Professional Documents
Culture Documents
BestPractices InformationSecurity
Uploaded by
dmuscharOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
BestPractices InformationSecurity
Uploaded by
dmuscharCopyright:
Available Formats
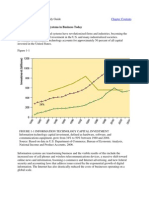
Benchmark Results
Best Practices for Managing Information Security
Key Finding
Organizations with Chief Information Security Officers are posting much better results, including: - Higher revenues, profits, and retained customers - Significant reductions in financial exposure from data loss and theft - Higher levels of business productivity from IT - 50 percent less being spent on audit
Some organizational structures and strategies yield better results
Organizations managing the information security function with a risk management and quality assurance focus deliver much better results. The differences are reflected in better retention of customers, as well as larger revenues and profits. Better business results are matched by much lower losses or thefts or customer and sensitive data, accompanied by lower financial exposure from these events. Moreover, the differences in outcomes are accompanied by fewer problems with audit, much lower expenses for audit, and less business downtime related to failures and disruptions occurring in IT.
Organizational structure
The outcomes being experienced by organizations also reflect significant differences in how the information security and assurance function is organized, managed and operated by organizations. Those experiencing the best outcomes manage the information security function through a CISO, who reports to a Chief Risk Officer CRO), a Chief Compliance Officer (CCO), the senior leader of IT assurance or the Chief Information Officer (CIO) Most organizations posting normal results manage the information security function through a CSO or a manager of IT operations who reports to either the senior leader of IT operations or a CIO. Organizations experiencing the worst outcomes manage information security through a systems or network administrator who reports to a manager or director of IT operations, or the senior leader of IT operations.
Coverage
The findings covered by the benchmark report, Best Practices for Managing Information Security, are based on outcomes being experienced by organizations. The outcomes benchmarked include customer retention rates, revenue, profit, data loss and theft, business downtime due to IT failures
IT POLICY
COMPLIANCE
GROUP
FEBRUARY 2010
and disruptions, regulatory audit deficiency corrections needed in IT to pass audit and spend on audit. Management structures for information security are accompanied by differences in how organizations establish and manage information security objectives, manage the information security function and manage day-to-day operations, with detailed coverage of management and operational activities. The report also covers the role of standardized procedures and the specialization of labor, the impact of automation, reporting, quality improvement programs and where the information security function reports in organizations.
About the Research
The benchmark findings contained in the report are from research conducted between late 2008 and late 2009 with 809 organizations, primarily within the United States. Although the findings in the report are representative of outcomes and management practices within North America, the results and practices mirror others obtained from research conducted with respondents in organizations in Asia, Europe, Latin America, the Middle East and the Pacific Rim. A full copy of the report can be obtained from the IT Policy Compliance Group website: www.itpolicycompliance.com There is no charge for reports and reuse privileges can be found on the website.
About IT Policy Compliance Group
The IT Policy Compliance Group is a member-advised research consortium focused on identifying what is working to produce better outcomes from fact-based benchmarks. The Group is focused on assisting IT, IT audit, internal audit, risk management, legal and compliance professionals.
Charter members of the Group include Computer Security Institute, The Institute of Internal Audit, ISACA, IT Governance Institute, Protiviti and Symantec Corporation.
MAY 2008 IT POLICY COMPLIANCE GROUP FEBRUARY 2010
You might also like
- Auditing Information Systems: Enhancing Performance of the EnterpriseFrom EverandAuditing Information Systems: Enhancing Performance of the EnterpriseNo ratings yet
- Best Practices For Managing Information SecurityDocument22 pagesBest Practices For Managing Information SecurityNikhil AggarwalNo ratings yet
- AUDIT and CONTROLSDocument2 pagesAUDIT and CONTROLSAple MancaoNo ratings yet
- Reviewing IT in Due Diligence: Are you buying an IT asset or liabilityFrom EverandReviewing IT in Due Diligence: Are you buying an IT asset or liabilityNo ratings yet
- B-Guidance For Best Practices in Information Security and It Audit-September 2009 or 2875202.en-UsDocument28 pagesB-Guidance For Best Practices in Information Security and It Audit-September 2009 or 2875202.en-UsSaid SakrNo ratings yet
- It Sec Audit ChecklistDocument38 pagesIt Sec Audit Checklistbrian1mugadzaNo ratings yet
- 2012 TTI WhitepaperDocument19 pages2012 TTI WhitepaperpinkoskiNo ratings yet
- Audit LessonsDocument87 pagesAudit Lessonscalamnojeffrey29No ratings yet
- Risk Management: by Dr. Selasi OcanseyDocument30 pagesRisk Management: by Dr. Selasi OcanseyHannett WoodNo ratings yet
- Week 3 Cis AssDocument4 pagesWeek 3 Cis AssKatrina PaquizNo ratings yet
- So You Want To Be An IT AuditorDocument4 pagesSo You Want To Be An IT Auditordiqyst33251No ratings yet
- Assignment No:4: Information Systems Helping in Better Corporate GovernanceDocument9 pagesAssignment No:4: Information Systems Helping in Better Corporate GovernanceTonmoy BorahNo ratings yet
- Information Security Governance-Top Actions For Security ManagersDocument28 pagesInformation Security Governance-Top Actions For Security ManagersM Luthfi AnshoriNo ratings yet
- CISA Domain 2 QuestionsDocument14 pagesCISA Domain 2 QuestionseliNo ratings yet
- SOX 404 & IT Controls: IT Control Recommendations For Small and Mid-Size Companies byDocument21 pagesSOX 404 & IT Controls: IT Control Recommendations For Small and Mid-Size Companies byDeepthi Suresh100% (1)
- Guidance For Best Practices in Information Security and IT Audit (PDFDrive) PDFDocument28 pagesGuidance For Best Practices in Information Security and IT Audit (PDFDrive) PDFEnvisage123No ratings yet
- COBITDocument25 pagesCOBITMaxwell MabhikwaNo ratings yet
- Week 5 Chapter DiscussionDocument5 pagesWeek 5 Chapter DiscussionPraveen JairamNo ratings yet
- Sox Octave FinalDocument11 pagesSox Octave FinalErick MorenoNo ratings yet
- Sir Vic ITSM CriticalDocument11 pagesSir Vic ITSM Criticaltricia quilangNo ratings yet
- What Is IT Governance? A Formal Way To Align IT & Business StrategyDocument4 pagesWhat Is IT Governance? A Formal Way To Align IT & Business StrategyHamidur BabuNo ratings yet
- Avoiding 7 Common Mistakes of IT Security Compliance: GuideDocument7 pagesAvoiding 7 Common Mistakes of IT Security Compliance: Guiderana_dipaNo ratings yet
- 49 NB Management Briefing On Privacy MetricsDocument3 pages49 NB Management Briefing On Privacy Metricszhiqunzeng1No ratings yet
- Information Security About The Industry and CompanyDocument7 pagesInformation Security About The Industry and CompanyVinitNo ratings yet
- MIS CHP 1Document12 pagesMIS CHP 1Shambhavi Verenkar HindeNo ratings yet
- IT Audit ch01Document4 pagesIT Audit ch01hermione_crisNo ratings yet
- Chapter 3 OteroDocument43 pagesChapter 3 OteromurdiawatiNo ratings yet
- 2.4 Information Technology Monitoring and Assurance Practices For Board and Senior ManagementDocument6 pages2.4 Information Technology Monitoring and Assurance Practices For Board and Senior ManagementJonathan MdsNo ratings yet
- The Role of Information Systems in Business TodayDocument43 pagesThe Role of Information Systems in Business TodaySohail HaqueNo ratings yet
- IT Governance NotesDocument21 pagesIT Governance NotesFeisal MohamedNo ratings yet
- Information Technology General ControlDocument7 pagesInformation Technology General Controleie_subir_09No ratings yet
- Best Practices in IT Portfolio ManagementDocument19 pagesBest Practices in IT Portfolio Managementaskvishnu7112No ratings yet
- ACCN 301 - Group - 5AIS2Document11 pagesACCN 301 - Group - 5AIS2Mcdonald MutsvangaNo ratings yet
- Data GovernanceDocument22 pagesData Governanceganesh100% (2)
- IT GovernanceDocument3 pagesIT GovernanceTochukwuNo ratings yet
- Comp. Lesson 7Document18 pagesComp. Lesson 7Ryan Prado AndayaNo ratings yet
- Mobilizing A Cyber Risk StrategyDocument13 pagesMobilizing A Cyber Risk StrategyMuhamad PanjiNo ratings yet
- Trends in IT Performance ManagementDocument5 pagesTrends in IT Performance Managementlgg1960789No ratings yet
- UATDocument3 pagesUATAngelica DeniseNo ratings yet
- Tharun-Research PaprDocument8 pagesTharun-Research PaprAnuja ShuklaNo ratings yet
- Session 6 - IT GovernanceDocument42 pagesSession 6 - IT GovernanceDavid sangaNo ratings yet
- Governance - ITDocument16 pagesGovernance - ITsuraniNo ratings yet
- ISP GovernanceDocument12 pagesISP GovernanceFrancis Leo Gunseilan100% (1)
- Ref 6 - What Is IT Governance - A Formal Way To Align IT - Business Strategy - CIODocument4 pagesRef 6 - What Is IT Governance - A Formal Way To Align IT - Business Strategy - CIOTowhidul IslamNo ratings yet
- Paquiz, Lesson 1 Key TakeawaysDocument2 pagesPaquiz, Lesson 1 Key TakeawaysKatrina PaquizNo ratings yet
- Information System and Control Audit For Ca FinalDocument157 pagesInformation System and Control Audit For Ca FinalKhundrakpam SatyabartaNo ratings yet
- Solution Manual Chapter One: Information & Information Technology AssuranceDocument109 pagesSolution Manual Chapter One: Information & Information Technology AssuranceGwen Sula LacanilaoNo ratings yet
- Summary Report of Information Technology Audit FindingsDocument32 pagesSummary Report of Information Technology Audit Findingshameed77No ratings yet
- Jopdf0705 Turning A SecurityDocument7 pagesJopdf0705 Turning A SecurityJerome B. AgliamNo ratings yet
- Chapter 7 - Control and Accounting Information SystemsDocument3 pagesChapter 7 - Control and Accounting Information SystemsLouBel100% (5)
- IM - Executive RIM Whitepaper - Gens and Associates - V - Fall 2012 EditionDocument19 pagesIM - Executive RIM Whitepaper - Gens and Associates - V - Fall 2012 Editionpedrovsky702No ratings yet
- Supplying Risk Management SolutionsDocument11 pagesSupplying Risk Management SolutionsArtieKNo ratings yet
- It Risk ManagementDocument34 pagesIt Risk Managementranzel789No ratings yet
- Trusted: Identity Management: A Business Imperative in Building A Trusted EnterpriseDocument10 pagesTrusted: Identity Management: A Business Imperative in Building A Trusted EnterpriseJeffNo ratings yet
- The Significance of IT Security Management & Risk AssessmentDocument30 pagesThe Significance of IT Security Management & Risk AssessmentBradley Susser100% (1)
- Chapter 6 Risk ManagementDocument11 pagesChapter 6 Risk Managementricojr.pagalanNo ratings yet
- Holistic IT GovernanceDocument13 pagesHolistic IT GovernanceWannachin Chinchaipong100% (2)
- Gtag No 01: IT ControlsDocument59 pagesGtag No 01: IT Controlsmarmah_hadiNo ratings yet
- Information Technology ControlsDocument59 pagesInformation Technology ControlszomozoraxNo ratings yet
- Indoco Annual Report FY16Document160 pagesIndoco Annual Report FY16Ishaan MittalNo ratings yet
- Ogutu - The Role of National Housing Corporation in The Provision of Housing in KenyaDocument95 pagesOgutu - The Role of National Housing Corporation in The Provision of Housing in KenyaboneylouNo ratings yet
- Communications Plan and TemplateDocument6 pagesCommunications Plan and TemplateBrittani Bell100% (1)
- (Please Write The Name That Appears On Your Card) : PNB Credit Card Rewards Redemption FormDocument1 page(Please Write The Name That Appears On Your Card) : PNB Credit Card Rewards Redemption FormJane PulmaNo ratings yet
- Jack Monroe On Twitter - Woke Up This Morning To The RadioDocument9 pagesJack Monroe On Twitter - Woke Up This Morning To The RadioToni PrugNo ratings yet
- Sap Fico Training: by Rajeev KumarDocument115 pagesSap Fico Training: by Rajeev KumarRajeev Kumar90% (10)
- Ifc IdaDocument10 pagesIfc IdaShyama KakkatNo ratings yet
- Air India (HRM) - Invitation Letter - 2 PDFDocument2 pagesAir India (HRM) - Invitation Letter - 2 PDFNilesh Sanap100% (2)
- High Dividend Yield StocksDocument3 pagesHigh Dividend Yield StockskaizenlifeNo ratings yet
- Ireland Soaking Tub Prices September 2017Document2 pagesIreland Soaking Tub Prices September 2017DerekSashaNo ratings yet
- Cost Management Process in Construction Industry: Hardeep KumbhaniDocument8 pagesCost Management Process in Construction Industry: Hardeep KumbhaniGuts GriffithNo ratings yet
- Project On SunsilkDocument11 pagesProject On Sunsilktanya sethiNo ratings yet
- Root Cause AnalysisDocument45 pagesRoot Cause AnalysisEssalim HakimNo ratings yet
- Leading Through Digital Disruption AmazonDocument13 pagesLeading Through Digital Disruption AmazonMaham Tariq0% (1)
- Customer Management and Organizational Performance of Banking Sector - A Case Study of Commercial Bank of Ethiopia Haramaya Branch and Harar BranchesDocument10 pagesCustomer Management and Organizational Performance of Banking Sector - A Case Study of Commercial Bank of Ethiopia Haramaya Branch and Harar BranchesAlexander DeckerNo ratings yet
- Startup Fundraising 101Document8 pagesStartup Fundraising 101CrowdfundInsiderNo ratings yet
- Hidden-City Ticketing The Cause and ImpactDocument27 pagesHidden-City Ticketing The Cause and ImpactPavan KethavathNo ratings yet
- Shiny Hill Farms Case StudyDocument2 pagesShiny Hill Farms Case StudyDana WilliamsNo ratings yet
- Retail and Franchise AssignmentDocument8 pagesRetail and Franchise AssignmentAkshay Raturi100% (1)
- Week 4: The Service EncounterDocument20 pagesWeek 4: The Service EncounterAyu Anggraeni DwijayantiNo ratings yet
- Literature Review Effects of Demonetization On Retail OutletsDocument18 pagesLiterature Review Effects of Demonetization On Retail OutletsAniket RoyNo ratings yet
- Pepsi Cola Vs NLRCDocument10 pagesPepsi Cola Vs NLRCAnonymous wD8hMIPxJNo ratings yet
- D15 Hybrid P1 QPDocument6 pagesD15 Hybrid P1 QPShaameswary AnnadoraiNo ratings yet
- Reading Comprehension Read The Article Below and Then Answer The Questions That FollowDocument4 pagesReading Comprehension Read The Article Below and Then Answer The Questions That FollowRaluca Igna50% (2)
- Feedback Industry Report BicycleDocument24 pagesFeedback Industry Report BicycleajaxorNo ratings yet
- Purpose of AuditDocument5 pagesPurpose of Auditannisa radiNo ratings yet
- All India GST JurisdictionDocument2 pagesAll India GST JurisdictionCafe 31No ratings yet
- Banglore Institute of TechnologyDocument5 pagesBanglore Institute of TechnologyAdmission DetailsNo ratings yet
- Huimfisllfia: 18 July - August 2006 Aba Bank MarkehngDocument8 pagesHuimfisllfia: 18 July - August 2006 Aba Bank MarkehngGhumonto SafiurNo ratings yet
- Riphah International University: Crescent Standard Investment Bank Limited (Case Study)Document4 pagesRiphah International University: Crescent Standard Investment Bank Limited (Case Study)bilal mustafaNo ratings yet
- Facing Cyber Threats Head On: Protecting Yourself and Your BusinessFrom EverandFacing Cyber Threats Head On: Protecting Yourself and Your BusinessRating: 4.5 out of 5 stars4.5/5 (27)
- The Internet Con: How to Seize the Means of ComputationFrom EverandThe Internet Con: How to Seize the Means of ComputationRating: 5 out of 5 stars5/5 (6)
- Tor Darknet Bundle (5 in 1): Master the Art of InvisibilityFrom EverandTor Darknet Bundle (5 in 1): Master the Art of InvisibilityRating: 4.5 out of 5 stars4.5/5 (5)
- Transformational Security Awareness: What Neuroscientists, Storytellers, and Marketers Can Teach Us About Driving Secure BehaviorsFrom EverandTransformational Security Awareness: What Neuroscientists, Storytellers, and Marketers Can Teach Us About Driving Secure BehaviorsRating: 5 out of 5 stars5/5 (2)
- Hacking With Kali Linux : A Comprehensive, Step-By-Step Beginner's Guide to Learn Ethical Hacking With Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingFrom EverandHacking With Kali Linux : A Comprehensive, Step-By-Step Beginner's Guide to Learn Ethical Hacking With Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingRating: 4.5 out of 5 stars4.5/5 (9)
- Digital Forensics and Incident Response - Second Edition: Incident response techniques and procedures to respond to modern cyber threats, 2nd EditionFrom EverandDigital Forensics and Incident Response - Second Edition: Incident response techniques and procedures to respond to modern cyber threats, 2nd EditionNo ratings yet
- Practical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTFrom EverandPractical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTNo ratings yet
- Cyber Security: How to Protect Your Digital Life, Avoid Identity Theft, Prevent Extortion, and Secure Your Social Privacy in 2020 and beyondFrom EverandCyber Security: How to Protect Your Digital Life, Avoid Identity Theft, Prevent Extortion, and Secure Your Social Privacy in 2020 and beyondRating: 4.5 out of 5 stars4.5/5 (14)
- Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNFrom EverandSet Up Your Own IPsec VPN, OpenVPN and WireGuard Server: Build Your Own VPNRating: 5 out of 5 stars5/5 (1)
- 200+ Ways to Protect Your Privacy: Simple Ways to Prevent Hacks and Protect Your Privacy--On and OfflineFrom Everand200+ Ways to Protect Your Privacy: Simple Ways to Prevent Hacks and Protect Your Privacy--On and OfflineNo ratings yet
- Cybersecurity for Beginners : Learn the Fundamentals of Cybersecurity in an Easy, Step-by-Step Guide: 1From EverandCybersecurity for Beginners : Learn the Fundamentals of Cybersecurity in an Easy, Step-by-Step Guide: 1No ratings yet
- An Ultimate Guide to Kali Linux for BeginnersFrom EverandAn Ultimate Guide to Kali Linux for BeginnersRating: 3.5 out of 5 stars3.5/5 (4)
- Hands-On AWS Penetration Testing with Kali Linux: Set up a virtual lab and pentest major AWS services, including EC2, S3, Lambda, and CloudFormationFrom EverandHands-On AWS Penetration Testing with Kali Linux: Set up a virtual lab and pentest major AWS services, including EC2, S3, Lambda, and CloudFormationNo ratings yet
- Ultimate GDPR Practitioner Guide (2nd Edition): Demystifying Privacy & Data ProtectionFrom EverandUltimate GDPR Practitioner Guide (2nd Edition): Demystifying Privacy & Data ProtectionNo ratings yet
- Risk Management and Information Systems ControlFrom EverandRisk Management and Information Systems ControlRating: 5 out of 5 stars5/5 (1)
- CYBERSECURITY FOR BEGINNERS: HOW TO DEFEND AGAINST HACKERS & MALWAREFrom EverandCYBERSECURITY FOR BEGINNERS: HOW TO DEFEND AGAINST HACKERS & MALWARERating: 3.5 out of 5 stars3.5/5 (6)
- SRS - How to build a Pen Test and Hacking PlatformFrom EverandSRS - How to build a Pen Test and Hacking PlatformRating: 2 out of 5 stars2/5 (1)
- CCSP Certified Cloud Security Professional A Step by Step Study Guide to Ace the ExamFrom EverandCCSP Certified Cloud Security Professional A Step by Step Study Guide to Ace the ExamNo ratings yet