15 Indicators of CompromisenandaanujNo ratings yet
- Roadmap to Creating a World-Class Security Operations CenterDocument1 pageRoadmap to Creating a World-Class Security Operations CenterRoot100% (1)
- Cloud Security Handbook for Architects: Practical Strategies and Solutions for Architecting Enterprise Cloud Security using SECaaS and DevSecOps (English Edition)From EverandCloud Security Handbook for Architects: Practical Strategies and Solutions for Architecting Enterprise Cloud Security using SECaaS and DevSecOps (English Edition)No ratings yet
- Ebook - Hack - Discovery NmapDocument16 pagesEbook - Hack - Discovery Nmapapi-26021296100% (3)
- CIS Security Metrics-Quick Start Guide v1.0.0 PDFDocument18 pagesCIS Security Metrics-Quick Start Guide v1.0.0 PDFCarolus GazaNo ratings yet
- CIS Red Hat Enterprise Linux 7 Benchmark v2.2.0Document386 pagesCIS Red Hat Enterprise Linux 7 Benchmark v2.2.0Sandro MeloNo ratings yet
- CIS Security Metrics v1.1.0Document175 pagesCIS Security Metrics v1.1.0dohungthuanNo ratings yet
- CRITICAL LOG REVIEW CHECKLISTDocument1 pageCRITICAL LOG REVIEW CHECKLISTviny2010No ratings yet
- CIS Security Metrics v1.1.0Document175 pagesCIS Security Metrics v1.1.0dohungthuanNo ratings yet
- CRITICAL LOG REVIEW CHECKLISTDocument1 pageCRITICAL LOG REVIEW CHECKLISTviny2010No ratings yet
- ISMS Implementation - ISO-27003 PDFDocument22 pagesISMS Implementation - ISO-27003 PDFprakashtNo ratings yet
- RatioDocument46 pagesRatioGagan BossNo ratings yet
- Database Technology QuestionsDocument18 pagesDatabase Technology QuestionsShenbakesh KishoreNo ratings yet
- WebbyDocument12 pagesWebbyapi-327832679No ratings yet
- Configuration For NWDI Integration Into CTSDocument18 pagesConfiguration For NWDI Integration Into CTSBee NuttakornNo ratings yet
- Types of Computers and SoftwareDocument2 pagesTypes of Computers and SoftwareMatrixNo ratings yet
- Visio-1 AVR UC History and FeaturesDocument2 pagesVisio-1 AVR UC History and FeaturesAndrs AlvearNo ratings yet
- Gandhinagar Institute of Technology Mathematics & Humanities Department Discrete Mathematics (3140708) Set TheoryDocument10 pagesGandhinagar Institute of Technology Mathematics & Humanities Department Discrete Mathematics (3140708) Set Theoryshah mananNo ratings yet
- Burner Management System SpecificationDocument30 pagesBurner Management System SpecificationAndrew OnymousNo ratings yet
- Calc 3 Lecture Notes Section 12.3 1 of 6Document6 pagesCalc 3 Lecture Notes Section 12.3 1 of 6AhmadMoaazNo ratings yet
- Lakes Aermod View Release NotesDocument79 pagesLakes Aermod View Release NotesJuan Sebastian PinchaoNo ratings yet
- PressedDocument23 pagesPressedAbid LashariNo ratings yet
- Translation Practice PortfolioDocument25 pagesTranslation Practice PortfoliolaifkaifNo ratings yet
- Genre-Based Instruction OverviewDocument16 pagesGenre-Based Instruction OverviewZaenul WafaNo ratings yet
- Dashboard - Reveal Math, Grade 4 - McGraw HillDocument1 pageDashboard - Reveal Math, Grade 4 - McGraw HillTijjani ShehuNo ratings yet
- Tricks to handle windows shortcutsDocument15 pagesTricks to handle windows shortcutsshivamtruthNo ratings yet
- Bloom's TaxonomyDocument2 pagesBloom's TaxonomyJoshua PelagioNo ratings yet
- A Bibliography of Fieldwork in The Ethnography of CommunicationDocument11 pagesA Bibliography of Fieldwork in The Ethnography of CommunicationBlazsNo ratings yet
- Kusum - 11th LotDocument32 pagesKusum - 11th Lotsunil100% (1)
- Document 3Document1 pageDocument 3zoeijfoizjefNo ratings yet
- Tarea de Ingles 1Document12 pagesTarea de Ingles 1Antonio DelgadoNo ratings yet
- An English Translation of The Satyarth Prakash by Swami Dayananda SarasvatiDocument594 pagesAn English Translation of The Satyarth Prakash by Swami Dayananda Sarasvatinarayanbehera2014100% (3)
- CN Practical FileDocument17 pagesCN Practical FileDeepanshu PunjNo ratings yet
- Unlock Hidden Menu in Phoenix BIOS Setup Menu TutorialDocument10 pagesUnlock Hidden Menu in Phoenix BIOS Setup Menu TutorialSuper-Senior Pranksters100% (1)
- Man Applications ProgrammingDocument51 pagesMan Applications ProgrammingVicente FuentesNo ratings yet
- DLL Templates - 10 - W2Document5 pagesDLL Templates - 10 - W2Patrick PelicanoNo ratings yet
- Analytical ReasoningDocument7 pagesAnalytical ReasoningMandeep KhatoniarNo ratings yet
- INOSLOBAN-MARAWOY INTEGRATED SPEECH ACTDocument38 pagesINOSLOBAN-MARAWOY INTEGRATED SPEECH ACTSol Vińas De GuzmanNo ratings yet
- Unit 3 Standard Grammar: 1 2 3 4 5 A B C D eDocument1 pageUnit 3 Standard Grammar: 1 2 3 4 5 A B C D emehmet emin ulusoyNo ratings yet
- Activity IIDocument11 pagesActivity IITomás SaavedraNo ratings yet
- Song ListDocument180 pagesSong Listksraghavan2000No ratings yet